CISO: Igor, someone got access to our cameras
Igor: @@@!
CISO: Go figure it out. Check the configurations of every camera, every computer.
Igor: But there are 100,500+ of them, it will take a lot of time!
CISO: Take Mikhalych, our electrician, as a child, he visited the radio circle as a child.
Igor: Maybe we'd better try SCAP?
CISO: And what the ...

Introduction
Many documents (standards, orders, recommendations) define requirements for the security settings of information systems, search for vulnerabilities and update management. A recently discovered problem in one of the largest corporations once again demonstrates the need to manage vulnerabilities and configurations.
As a rule, an information system is a complex and dynamic object, therefore, in order to comply with the requirements, constant monitoring of its state (audit) is required.
The de facto method for automating security auditing is the approach proposed by NIST and described in the Security Content Automation Protocol ( SCAP) specification .
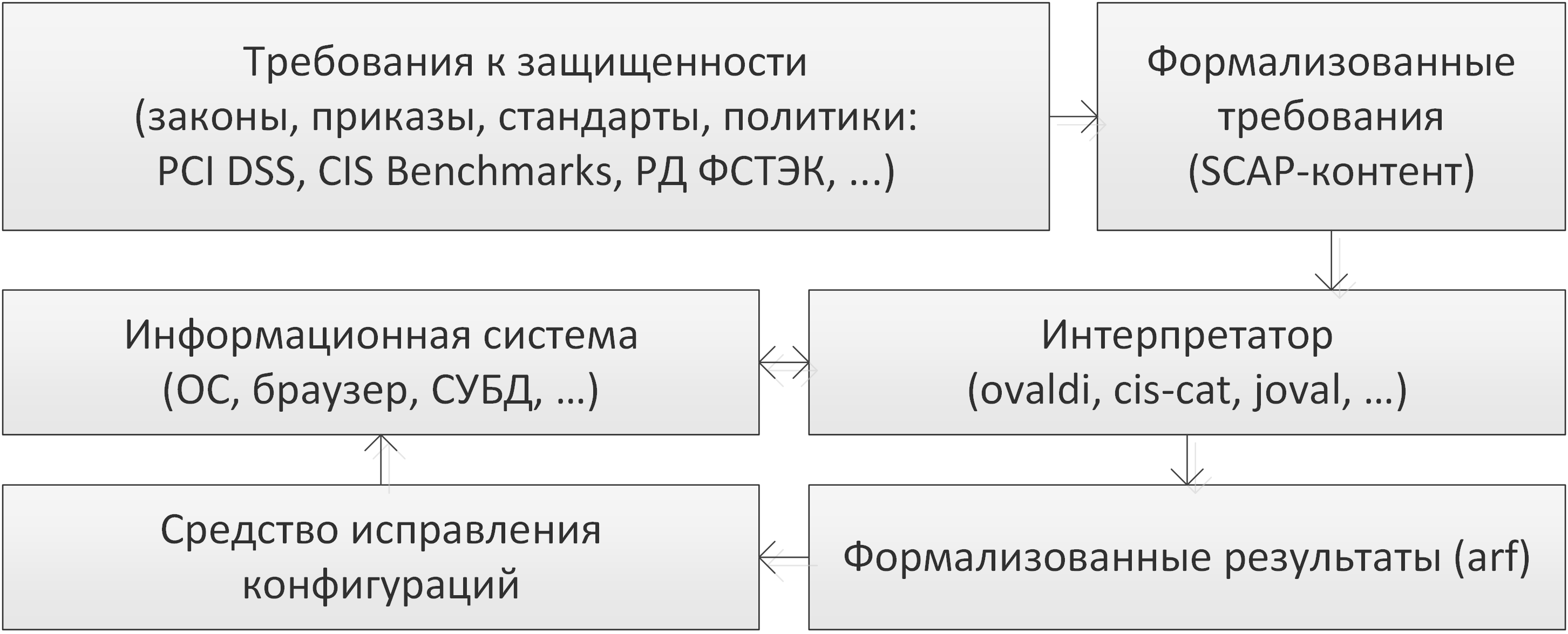
Structural diagram of the process of automated security audit of information systems using SCAP.
Next, I suggest that you familiarize yourself with all the points of the audit automation process in more detail. Go!
Requirements
The source of the audit, its basis and reason are high-level paper requirements for information systems, which are imposed by regulators, defined in best practices, own policies or those of partners.
For example, the PCI DSS standard describes the requirements for supporting firewall configurations, updating programs, regularly testing security systems, and supporting information security policies.
The recommendations of CIS Controls v. 7.1 presents the requirements for continuous vulnerability management (CIS Control 3), secure configuration of hardware and software (CIS Control 5).
And the FSTEC order No. 17 defines the requirements for the protection of information contained in state information systems.
The main problem of all requirements and recommendations is their high-level non-formalized description, which does not allow their use in the automation process. The solution was proposed by NIST in 2009 with the development of the SCAP specification.
SCAP
SCAP (Security Content Automation Protocol) is a hierarchical specification that allows information systems to be automatically configured, to search for and fix vulnerabilities, and to assess the level of security.
SCAP includes a number of interconnected components, the formal description of which is based on XML: XCCDF , OVAL , OCIL , ARF languages ; identification schemes CCE , CPE , SWID , CVE ; metrics CVSS , CCSS...
While other components of the specification are also important, the core languages are XCCDF and OVAL.
XCCDF (Extensible Configuration Checklist Description Format) is a language that describes lists of information systems security settings and defines the interconnection of other SCAP components. The language is designed to provide information exchange, document generation, automated testing and conformity assessment to specified requirements. Contains no commands to perform a scan.
OVAL (Open Vulnerability and Assessment Language) is a declarative language for logical statements about the state of the system. It is the main component of the SCAP standard, which is used to describe vulnerabilities and required system configuration.
So, SCAP-content is the requirements for information systems, which are translated into a formalized form, which makes it possible to automatically check systems for compliance with requirements and search for vulnerabilities.
I will analyze XCCDF and OVAL in detail in the next article and leave a link here.
Question. Where to get SCAP content?
- Create yourself, which is quite laborious and requires an understanding of the specifications. Life is made easier by an open source SCAP editor that allows you to create XCCDF and OVAL documents in an easy-to-use graphical interface.
- Use open resources. For example, the base of OVAL-descriptions from FSTEC, USGCB requirements or a repository from MITER.
- Buy. When purchasing some commercial products, you can get access to the manufacturer's databases.
Interpreters
Formalized requirements in the form of SCAP content are input data of so-called interpreters or scanners, of which there are a great many. MITER maintains a record of “authorized” organizations, their products and OVAL repositories .
Consider some free interpreters: OVALdi , OpenSCAP and ScanOVAL .
OVALdi
The interpreter was developed by MITER. It is intended only to demonstrate the evaluation and syntax check of the developed OVAL documents. Has minimal functionality for evaluating information systems. Available for both Windows and Linux. Distributed under BSD license.
OVALdi can be controlled only from the command line and only locally, for which you need to enter the command with administrator rights:
ovaldi.exe -m -o "definitions.xml"
where
m
- do not check the integrity of the OVAL document,
o
is the path to the OVAL document.
Openscap
Red Hat's project, represented by a variety of products, including OpenSCAP Base - a CLI-based open source scanner and SCAP Workbench - a GUI-based scanner.
In the next article, I will detail the deployment and use of Red Hat's free automated auditing system and leave a link here.
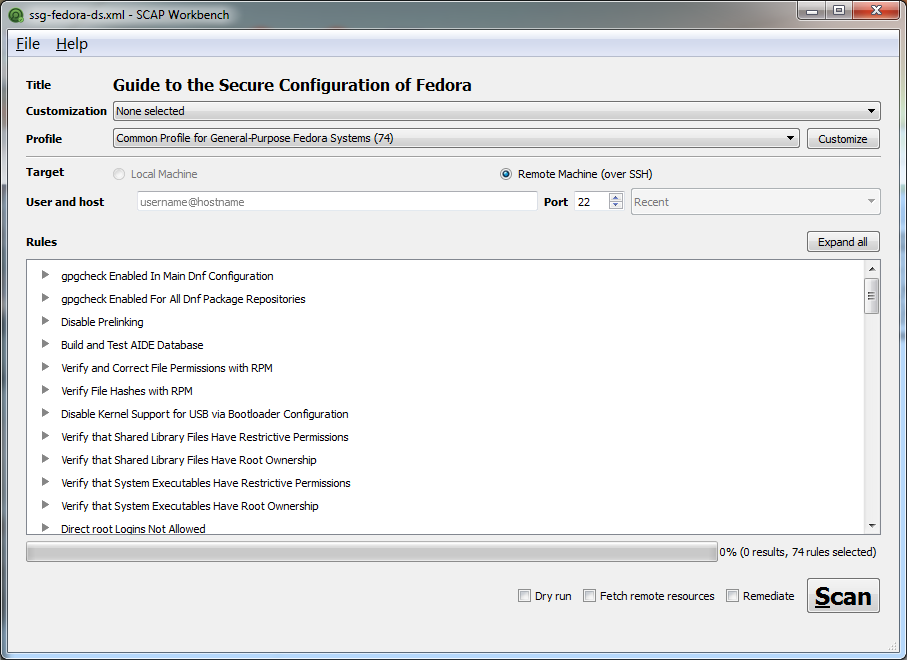
SCAP Workbench interface
Despite the fact that OpenSCAP tools are suitable for Windows, more possibilities are presented for unix-like systems, because initially the project was aimed only at their assessment.
Command interpreter in the terminal is triggered:
oscap oval eval "D:\definitions.xml" --report "D:\results.html"
,
and then will check the system according to the instructions in the document OVAL-
«D:\definitions.xml»
with saving the results to a file
«D:\results.html»
.
SvanOVAL
A tool developed for FSTEC by one Russian company. The tool is free and suitable for both Windows and Linux (Astra).

ScanOVAL interface
The main drawback is that the capabilities of the tool are limited only by checking the system for vulnerabilities that are presented in the FSTEC database, while the digital signature of the OVAL document is checked, so it will not work to feed the custom file. Despite this, ScanOVAL is FSTEC's big step towards paperless security.
SCAP logic
For simplicity, many nuances have not been taken into account, which does not violate the SCAP principles in general, but allows a better understanding of the approach itself.
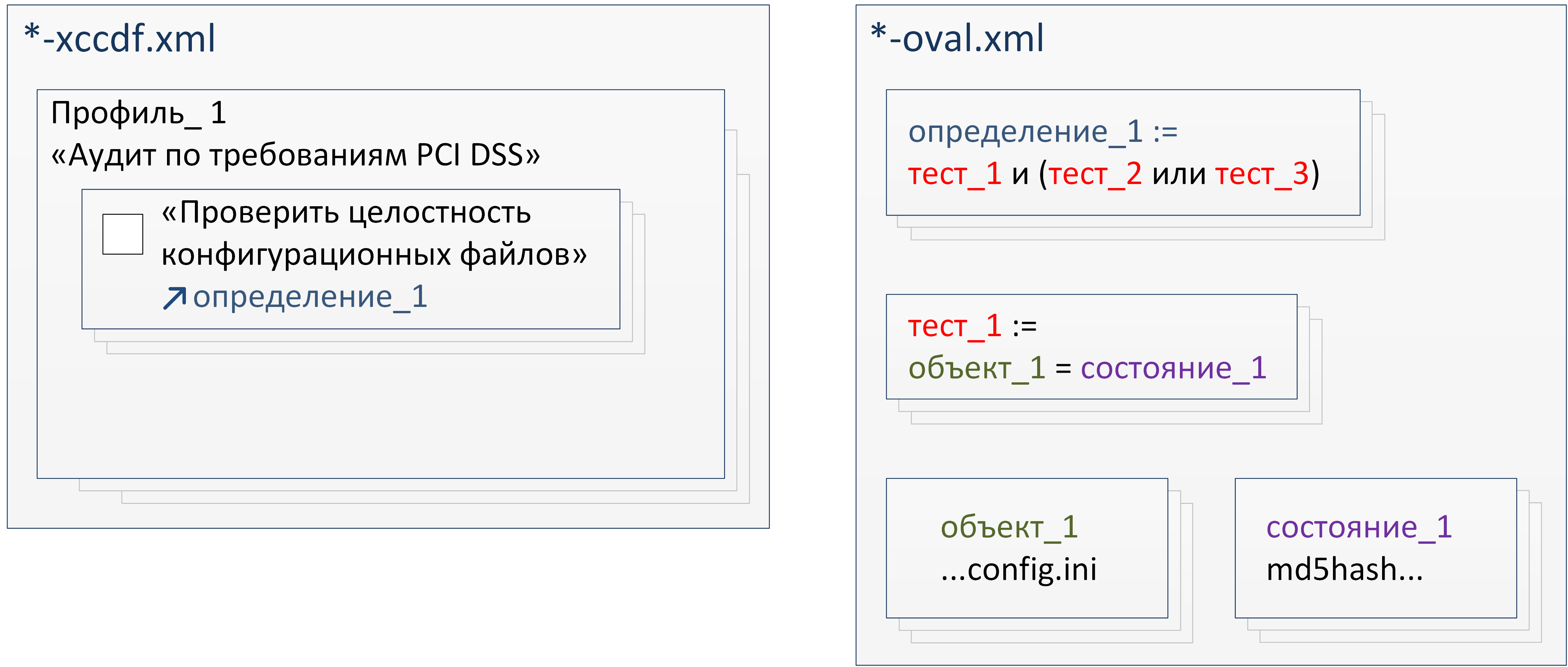
SCAP Basic Logic
Diagram The XCCDF document contains profiles, one of which can be selected for testing, for example - searching for vulnerabilities in Windows 10 or meeting some specific requirements. In fact, the profiles contain checklists that must be checked to determine if the system meets this profile.
Checklists contain descriptive information - verbal requirements, recommendations for resolving nonconformities, assessment metrics, etc. All this is used to display explanations for the verification results.
But the main thing that each item in the checklist contains is a link to a specific definition in the associated OVAL document. After processing the OVAL definition, the interpreter returns a boolean result (
true
or
false
), based on which it concludes that the request from the checklist has been fulfilled.
In an OVAL document, definitions form a logical bundle of tests to be passed. Each test uses logical operators to associate objects and states .
Tests, objects and states are of various types, of which there are many. It is their diversity that determines the broad capabilities of the SCAP specification.
For example, for Windows, among others, there is a type
group_sid
(
group_sid_test
,
group_sid_object
and
group_sid_state
) that allows you to evaluate users and subgroups by SID identifier. And the
dpkginfo
Linux type allows you to check information about a given DPKG package. The type
textfilecontent
is system independent and provides validation of the contents of a text file, such as a configuration file.
The state in the OVAL document specifies the required value of the parameter that characterizes some object.
When processing a test, the interpreter determines the value of the parameter that characterizes the current state of the object and, in accordance with the logic specified in the test, compares it with the specified value. Based on this, a boolean test result is generated.
The definition also compares the results of each linked test according to a predetermined logic, resulting in a final result that represents the fulfillment of a specific checklist requirement.
For example, if there is a requirement to ensure the immutability of executable files, then when it is translated into SCAP-content as the object will be given a specific executable file, which is determined by the full name:
.../example.exe
. Status will be set to the desired value of the hash sum of:
D41...27E
. The test will determine the comparison operation:
equal
- equality. In this case, the interpreter will calculate the hash sum of the file
.../example.exe
and compare it with the given one
D41...27E
. If they match, it will return a positive result.
results
According to the SCAP specification, audit results are presented in ARF (Asset Reporting Format).
The ARF report is contained in an XML document and includes profile descriptions, checklist requirements, and summary results for each checklist item.
Typically, the scan results are converted to human readable form.
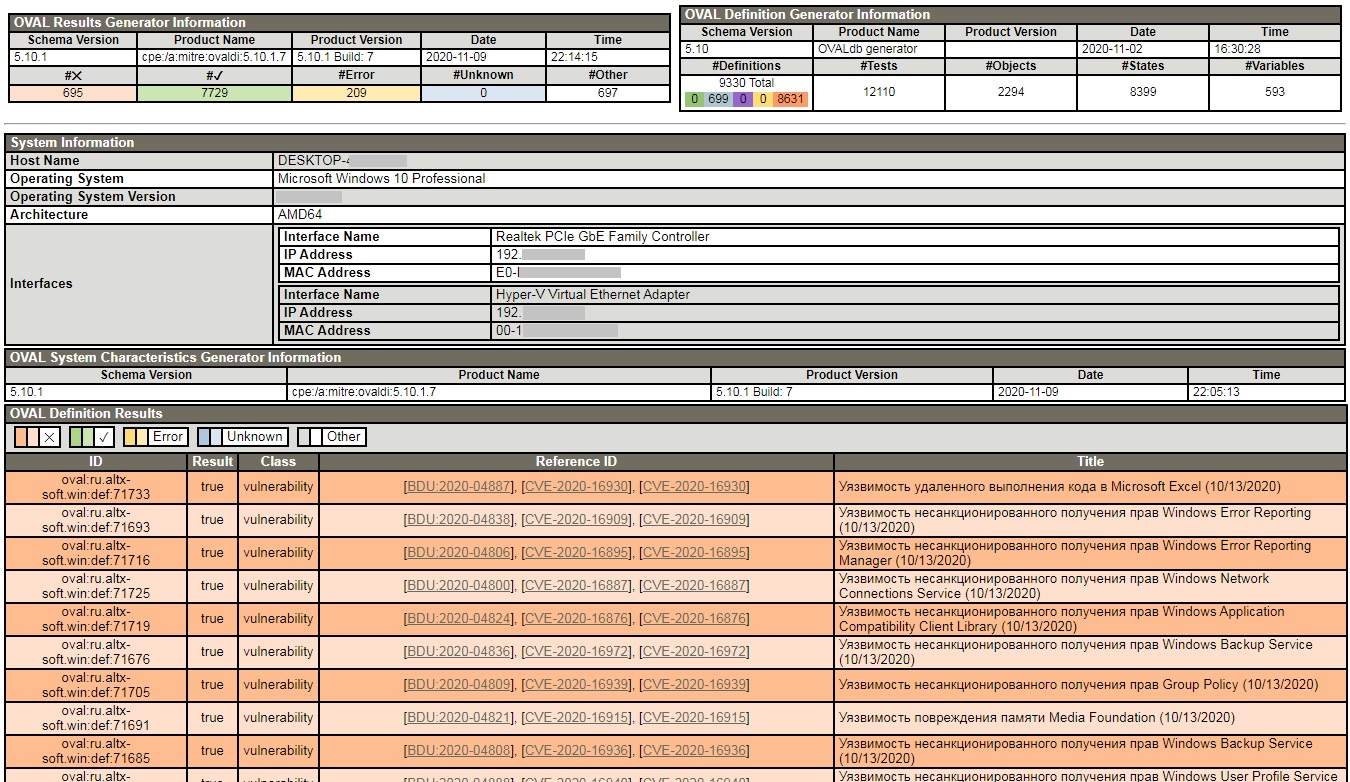
Sample results of checking Windows 10 for vulnerabilities using the OVALdi interpreter
Correction
The capabilities of the SCAP protocol provide for automatic correction of found inconsistencies and elimination of vulnerabilities (functionality must be supported by an automated audit system).
This seems like a good option, but automatic fixes can break the system, so use these features carefully.
The most common variant is when the results of the check are presented as a list of unfulfilled requirements and a textual description of the actions that need to be performed to correct them. For example, as in the free version of CIS-CAT.

Example of CIS-CAT Lite interpreter results with recommendations for elimination
Conclusion
Audit automation is the most important task of information security, its relevance is due to the number, complexity and dynamism of systems that must meet certain requirements.
SCAP provides a flexible and multifaceted automation methodology, which however has disadvantages:
- the complexity of translating high-level verbal requirements into formalized SCAP content;
- the complexity of creating interpreters that allow you to use the full potential of the SCAP specification.
On the other hand, from the end-user perspective, SCAP tools are a simple and effective tool that can reduce time costs and increase the security level of the administered infrastructure.