Especially for future students of the course “Network engineer. Basic ” our expert - Alexander Kolesnikov prepared an interesting author's material.
We also invite you to take part in an open online lesson on the topic “STP. What? What for? Why?" ... The participants of the lesson, together with an expert, will review the STP protocol, analyze the logic of its operation, and analyze its advantages and disadvantages.
This article will tell you how you can work with network traffic. Using the example of several dumps of network traffic, the work of several useful tools will be analyzed, and approaches to extracting and collecting information from traffic are shown.
Instrumentation and research methodology
We will use the following software to parse the traffic:
, . tshark
wireshark
. , .
Disclamer: CTF, .
:
;
;
2 ;
, , , , .
:
1.pcap(9cd84b46fee506dae818ecdca76607d1)
. — , "FLAG-???????????"
. . , :
WireShark (, , tshark
. WireShark ). WireShrak "Statistics->Endpoints":
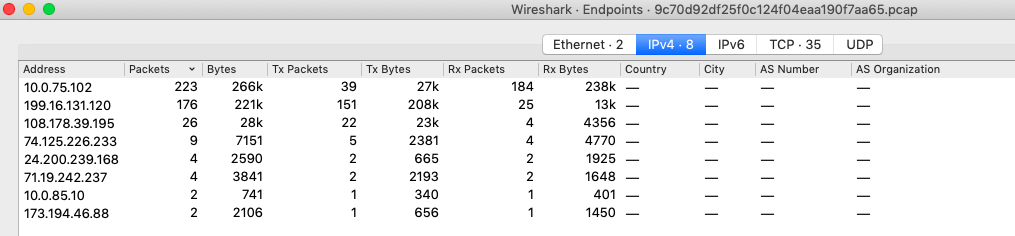
8 IP , . . "Statistics->Protocol Hierarchy":
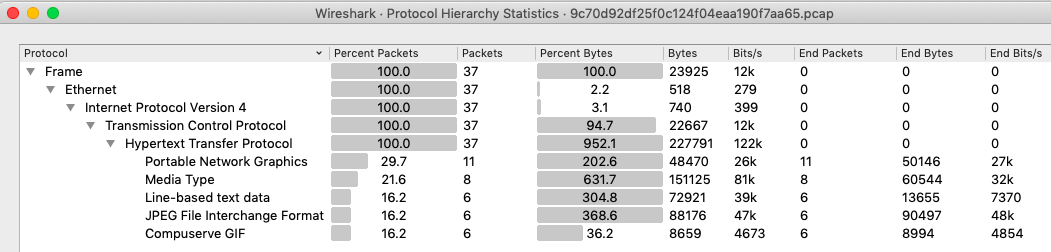
, — http. pcap
body
. tshark
. :
``` tshark -r ./1.pcap -Y http -Tfields -e http.file_data | grep "FLAG"```
:
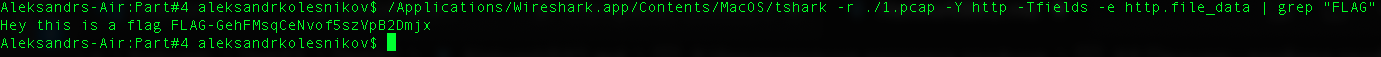
— 2.pcap (9a67e1fb9e529b7acfc6e91db6e1b092)
. . :
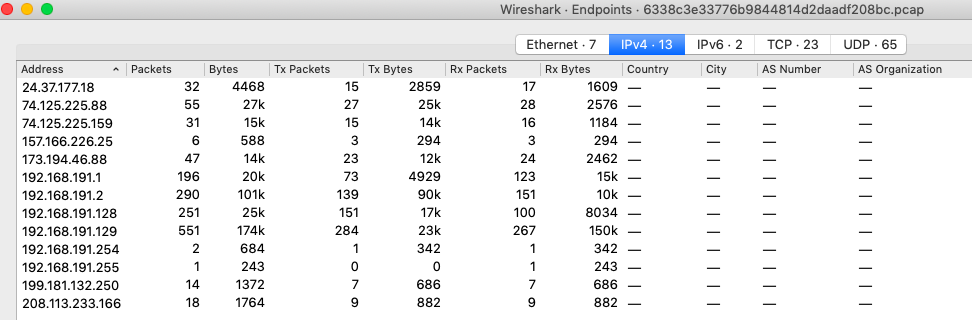
13 — . :

, . tcp . udp - :
``` tshark -r ./2.pcap -Y 'dns' ```
, dns, :

ip , - . :
```tshark -r ./2.pcap -Y '!icmp.code && dns.qry.name contains 192.168' -Tfields -e
dns.qry.name | tr '.' ' ' |awk '{print $1}' |xxd -r```
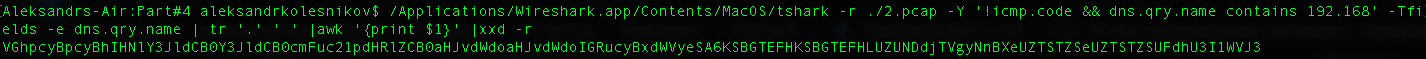
base64
, :
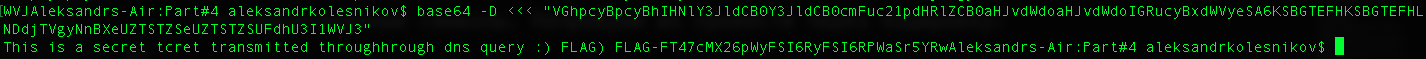
``` base64 -D <<<
"VGhpcyBpcyBhIHNlY3JldCB0Y3JldCB0cmFuc21pdHRlZCB0aHJvdWdoaHJvdWdoIGRucyBxdWVyeSA6KSBGTEFHKSBGTEFHLUZUNDdjTVgyNnBXeUZTSTZSeUZTSTZSUFdhU3I1WVJ3"```
:
3.pcap(0e66830db52ad51971d40c77fa5b02c0)
. :

, , — . http.
``` tshark -r ./3.pcap -Y http```

, http "flag.zip" "secret.txt". Wireshark :

, flag.zip
WireShark. , — Raw :

:

, , . , , tcp, :
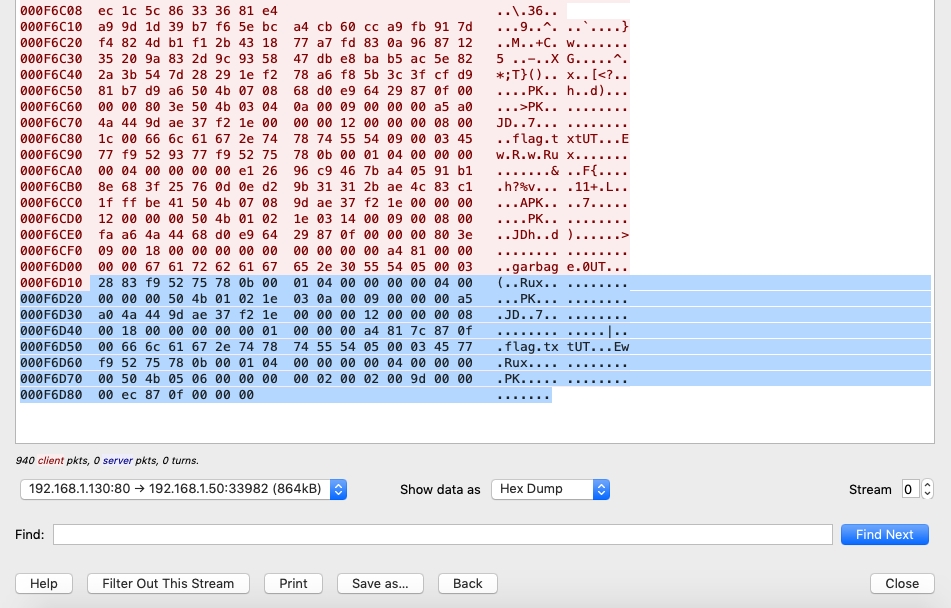
:
```python
data = []
with open('dump') as f:
data = f.read()
with open('tesst.zip','w') as w:
w.write(data[1010788:])
```
:
``` 7z x ./test.zip ```

, , flag.txt
. , 4.pcap(604bbac867a6e197972230019fb34b2e)
.