In this article, I would like to touch upon the application of security standards requirements in software development.
The main material was prepared and compiled based on the requirements of the PCI DSS standard . These requirements can also be applied to the processing and storage of personal data in terms of fulfilling the requirements of the GDPR .

12 , , , ( ) . PCI Council PA DSS, . , , , , PCI DSS, . , , PA DSS, . , , PA DSS.
, , .
, .
PCI DSS.
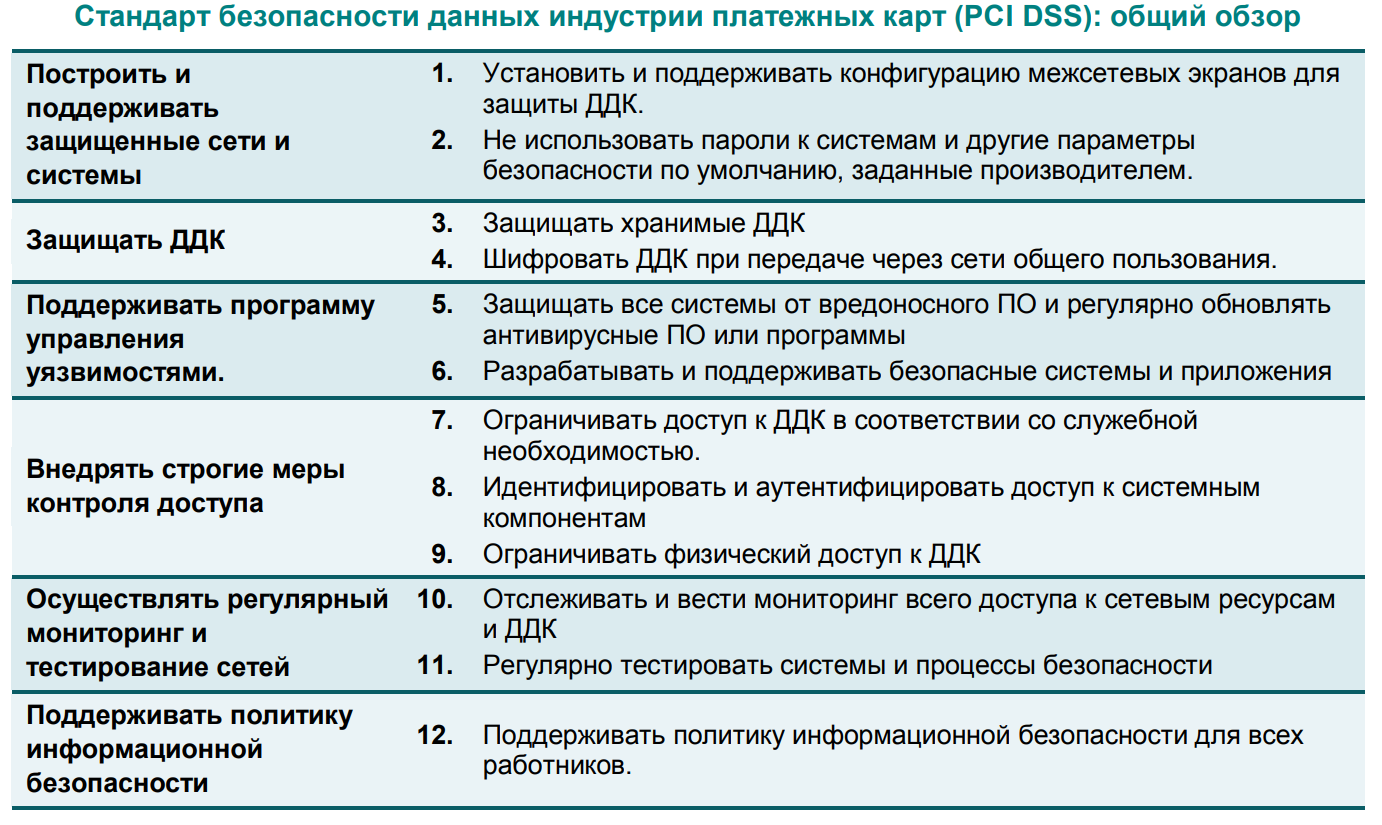
PCI DSS ( PCI DSS 3.2.1)
1. . — , PCI DSS + GDPR ( ).

? ? ?
, (), , . . . . . , .
2. , .
. ( ). . , , .
3. .
. . TLS, .
.
4. , .
, , (PAN, CVV). - . - . - Cvv .
5. .
, , . , .
6. .
. . , , .
7. .
.
, .
8. , ( ).
. . , . “”.
9. OWASP TOP 10.
. , Bug Bounty. OWASP TOP 10.

10. .
. , .
11. .
. , . , , . . . .
12. .
. ( , ). .
13. .
, . . , ( , , ).
14. .
Passwords should be chosen that do not lend themselves to brute-force attacks. The storage and transmission of passwords should be ensured in such a way as to minimize the likelihood of its compromise (password storages, separate storage, etc.).
15. An item that you probably want to add yourself