
In the aftermath of the attack, the company said the employee data was likely not harmed. Presumably CD Projekt has become the victim of a malicious campaign HelloKitty previously offending passages electricity supplier in Brazil ( here previous attacks are analyzed in detail). According to BleepingComputer, the leaked data has already been put up for auction with a starting price of one million dollars. The openness of the game developer about the incident is welcome. It should be noted some irony in how the entourage of Cyberpunk 2077 leaked into reality.
The second high-profile event was the attack on a water treatment plant in Oldsmar, Florida, USA. Pinellas County Sheriff Bob Gualtieri announced a cyberattack on critical infrastructure during a February 8 press conference . The attackers used standard means of remote access and, what is most unpleasant, tried to increase the sodium hydroxide feed by a factor of 100.
The incident was widely discussed mainly in the context of the dangerous use of remote access tools (in the described case, TeamViewer) to manage critical infrastructure. Leaked corporate address password leaks in city utilities (see tweet above). Even without them, directly controlling the computers in the wastewater treatment plant without additional security is a bad idea. Brian Krebs provides evidence in his article that this practice is commonin the whole country. And one more argument: if you fire all administrators who at least once opened remote access to the desktop, most likely there will be no one to manage industrial systems. The use of TeamViewer indicates underfunding and signals the need to comprehensively improve the security of critical infrastructure.
This high-profile news overshadowed Alex Birsan's interesting research on how to inject malicious code into building software that uses public repositories such as npm, PyPi, and RubyGems. Previously, this problem was investigated for uploading code with a typo in the name to the repository - in this case, it becomes possible to introduce arbitrary functions if the software developer makes a mistake in the name of the plug-in library. But this is not the only way. The article provides an interesting diagram of possible attack scenarios:
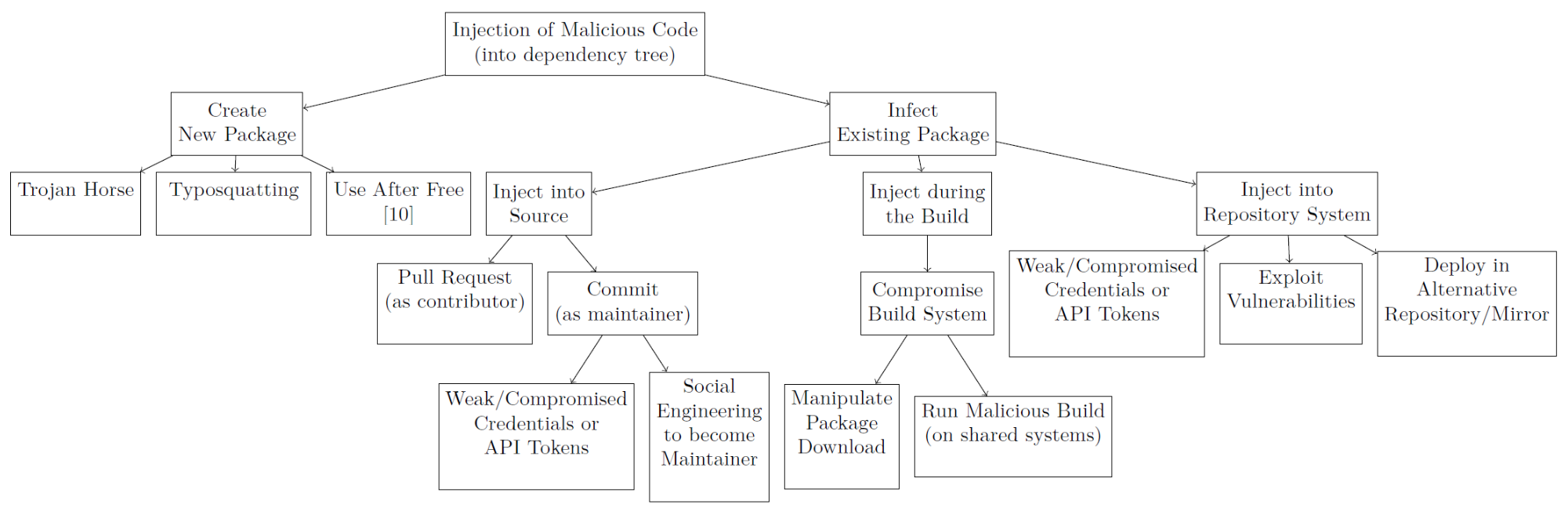
Birsan found another one. Analyzing the code for the PayPal payment system posted on GitHub, he found mentions of private libraries, apparently available only to the company's developers. Then he checked what would happen if you upload a package with the same name to the public repository. As it turned out, the public package gets priority over the private one. Then the researcher did a field test: he found private libraries, and then put his code in a shared repository under the same name. The code contained a simple trigger to report a successful "attack" to the author.
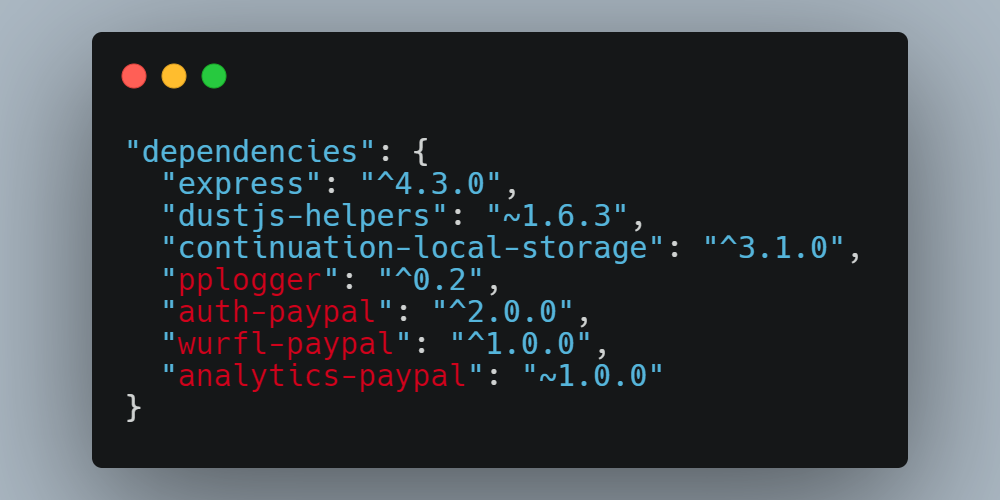
The results are impressive. The author managed to "crack" the code (in fact, to execute his program on the local network) of Shopify, Apple, PayPal, Netflix, Yelp and Uber. A number of companies have paid Alex significant rewards, corresponding to the danger of such a hack in the real world. Experts from Microsoft Azure offer several solutions for the described problem.
What else happened
An interesting study of the safety of video cameras intended for installation in nurseries and kindergartens. Access to devices is given to parents through a smartphone app, but, as it turned out, inside all clients connect through a common login-password pair that never changes. In addition, the connection is made using the HTTP protocol.
Microsoft developers are closing a bug introduced in the February patch set: it causes a blue screen when trying to connect to an access point with WPA3 authorization. In the same patch set , three serious vulnerabilities in the implementation of the TCP / IP protocol are closed .
ReportGoogle Phishing provides interesting statistics on the company's mail service: every day, one hundred million dangerous messages are blocked. Last year, Gmail analysts recorded up to 18 million phishing messages a day exploiting the COVID-19 theme. The average lifespan of a malicious campaign is three days.
Adobe is fixing critical vulnerabilities in Acrobat and Reader.
An interesting fact from the life of Wikipedia administrators is given in the thread above. In one of the datacenters, up to 20% of requests are for a flower photo. As it turned out , the image is loaded when launching a popular mobile application in India. Not only is this, in principle, not an ideal approach to creating software, but the picture is not yet shown to the user, that is, it is downloaded in vain.