 The past week has been eventful. Let's start with three vulnerabilities in Apple's mobile operating systems that were allegedly exploited in real-world attacks. In a
short message from Apple, two vulnerabilities are related to the WebKit engine - they allow the execution of arbitrary code. Another hole in the core of iOS and iPadOS allows for privilege escalation.
The past week has been eventful. Let's start with three vulnerabilities in Apple's mobile operating systems that were allegedly exploited in real-world attacks. In a
short message from Apple, two vulnerabilities are related to the WebKit engine - they allow the execution of arbitrary code. Another hole in the core of iOS and iPadOS allows for privilege escalation.
All three vulnerabilities are closed in OS update 14.4 from January 26th. Apple reports that it is aware of the active exploitation of these three bugs. The details of this attack are unknown, but there is a recent example of zero-click exploitation in iOS 13 disclosed in a Citizen Lab report at the end of December last year.
On Thursday, January 28, a specialist from the Google Project Zero team, Samuel Gross, published a description of another security mechanism implemented in iOS 14. Using reverse engineering, the expert analyzes the structural change in the work of the built-in messenger iMessage. Apparently, the current version of Apple's mobile OS has implemented strict isolation of all input processing tools. This should make it difficult to create new attack methods, even using as yet unknown vulnerabilities. On the one hand, Apple is not limited to the treatment of individual bugs, on the other hand, even with new protection mechanisms, attacks on devices with the subsequent installation of a backdoor are quite possible. Either way, it's worth updating your iPhone or iPad to the latest OS.
A vulnerability in the sudo utility, a universal tool for temporary elevation of user rights, was discovered by experts from Qualys (original article , news , discussion on Habré). Using the sudoedit command can cause a buffer overflow with subsequent elevation of user rights on the system. The vulnerability got into the utility code in 2011, and sudo versions 1.8.2-1.8.31p2 and 1.9.0-1.9.5p1 are affected. Patches for popular Linux distributions were released on January 26th.
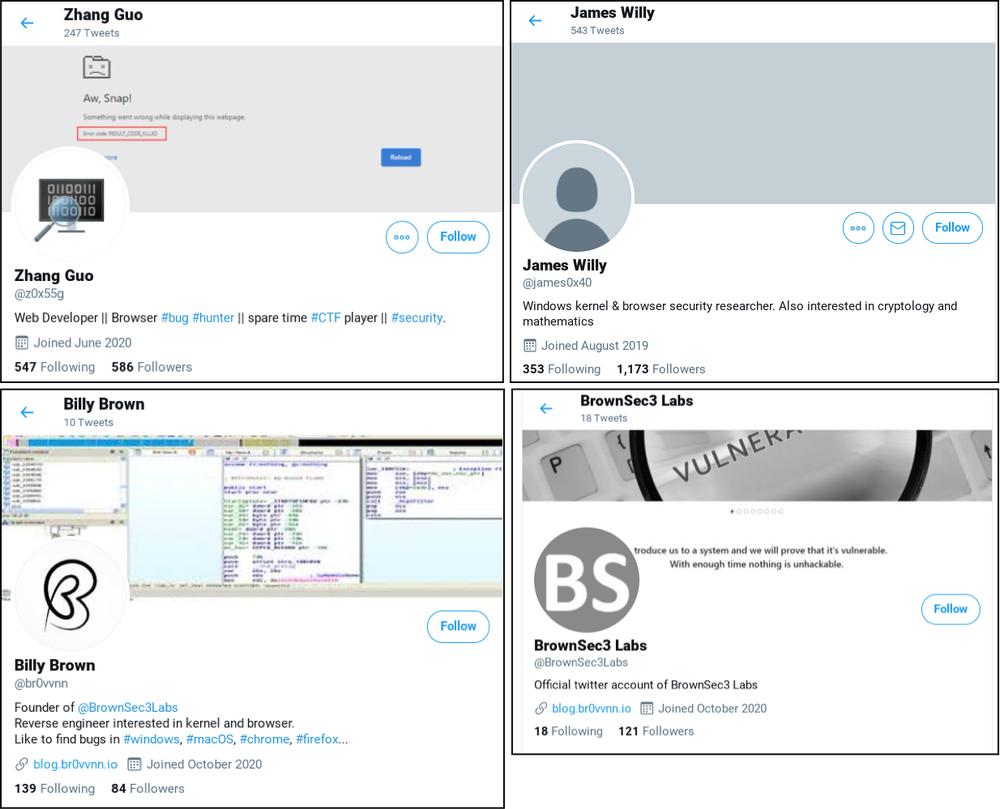
Finally, last week it became known about an attack on the information security experts themselves. The review article appeared in Vice, technical details in Google Threat Analysis Group and Microsoft . At the end of last year, several Twitter accounts (examples are in the screenshot above) actively communicated with security specialists, offering to participate in the analysis of an exploit for a vulnerability in Windows Defender. Those who entered into correspondence were sent a project for the Visual Studio IDE with a malicious appendage.
Most likely, this was a fallback method of attack, and the main method was a pseudo-blog, where an exploit for a vulnerability in the Chrome browser was posted. For which one is unknown, but links to the blog were actively distributed on Twitter and on other sites, for example, on Reddit. The virtual personalities had full bios, LinkedIn profiles, and GitHub accounts. On Twitter, there is some evidence of a successful attack, although often it was only the virtual machine that was specially raised to open such links that "suffered". However, this story suggests that social engineering works for professionals too.
What else happened
Europol seized control of the Emotet botnet.
A detailed description of the attack on the head unit in a Nissan car.
Firefox developers rolled out version 85, where they implemented protection against the so-called " super cookies ". This method of spying on the user is now made as difficult as possible by separately caching data for each visited website.