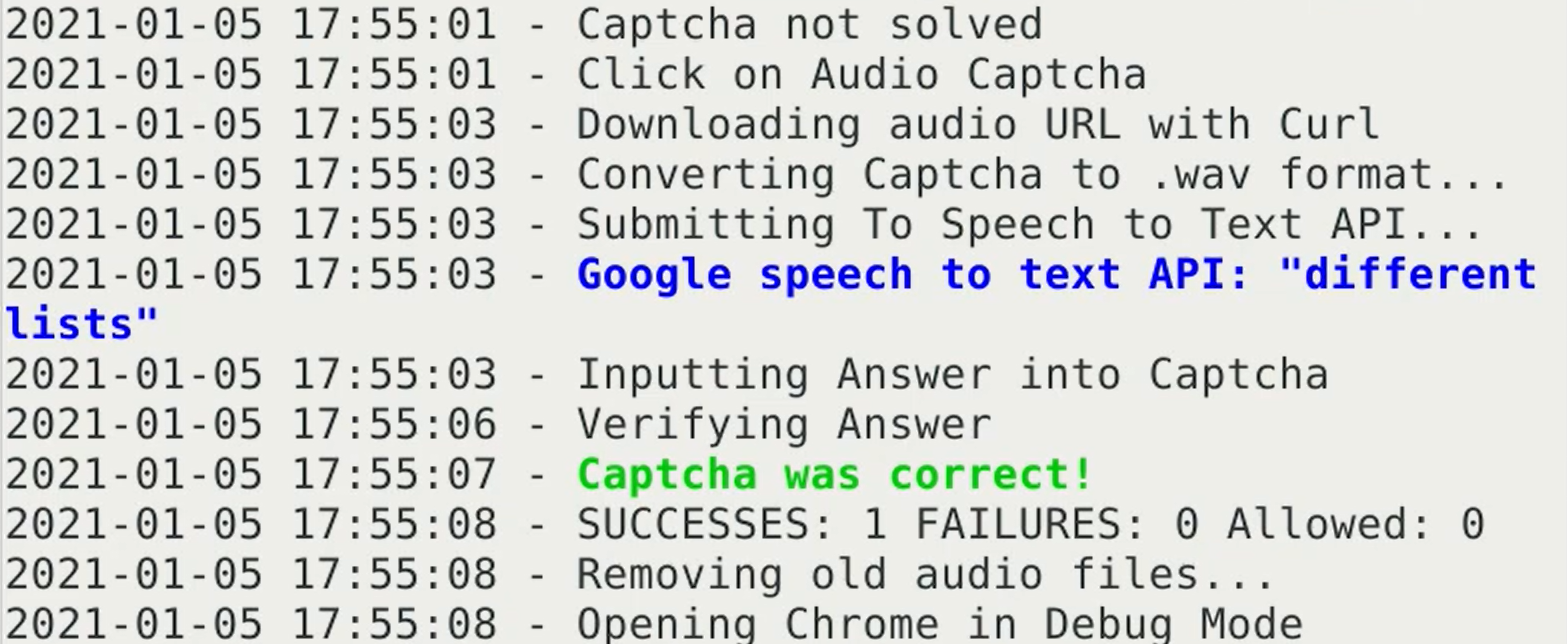
It was not the main captcha with images that was hacked, but an alternative method of verification using a voice message. A code is sent in the audio message, which must be entered in the appropriate field. Nikolay improved the method developed earlier against the previous version of reCAPTCHA v2: the script intercepts an audio file with a voice message and sends it to the Text-to-Speech service. The code is recognized properly in over 90% of cases. The researcher confirmed that the method also works against reCAPTCHA v3: apparently, the alternative authorization method migrated straight from the previous version, although the captcha upgrade to the third version also broke the Proof-of-Concept published two years ago. Nikolay posted an updated version in his repository on Github ...
Video demonstrating the operation of the updated script (fully automated up to mouse movements):
What else happened
In early January, the Firefox and Chrome browsers were updated . In both cases, serious vulnerabilities were closed that could allow arbitrary code to execute and gain control over the system. In the case of Firefox, both the PC version and the mobile release are affected. In Chrome, the vulnerability is only relevant to computers.
Closed vulnerability in NVIDIA drivers. In addition to the traditional privilege elevation hole, the patches address several issues in the vGPU driver for virtualizing GPU resources. The exploitation of these bugs, although it does not allow taking control of the host machine, allows information disclosure and denial of service.
January Android patch set closes43 vulnerabilities, including one in the Android System component, allegedly related to the operation of the Bluetooth module.
Researcher Ahmed Hassan found a vulnerability in the Telegram messenger function “People are Near”. The operation of the problem is similar to the methods for other programs using geolocation: by substituting your own coordinates, you can conduct a virtual triangulation and get the exact location of another user instead of an approximate one.
Representatives of the Nissan company announced a serious leak of corporate data: it happened due to a Git server with a username and password admin: admin.
Very interesting research on hacking(short version on Habré ) Google Titan hardware key used for two-factor authentication. A side-channel attack method was used to decrypt the data.
A hard-wired password was found in the latest firmware for some ZyXel network devices .