Instead of a direct offer to participate in the carve-up of non-existent wealth, the victim is asked to send a postcard to a little girl. The scam happens somewhere deep in the correspondence process: it feels like spammers have learned what a sales funnel is. Experts also note the diversification of malicious activities, a target for mobile users and instant messengers. In one case, scammers offer not only to participate in the drawing of valuable prizes, but also to inform friends and acquaintances about the pseudo-lottery. In another, in order to receive "coronavirus compensation", they require installing a malicious application on a smartphone. As usual, the most advanced fraud is seen in potentially more lucrative attacks on corporate infrastructure.
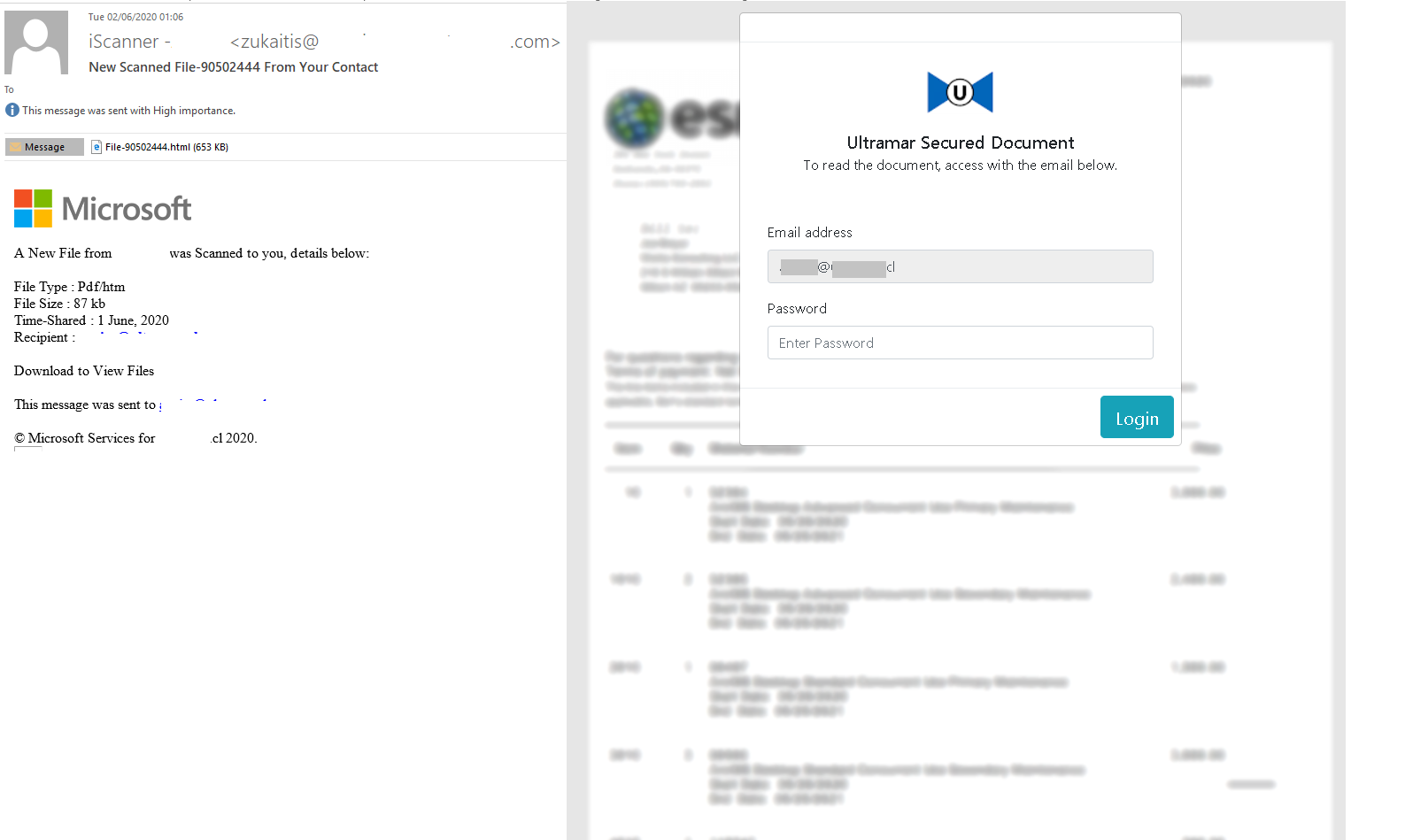
Spammers are doing everything they can to create plausible copies of the real cloud infrastructure, from web-based corporate email spoofs to file transfer services, as in the screenshot above. Among other channels similar to normal channels, the report includes voice messages, invites to meetings in Zoom and other teleconferencing services, notifications from the IT department, and simulated auto-responses with malicious attachments. Finally, there is an example of a creative attack on website owners: through a feedback form, they receive an email accusing them of stealing a picture or photo and evidence links (of course, malicious). Aerobatics: A scam without malicious links where the user is asked to call tech support.
In short, in the past year, the usual spam bacchanalia got a touch of COVID hysteria. The most interesting thing is that this happened against the background of a decrease in the share of spam in total mail traffic: in 2020 it was 50.37%, which is 6.14 percentage points lower than in 2019. Most likely, it was not spammers who began to work worse, but the number of legitimate emails increased due to the massive transition to remote work.
There have been some changes in spam geography: most often last year, junk emails were sent from Russia (21.27% of all unsolicited messages), followed by Germany. Last year, servers located in the US and China were the leaders in sending spam. The top three spam recipients are Spain, Germany and Russia.
Phishing links were blocked for 13.21% of users of Kaspersky Lab products. This is the global average, but in some countries the proportion of detections is higher: for example, in Brazil, phishing did not reach 20% of users. Overall, the authors of the report note an increase in the number of targeted email attacks targeting companies. We, the recipients of spam, we present the used of greater value when working, but not when we sit at home. True, in 2020, these two states did not differ much from each other.
What else happened
Microsoft forcibly removes Adobe Flash from users' computers with a Windows 10 update.
The patch for the Brave browser closes a serious privacy hole: it turns out that before that, all requests to .onion domains through the built-in Tor browser were leaked to the DNS server provider.
The first (and then the second ) sample of malware for Apple computers based on the M1 processor was detected.
The infrastructure of the Letsencrypt service has been seriously redesigned . Now it allows you to reissue all certificates within 24 hours. This is done in case you need to revoke certificates due to software errors.
Microsoft analysts releasedreport on SolarWinds attack on the company's infrastructure. According to them, the organizers were able to get access to the source codes of some solutions (in particular, Azure and Exchange). There was no evidence that Microsoft's infrastructure was being used to attack customers.