TL; DR Imagine what could happen if the country code top level domain (ccTLD) of a sovereign state falls into the wrong hands. However, I ( @Almroot ) bought the domain name that is listed for NS delegation in the ccTLD of the Democratic Republic of Congo (
.cd
), and temporarily took over 50% of all DNS traffic for that TLD. In my place, there could be an attacker who would use this opportunity for MITM or other abuses.

Introduction
A week before Christmas, I decided to analyze all NS records for all TLDs in the world. And one thing caught my attention. The domain
scpt-network.com
had the EPP status code “redemptionPeriod”. This means that the owner did not transfer money for the domain renewal. If the owner continues to ignore the payment, then his property will be taken away from him - and the domain will go on sale.
Quite a problematic situation, since it is included in the list of NS servers that manage the zone
.cd
:
almroot@x:~$ dig NS +trace cd | grep "cd."
cd. 172800 IN NS ns-root-5.scpt-network.com.
cd. 172800 IN NS igubu.saix.net.
cd. 172800 IN NS sangoma.saix.net.
cd. 172800 IN NS ns-root-2.scpt-network.com.
cd. 172800 IN NS sabela.saix.net.
cd. 172800 IN NS ns-root-1.scpt-network.com.
I decided to write a bash script just in case that would notify me whenever the EPP status changes.
To my surprise, about a week later, I received a notification that the domain had moved to the “pendingDelete” status.
I was aware of the gravity of the situation . The domain name will soon be put up for sale for everyone, that is, anyone can easily take over the name server
.cd
.
I changed the script - and began to ping the registrar every minute for further status changes.
In the evening of December 30, a notification came. I opened my laptop and bought a domain name to prevent it from falling into the wrong hands.

Since there were three more delegation records left on SAIX (South African Internet eXchange, South African traffic exchange point ), the country code remained operational (although the speed of resolving any domains decreased slightly).
Once
scpt-network.com
I got it, I could configure any subdomain at my discretion. For example, if you create a new subdomain
ns-root-1
with an A record that points to the IP address 1.3.3.7, then DNS queries for the .cd zone will go to this address 1.3.3.7. Any DNS response to these queries will be accepted as legitimate.

If you do not respond to the request, the subscriber will time out with the SERVFAIL status code. This is good, because when it receives such a code, it will try to contact any other nameserver (NS record) for that zone. This will eventually end up in one of the normal SAIX records and be appropriately redirected to the correct destination.
Potential Impact
The seizure of the national top-level domain of a sovereign state has serious negative consequences, especially if this domain falls into the hands of cybercriminals or a foreign adversary. The Democratic Republic of the Congo (DRC) is a rather big country. This is approximately 90 million people , not to mention the numerous international companies and organizations operating in this domain zone.
Hijacking an entire country's DNS TLD record is rare, but not new. For example, ten years ago cybercriminals took over the domain of the former Soviet Union (.su), and in 2015, the Vietnamese sites Lenovo and Google (.vn) were also victims of DNS hijacking.... Redirecting DNS traffic from legitimate .cd sites to a phishing site is one of the obvious opportunities for abuse, but there are others:
- Passive interception of DNS traffic
- for surveillance or exfiltration of data
- Creating new domain names "out of thin air"
- imagine the possibilities for quickly generating new domain names with the botnet switching to new C&C servers every few minutes, so that no one has time to block them ( fast flux technique )
- Remote Code Execution (RCE) attacks on local networks
- victims will be companies that use WPAD (Automatic Proxy Configuration Protocol)
- Spoofed DNS responses to legitimate DNS queries
- completely hijacking root domains in a zone.cd
or conducting a DDoS attack.
For example, I could write an exploit to hijack a specific domain in a zone
.cd
. Imagine that for any NS requests to,
google.cd
I always return responses
ns-root-1.scpt-network.com
(instead of these four :)
[ns1,ns2,n3,ns4].google.com
. The subscriber will receive such a response, and will send any subsequent DNS requests to
ns-root-1.scpt-network.com
.
It also got me thinking: what if I answer all NS requests with a link to myself. Then, for any request that 1.3.3.7 responds to, all domain lookups will end up going to that link. And all subsequent network traffic will be redirected to 1.3.3.7, which can lead to a DDoS attack.
In fact, this will also affect the availability of the entire TLD, as 50% of the DNS responses will become incorrect. The strength of (both) DoS attacks can be increased by setting a high TTL in DNS responses.
Let's take it one step further. Let's say I'm specifically faking TXT records for the server
google.cd
. Using fake text files, I trick
the Let's Encrypt registrar's DNS-01 validation system into obtaining a valid certificate for
google.cd
, and then effectively hacking the SSL / TLS encrypted channel.
Since I can control the delegation of NS servers for any domain
.cd
and get valid certificatesthen I can conduct an MITM attack even if the victim is using SSL / TLS.
Translator's note. Some of the methods described are available to government agencies that control country code domains in their countries.
While Google implements various countermeasures against such abuses, it is safe to say that this does not apply to all root domains in the .cd zone. For more information on how CAs verify domain ownership, see BR 1.7.3 .
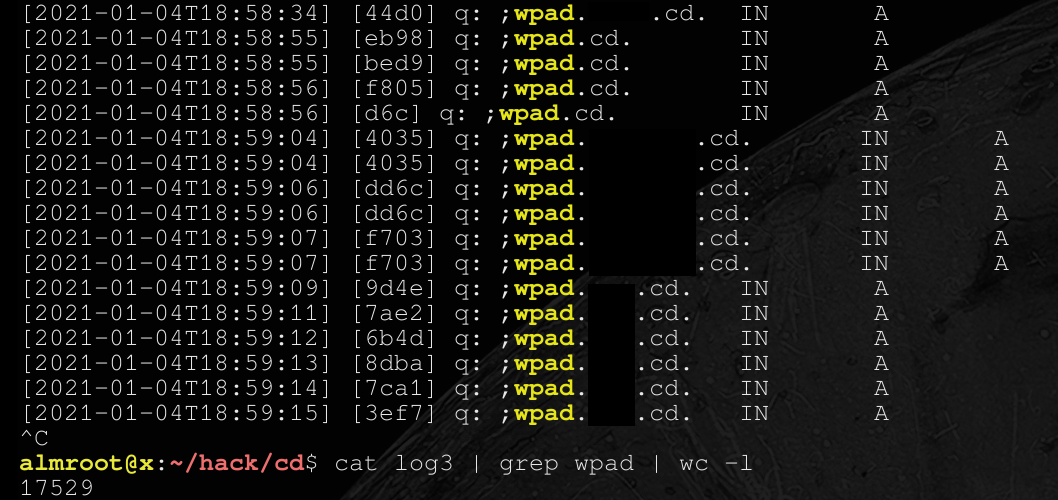
Last but not least, with privileged access to an upstream host with DNS control, I can break into company LANs(example in the screenshot below) that send DNS requests to WPAD - you can track their requests, fake responses and redirect the victim to download and execute a malicious proxy server configuration on JS . WPAD has a host of problems, including RCE vulnerabilities, according to hackers from the Project Zero team at Google.
Fixing the problem
On January 7, 2021, I contacted the administrative and technical contacts listed for the .cd zone on the IANA page . Initially, I wanted to transfer the domain to an operator
.cd
.
Although one of the contacts responded and referred me to a colleague, at the time of this writing, I have not received written confirmation that they fixed the problem. But soon the DNS traffic was redirected to scpt-network. net .
On January 8th, I also submitted a report on the Internet Bug Bounty to HackerOne, which offers rewards for responsible hacking of the Internet infrastructure.
Conclusion
DNS server hijacking is extremely negative, especially if the attacker has bad intentions. This vulnerability affects more than one site, subdomain, or one root domain. Any website can become a victim of phishing, MITM or DDoS
.cd
, including websites of large international companies, financial institutions and other organizations. And this is the second largest country in Africa and a popular domain zone.
At the time of this writing, I still own the domain name scpt-network.com although the delegation of NS requests from the .cd zone stopped around January 8, 2021 after I contacted them. I carried out this operation in order to prevent attackers from seizing the domain zone of the Democratic Republic of the Congo, when anyone could hijack the domain name of one of the servers that control the ccTLD. Fortunately, in this case, everything worked out.