
Since the invention of e-mail, phishing attacks have targeted individuals and organizations alike, becoming more sophisticated and disguised over time. A phishing attack is one of the most common methods used by hackers to infiltrate the accounts and networks of their victims. According to Symantec , every 2,000 email is a phishing email, which means there are around 135 million attacks every day.
And although phishing attacks are not uncommon for a long time, in times of crisis their number increases dramatically. Fraudsters are taking advantage of the chaos and confusion caused by recent events. At times like these, many expect letters from official sources such as expert organizations, insurance companies, or government agencies. This gives criminals an excellent opportunity to disguise their malicious mailings as emails from official sources. These seemingly harmless emails redirect users to fraudulent sites in order to trick them into entering confidential information.
What is phishing?
In simple terms, phishing is a tactic of sending fraudulent emails to trick recipients into clicking a malicious link or downloading an infected attachment in order to steal their personal information. These emails may look like messages from reputable sources: merchants, banks, or individuals or teams in your own organization, such as HR, your manager, or even the CEO.
If your employees cannot recognize the signs of phishing, your entire organization is at risk. According to Verizon research , the average time it took for the first victim of a large-scale phishing campaign to open a malicious email was 16 minutes, and it took twice as long to report a phishing campaign to the cyber security department - 33 minutes.
Considering that 91% of cybercrime starts with a successful phishing email , those 17 minutes can be a disaster for your company.

Phishing attack methods
As mentioned, most, if not all phishing attacks start with an email that looks like it was sent by a legitimate source, but the subsequent attack and penetration methods may vary. Some of the methods are quite simple and consist in tricking the user into clicking on a link and entering confidential information, while others are more sophisticated, for example, launching an executable file that imitates the real process and gains access to the victim's computer and network in order to invisibly launch malicious program.
Typically, a phishing attack uses several techniques to deceive a victim. For example, it is not uncommon for scammers to use link manipulation and website spoofing., which in combination gives their actions the maximum persuasiveness. The first thing you see when you receive a phishing email is a believable-looking link that leads to a frequently used and unsuspecting site like Facebook, Amazon, or YouTube, and a message urging you to follow that link for various reasons. These messages will prompt users to enter sensitive information, claiming that there is a problem with their account or order that needs to be resolved. This is where the next trick comes into play - website spoofing .
While at first glance, the link may look just like a legitimate website, say, "amazon.com", on closer inspection you can find minor inconsistencies or inconsistencies that reveal the true nature of the link. The creation of such fraudulent domains, similar in spelling to well-known sites, is called typesquatting . These malicious sites are as close as possible to real pages, and unsuspecting users can enter their credentials on them. Hackers are able to enter the stolen data on the real site.
Also, hackers often attach an unsuspecting file or add a link that, when clicked, will secretly download malicious software that will infiltrate the victim's system. These attacks often inject malwaremasquerading as a real executable file. Running in the background, such a program will roam the user's network in order to steal confidential information such as bank accounts, social security numbers, user credentials, and more. Sometimes, malware includes ransomware that sneaks through the victim's network, encrypting and moving sensitive data for ransom storage.
Types of phishing attacks
The most popular attack method among phishing scammers is to create the widest possible reach. They send out standard e-mails on behalf of well-known sites to as many recipients as possible, hoping that someone will fall for their tricks. This is an effective, but not the only way to hook the victim. Some cybercriminals use more precise methods to achieve their goals, such as spear phishing, clone phishing, and whaling .
Spear phishing and whaling
As with regular phishing attacks, targeted (targeted) phishing and whaling uses emails from trusted sources to trick victims. However, instead of mass mailing to multiple recipients, spear phishing targets specific individuals or impersonates a trusted person to steal credentials or information.
Similar to spear phishing, whaling (literally "whale hunting") is aimed at a specific high-ranking person . Rather than targeting a wider group like a department or team, attackers direct their inner captain Ahab to high-level targets - leaders and influencers - in hopes of hitting their white whale.
Whale hunters seek to impersonate senior management, such as the CEO, CFO, or HR manager, in order to convince members of the organization to disclose sensitive information of value to attackers.
For whaling to succeed, attackers must study their victim much better than regular phishing in order to look as authentic as possible. Attackers expect to use the authority they claim to be in order to convince employees or other executives not to check or question their requests.
During my work at the previous company, I also became a target for Wailing: a scammer posing as my CEO asked for his phone number so he could call me and ask for a service. Fortunately, there were many clear signs of fraud in the letter. The most obvious thing was that the CEO's office was just a few steps from my desk, so it could easily fit if he needed me!
Clone phishing
Clone phishing is not as ingenious as spear phishing or whaling, but it is no less effective. All the basic elements of a phishing scam are inherent in this attack method, but the difference is that instead of impersonating a user or organization with a specific request, attackers copy a real email that was previously sent by a legitimate organization . The hackers then use link manipulation to spoof the real link from the original email and redirect the victim to a fraudulent site. There, they trick users into entering credentials that attackers would use on a real site.
Examples of email scams
Scammers often fake official emails from retailers like Amazon or Walmart, claiming that the user needs to enter their credentials or payment information to complete an order. The links in the email will take you to a landing page that looks like a real one, where you can enter sensitive information.
With the development of e-commerce, as well as in the context of a pandemic, the number of online purchases has reached unprecedented proportions, which means that the scammers have more work. During the holidays, when everyone buys gifts in large quantities, the number of such scammers grows exponentially. Many people make so many purchases that they stop thinking and noticing that something is wrong with their order.
An example of a phishing scam that has gained traction in the 2020 holiday season is a fake email from Amazon informing customers to sign in to update billing information and order fulfillment address.

( Source )
Personally, I keep getting emails from Amazon about delivery, arrival dates, confirmations and more. If I didn’t know what to look for to identify phishing, I would have easily fallen for the tricks of scammers.
Anatomy of a phishing email
We have highlighted the most common elements inherent in phishing emails. Check out our full infographic to test your knowledge.
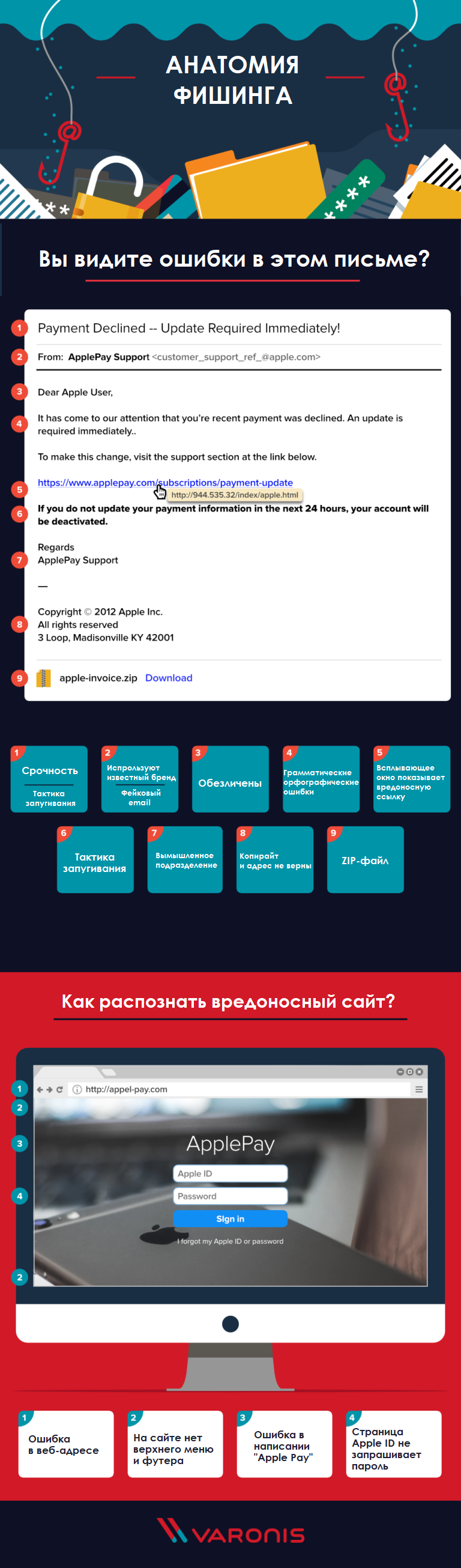
Topic
Phishing emails usually aim to create a sense of urgency and employ assertive language and intimidation tactics, starting with the subject line.
Sender / From field
Scammers will give the impression that the email was sent by an official from a well-known company , such as customer support. However, upon closer inspection, you can see that both the sender's name and the email address are fake and do not belong to this company.
Recipient / "To" field
Phishing emails are often impersonal , referring to the recipient as a "user" or "customer."
Body of the letter
As with the subject line, body copy often uses expressions that create a sense of urgency . They encourage the reader to act without thinking. Phishing emails also often contain both grammatical and punctuation errors .
Malicious link
A suspicious link is one of the main elements of phishing emails, their payload. These links are often shortened (using bit.ly or a similar service) or formatted to look like a real link from a real company and to match the message of a fake email.
Intimidation tactics
In addition to creating a sense of urgency, phishing emails often use intimidation tactics designed to cause readers to click on a malicious link out of anxiety or confusion .
Signature at the end of the letter
As with the greeting, the signature at the end of a phishing email is often impersonal - usually the generic name of the customer support team, not the name of the person, and no corresponding contact information.
Letter footer
The footer of phishing emails often contains clear signs of forgery, including an incorrect copyright date or an address that does not match the location of the real company.
Malicious site
Typically, clicking on a link in a phishing email will take you to a malicious site.
How to avoid falling victim to an attack
The best defense against phishing is knowledge . Phishing attackers tend to look as convincing as possible, but they can often be detected by telltale signs . Mandatory regular training in the basics of information security and social engineering is a great prevention tool to help your organization identify signs of malicious emails.
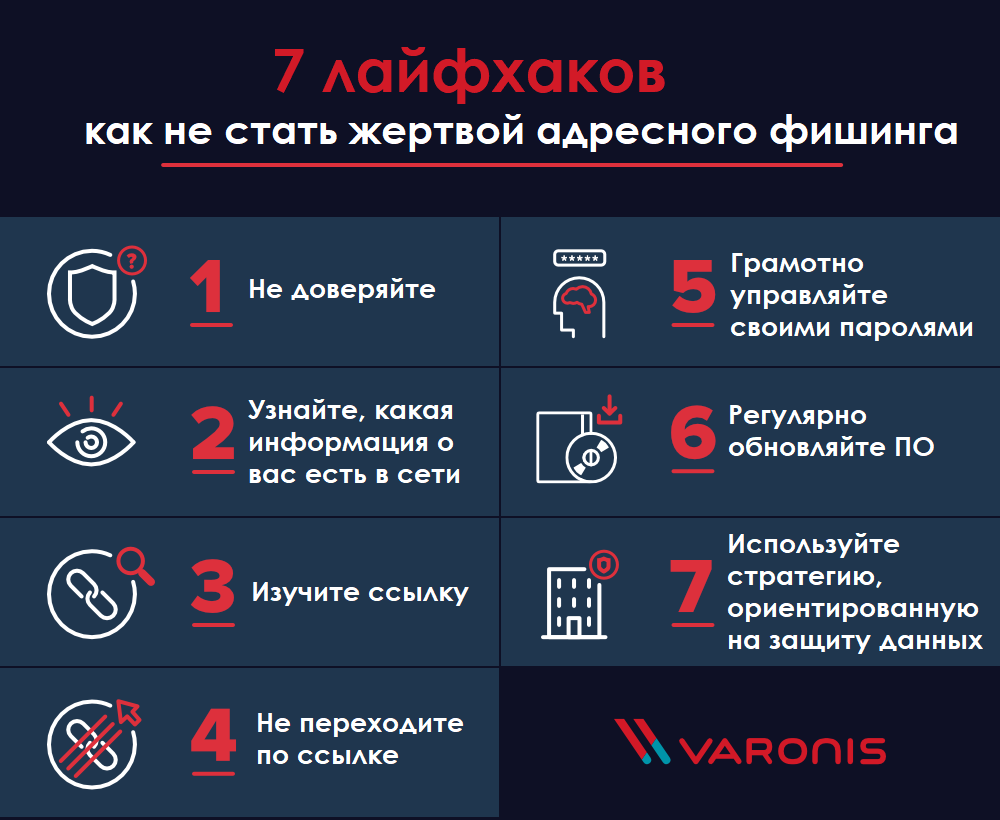
Here's what to look out for every time you receive an email asking you to click on a link, download a file, or provide your credentials, even if it seems like the email came from a trusted source:
If you have the slightest suspicion that the message you received is a phishing email, do not click on it or open any attachments. Instead, check it off and report it to those in charge. This could be your company's cybersecurity staff, company representatives whose email address is spoofed, or your email domain provider (e.g. Google, Microsoft, etc.).
Don't fall for tricks
Knowledge is power, especially when it comes to phishing protection. For the scammers' idea to be successful, you must fall for their tricks. Even if you consider yourself an expert in detecting phishing, you must be on your guard, because the danger lurks behind every link. As time goes on, phishing scams and malicious emails will become more sophisticated and difficult to distinguish from the real ones.
As long as our daily lives are closely connected with digital technologies and the Internet, hackers will always be around , trying to use innocent people for financial gain. The best way to stay safe and up to date is by continuing to research the most advanced forms of phishing scams.