At the last The Standoff, experts from the PT Expert Security Center , in this case representing the team of the global SOC of the cyber polygon, monitored the actions of the teams of attackers and defenders of the digital copy of the FF metropolis, the confrontation took place in real time and lasted 123 hours. Earlier, we wrote about how the global SOC monitored everything that was happening in the infrastructure of the virtual city, how the malware detection department caught and investigated the Trojans of "redimers" using the PT Sandbox sandbox and how we monitoredbehind all the web resources of the cyber polygon using PT Application Firewall. Now let's talk about the security of technological networks of virtual city objects and the results of monitoring carried out using the in-depth analysis of technological traffic PT Industrial Security Incident Manager (PT ISIM).
In this article, we will talk about what attacks on the technological segment of the network of city facilities were detected by the system, and note how these threats correspond to the real level of security of industrial systems.
What was attacked at The Standoff
The model of the city on The Standoff cyber polygon included digital copies of infrastructure facilities controlled by real SCADA systems and PLCs: the exact same ones are installed in real enterprises. Here are the elements and objects that may have been attacked by competitors from read teams:
control systems for switches and barriers on the railway,
baggage tape at the airport,
telescopic gangway at the airport,
crane in the seaport,
HVAC business center,
a ferris wheel in an amusement park,
traffic lights in the business center,
street lighting,
substation (electricity of the whole city),
gate valves of an automated gas distribution station,
CHP turbine,
fire control cabinet for CHP,
wind turbines at a power plant,
production control systems at a petrochemical plant,
oil production control systems.
, , , SOC The Standoff PT ISIM.
Back2oaz odeby Nuft, . red teams SCADA , — . - , .
:
RDP 172.20.61.2 SCADA 172.20.22.11 ( 01:30). SCADA-.
CIP SCADA 172.20.22.11 172.20.23.11 (09:02). ( , : 0x349, 0x68 (SFC Forces), 0x6b (SymbolObject)). , .
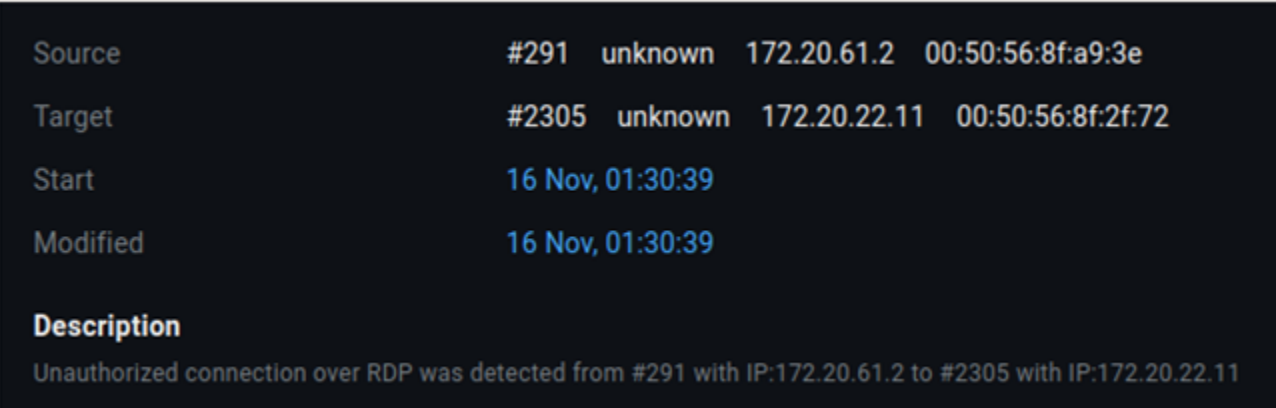


CIP. , , . , , MaxPatrol SIEM, PT Sandbox, PT NAD PT ISIM. , . , : SCADA- .
, . , , , . , , , .
FF 25 Hours, . Back2oaz, SCADA . — , .
:
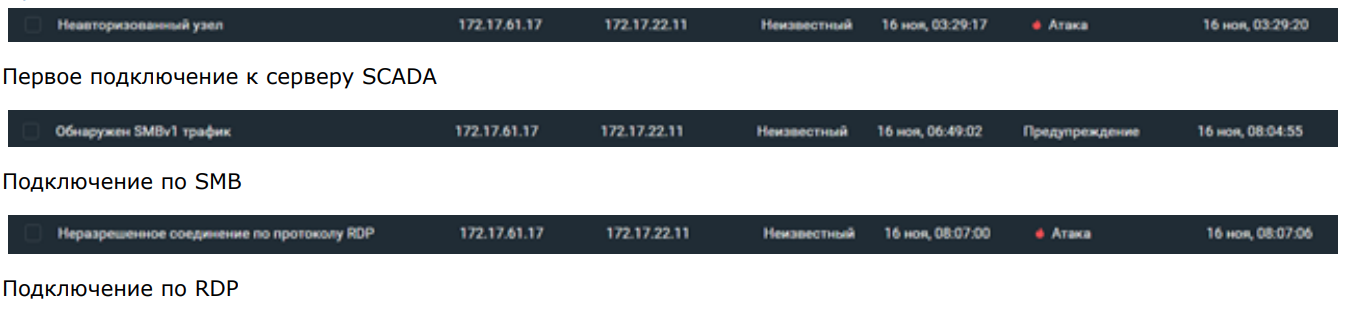
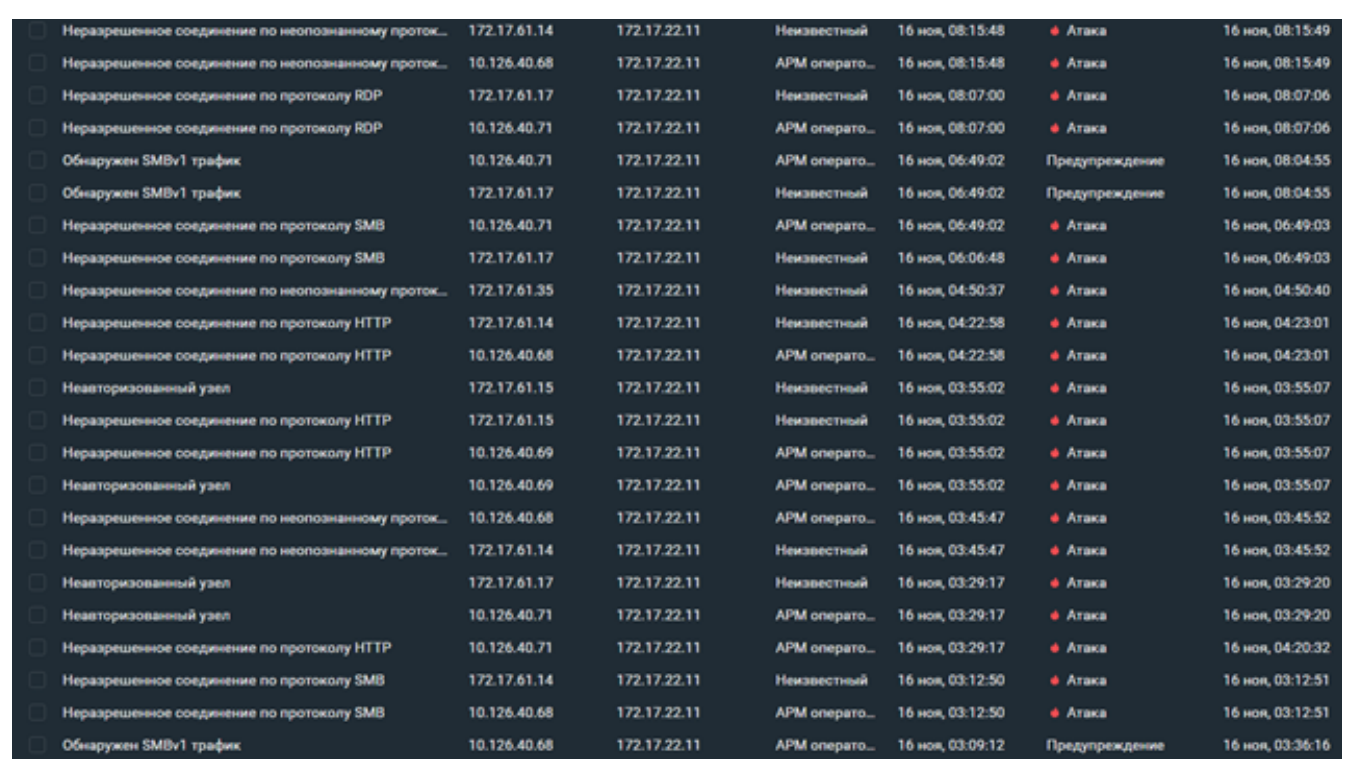
TCP 172.17.61.17 SCADA 172.17.22.11 (03:29). , .
SMB 172.17.61.17 SCADA 172.17.22.11 (06:06). . , .
RDP 172.17.61.17 SCADA 172.17.22.11 (08:07). SCADA-.
, SCADA 172.17.22.11 172.17.23.11 (08:25). SCADA — . , . SCADA- , . , NTA ( , PT ISIM proView Sensor).
PT ISIM.
, . , . , , MaxPatrol SIEM, PT Sandbox, PT NAD PT ISIM. , . , , , . , . , .
Nuft — . Back2oaz. SCADA RDP, , - — . , , , , , .
:
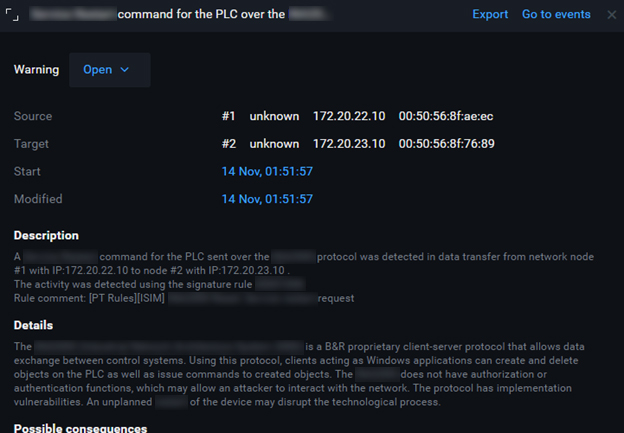
RDP 172.20.61.17 SCADA 172.20.22.10 (19:30). SCADA-.
, SCADA 172.20.22.10 172.20.23.10 (01:51 ). , . . , , .
PT ISIM .



The Standoff, , , . , . , . , . — SIEM-, ; .
: , Positive Technologies