The number of ways that hacker groups use to attack companies seems endless, but in reality they are not. Almost all tactics and techniques of cybercriminals have been analyzed and documented in the public MITER ATT & CK database. In this post, we will tell you how, during the investigation of a real incident, using the MITER ATT & CK base helped us figure out which group attacked the client company.

Initial analysis
We were approached by a company, one of the servers in the network of which was constantly exchanging data with a third-party Internet server. After initial examination, it turned out that this traffic contained data and commands that were exchanged between the malware and the attacker's C&C server.
: , , , . , .
, 62 . 10 13 , , 22 -. , , .
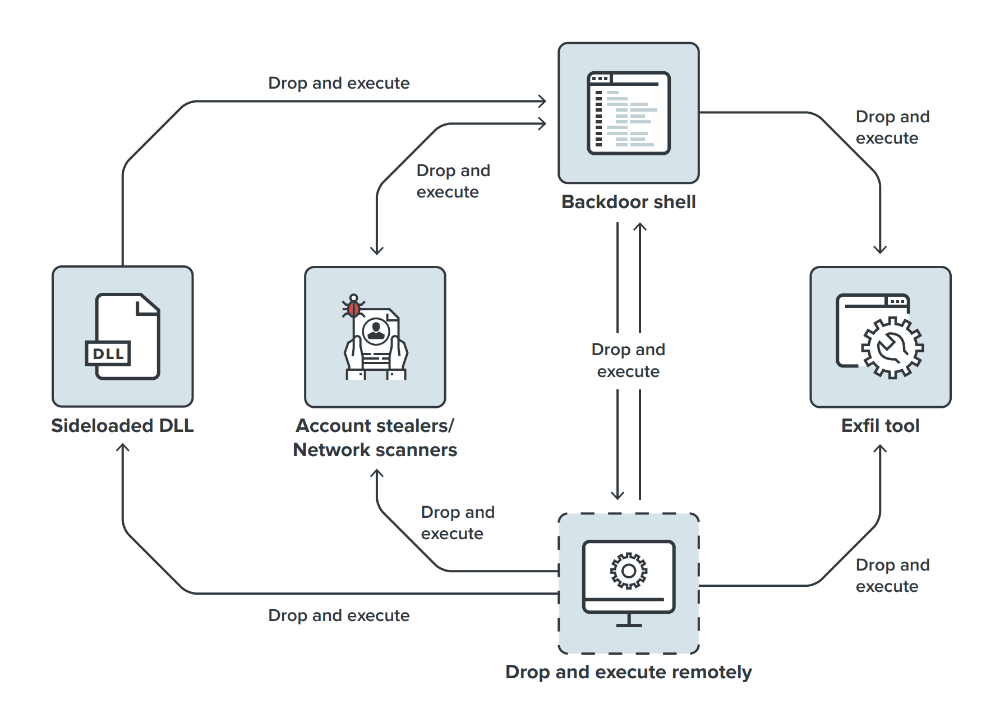
, DLL, cmd.exe. ProcDump Mimikatz. IPC . Schtasks, wmic-.
PDF MS Office, , .
, , MITRE ATT&CK, — APT3 APT32.
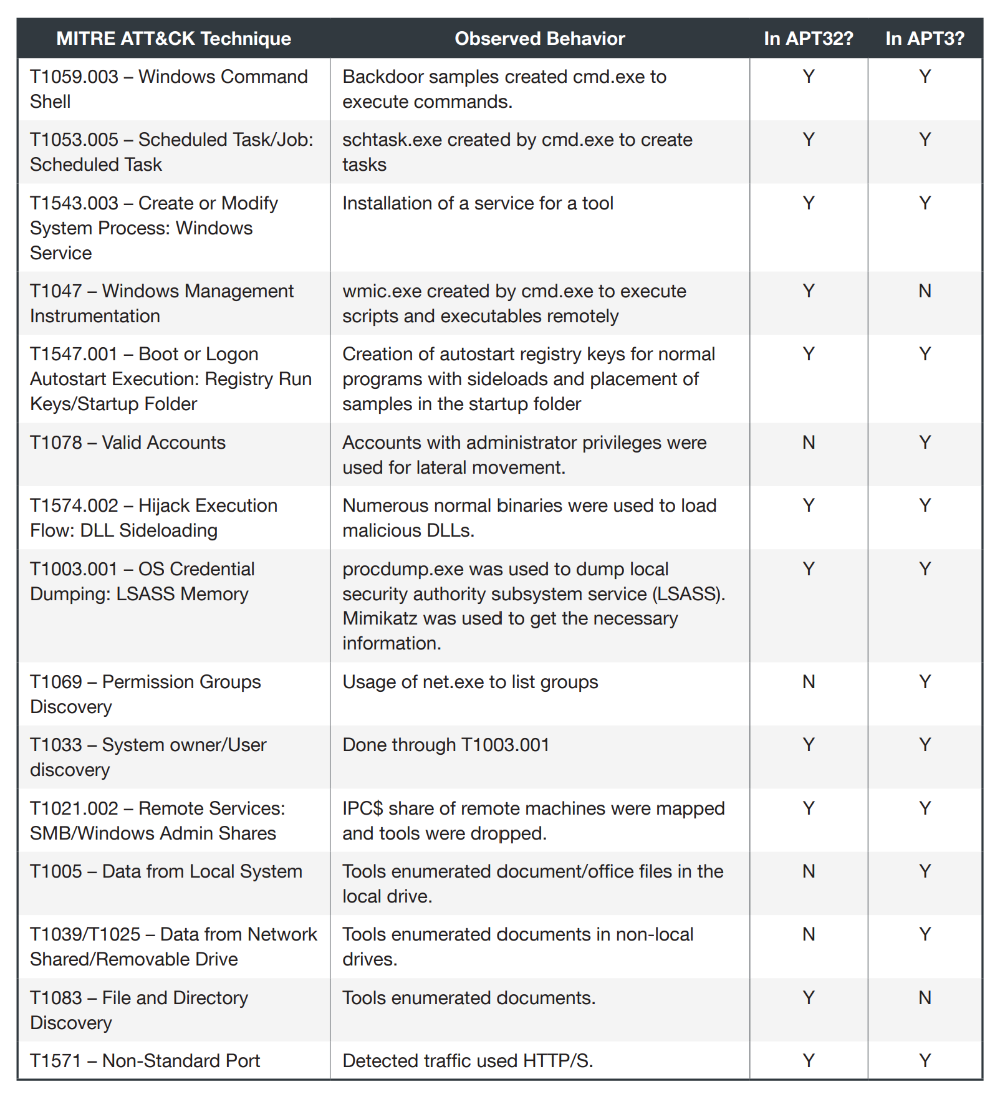
, , , . . , , .
:
,
,
.
.
, — , , RAR- . . .
, , IP- , ; . . . , , . XOR.
URL . . , , , PDF-.
PowerShell- MySQL
MySQL. , , UID, , SQL-, . :
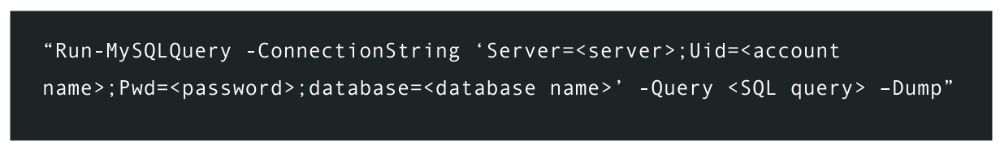
, , , , , , . . CSV-. , .
FTP-
, . , 7-Zip , XOR-. FTP-, . , .
-, cmd.exe. , , . , .
, -, Apache. - :

, . :
TROJ_CHINOXY.ZAGK, dll;
Procdump — LSASS;
Mimikatz — ;
NBTScan — .
, . .
. , :

, , dll. , dll. , dll -, Procdump .
, , - , , , .
, , , , . . , .
, « », .
№ 1
, dll FTP. .
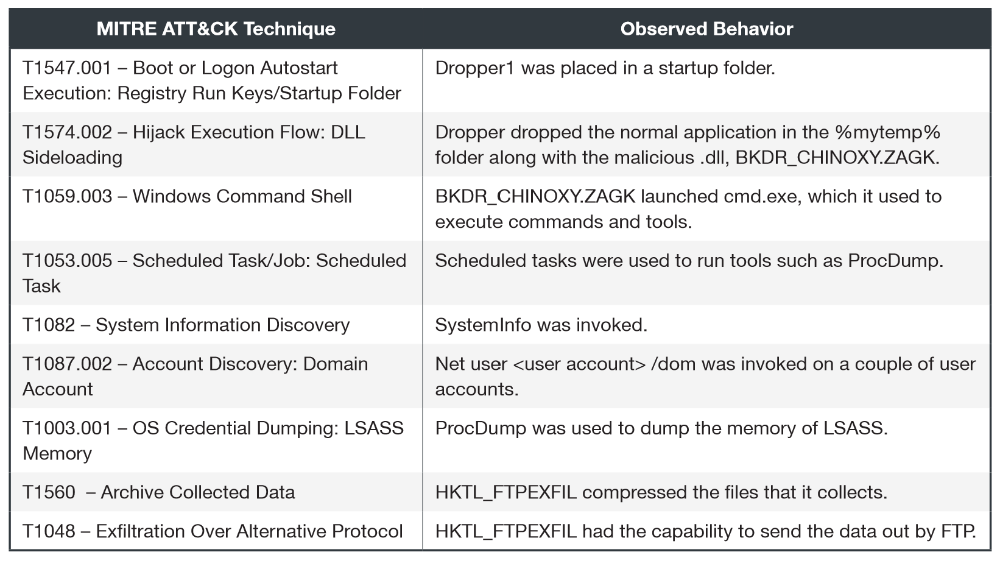
Lotus Blossom
. Trip, Lotus Blossom. , № 1:
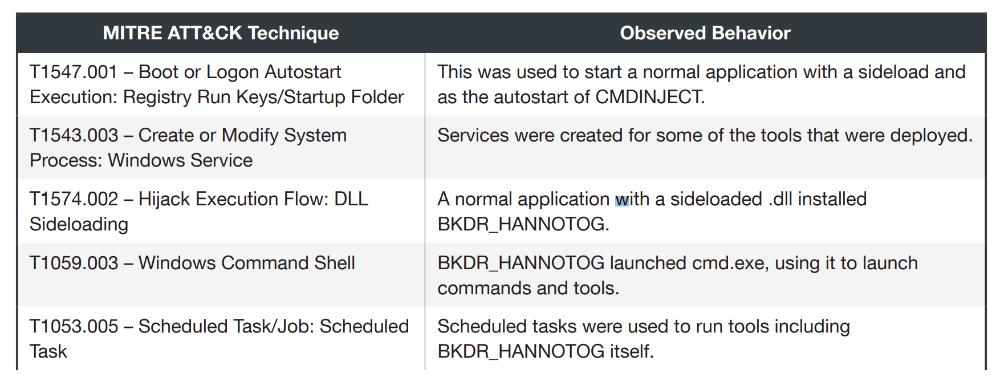
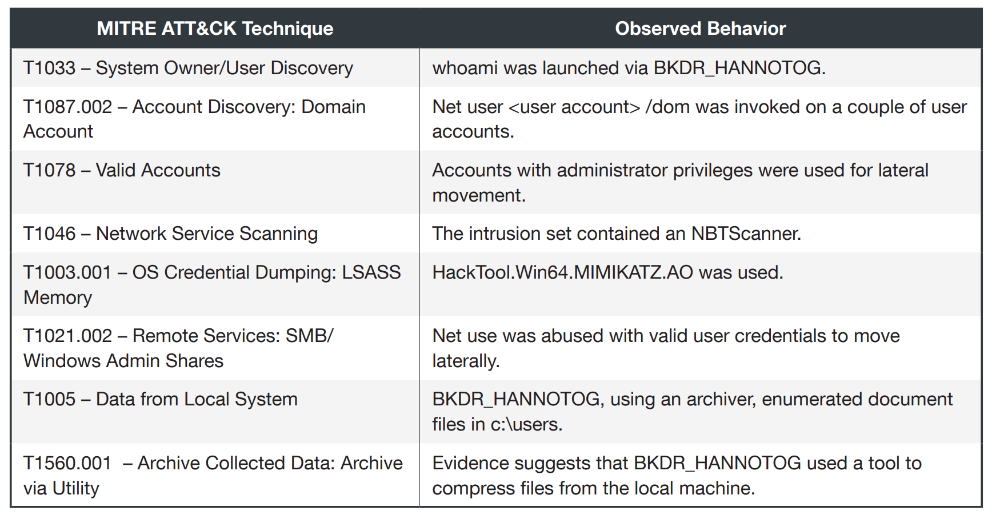
№ 2
, APT-. , RAR-. . dll, . , .
OceanLotus
, APT32. , . , .
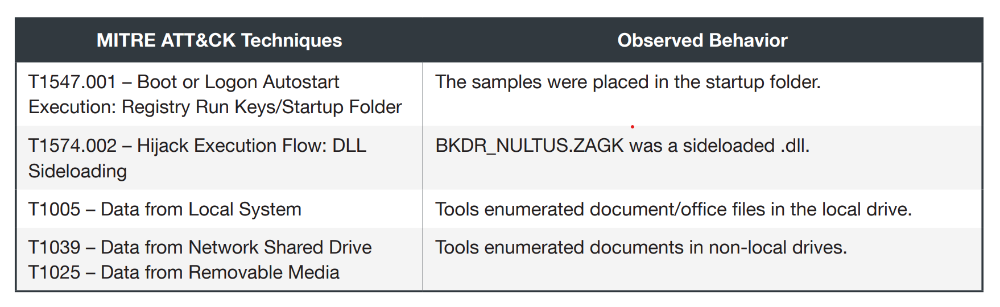
OceanLotus APT32 . , , .
, , . — , , .
, , , . , , sideloaded-DLL.
, MITRE, . , . , APT, . , .