Hello, today we will analyze the protocol of tanks (mobile)
The author is not responsible for the material provided in this article, everything that you read or saw was in a dream. Tools written during the protocol analysis process will never be released to the public.
The tools we need
x64 dbg
Cutter (Radare2)
C ++ 4. WireShark
Start (Protocol)
I started the analysis by defining the protocol the game uses for communication (TCP / UDP).
We open procmon (we try to authorize in the game client).

UDP ( ) 12 ( ping / pong), , 273 30 . "loginapp_wot.pubkey" - RSA-2048 ( )
( )
WireShark - UDP .


( ) (273 ) . , :
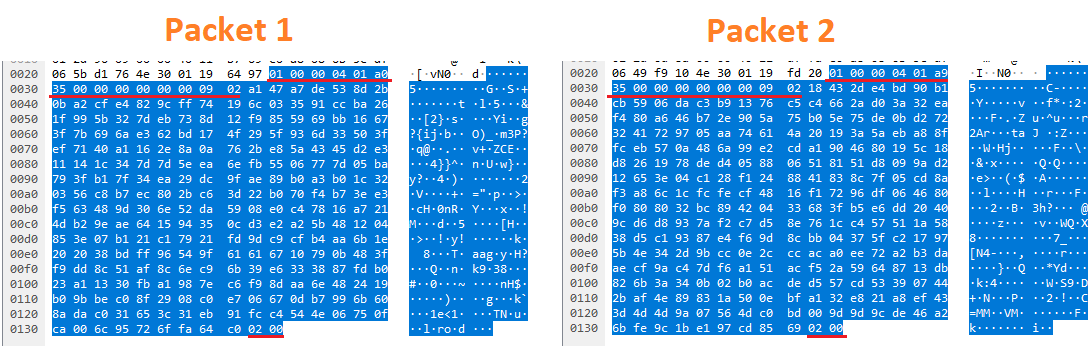
( 1-2 ) :
HEADER => [0x01, 0x00, 0x00, 0x04, 0x01, 0x31, 0x98, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x09, 0x02]
BODY => [? ? ? ? ?]
FOOTER => [0x02, 0x00]
256 * 8 = 2048 ( RSA-2048)
x64dbg 2 ws2_32 [send / sendTo]
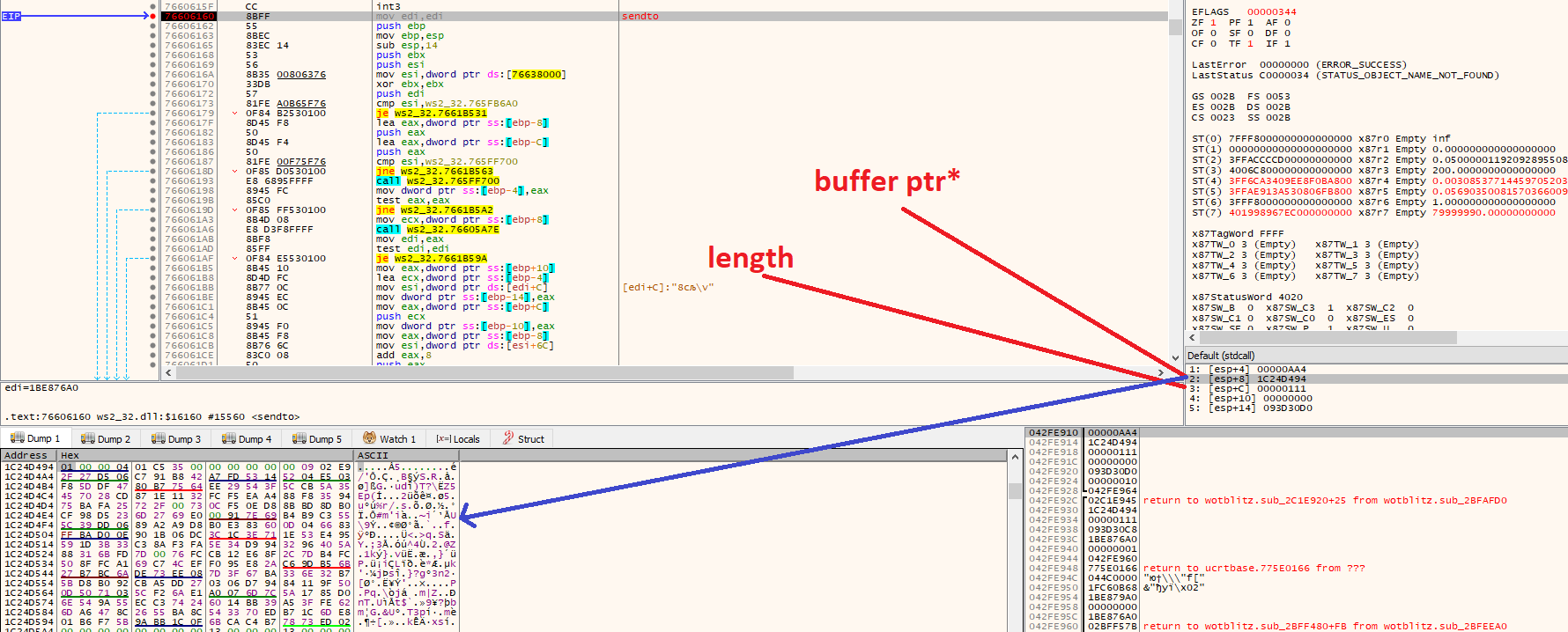
( ) . call stack, 0x100:
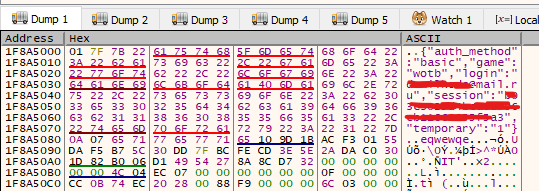
Json .
body .
?
(RSA-2048) .
.
( )
, .

(caller)
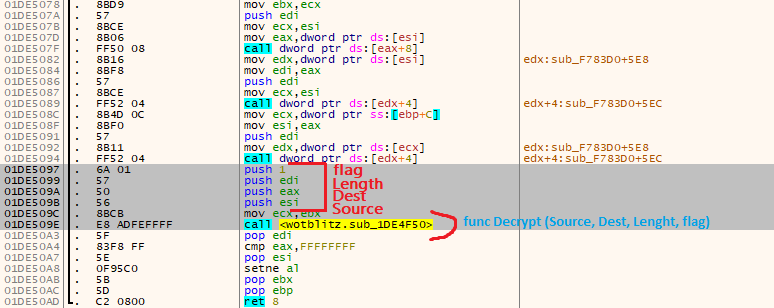
.
Splice is a method of intercepting API functions by changing the target function code. Instead, a transition is inserted to a function that the programmer defines.
First, we need to call the original decryption function.
Then read [ptr * dest]
I decided to write my Dll in C ++ to make a trampoline of the function
Do not forget about observing the convention when calling (__cdecl / __fastcall / __thiscall)
We get the address of the function via GetModuleBaseAddress + RVA
Splicing functions
Outcome
Inject dll into the game process (I used CE).
We authorize the game and enjoy.