
The vulnerability (CVE-2021-3011) allows recovering the primary encryption key and bypassing two-factor authentication. Security experts from NinjaLab explained how the potential hacker attack works for Google Titan tokens based on the NXP A700X chip, but theoretically the same hacking pattern is relevant for Yubico (from YubiKey) and Feitian crypto tokens using a similar chip.
Let's talk about how the attack works and whether you can continue to trust the physical encryption keys.
About Google Titan
This security key has been on the market since 2018. It is a hardware MFA device used to physically verify a user's identity. Keys are commonly used in place of less secure multi-factor authentication methods such as verification codes sent via SMS or email.

The peculiarity of Google Titan is that, even after receiving an email password, attackers will not be able to access your data without a physical key. NinjaLab researchers also noted this: your key will be in danger only if it is stolen or lost.
Google Titan comes in two flavors on the market. One is somewhat similar to a USB flash drive - the microchip is "naked", the key works via USB and NFC. The second option is similar to car keys in the form of a key fob and works via Bluetooth.
Calculate from electromagnetic radiation
Since the inception of Google Titan, NinjaLab experts have suspected that the keys could be vulnerable to attacks through third-party, or side channels. These include, among other things, attacks based on the results of monitoring electromagnetic radiation emanating from devices during operation. Its analysis helps to identify patterns in work and gather information useful for hacking.
By observing the electromagnetic radiation during digital signature generation (ECDSA), security experts successfully attacked and cloned the secure key element - the NXP A700X chip. The fact that the chipset used in the Google Titan has become the basis for other security keys also raises concerns about other products on the market.

Among the products susceptible to the attack are:
- Google Titan Security Key,
- Yubico Yubikey Neo,
- Feitian FIDO NFC USB-A / K9,
- Feitian MultiPass FIDO / K13,
- Feitian ePass FIDO USB-C / K21,
- Feitian FIDO NFC USB-C / K40,
- NXP J3D081_M59_DF,
- NXP J3A081,
- NXP J2E081_M64,
- NXP J3D145_M59,
- NXP J3D081_M59,
- NXP J3E145_M64,
- NXP J3E081_M64_DF.
The NXP Security Response Team has confirmed that all NXP ECC Crypto Libraries prior to version 2.9 for P5 and A7x products are vulnerable to attack.
How the attack is carried out
It should be noted right away that the key can be hacked, but no one says that it is easy to do. Thus, the hacking process described on 60 pages of the NinjaLab report can become the basis for an operation in the spirit of the films about Agent 007.
It all starts with a simple attack, for example, a phishing letter. The attacker's goal is to get the username and password of the target account. This is the easiest part of the operation.
Credentials are useless without the possession of the security key, as we discussed above. This means that then the hacker will have to take care of stealing the security key from the owner, and for a certain period of time and so that he does not notice the loss. After all, if the owner notices the absence of a key, he will be able to revoke the key or register a new one, which will nullify all the efforts of fraudsters.
The successful theft of the Mission: Impossible token does not end. Further, the attacker is faced with a number of restrictions.
To use the Google Titan security key, you first need to open the case of the device. Since the attacker still needs to return the key to the unsuspecting victim (preferably in its original form), the autopsy must be done very carefully.
Experts from NinjaLab softened the plastic with a hot air gun and split the key with a scalpel. This must be done carefully so as not to damage the printed circuit board. As you can see from the picture below, the key case still loses its presentation, so there is a high probability that the situation will be saved only by printing a new case on a 3D printer. It took NinjaLab experts about 4 hours to disassemble and assemble the token.
It took another 6 hours to recover the key for one FIDO U2F account. Researchers have shown that electromagnetic radiation correlates with ECDSA ephemeral key information, which is sufficient to reveal the secret key using machine learning techniques. To recover the secret key in the Google Titan token, it is enough to analyze about 6,000 digital signature operations based on the ECDSA key used for FIDO U2F two-factor authentication when connecting to a Google account.
But, again, all this is possible only if the unsuspecting victim continues to use the key revealed by the attacker.
It would seem that all of the above will scare off any hacker who does not want to play a spy. But that's not all. The attack also requires rather expensive equipment, costing about $ 13,000, skills in reverse engineering of microcircuits, and special software that cannot be found in the public domain.
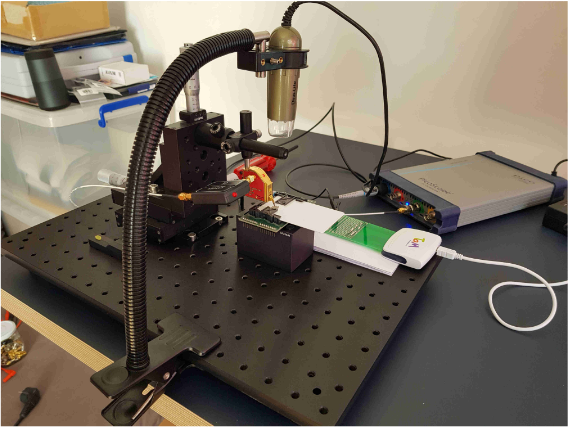
Among the necessary equipment:
- measuring complex Langer ICR HH 500-6, used for testing microcircuits for electromagnetic compatibility,
- amplifier Langer BT 706,
- Thorlabs PT3 / M micromanipulator with a resolution of 10 μm,
- four-channel oscilloscope PicoScope 6404D.
What's next
Despite the identified vulnerability, NinjaLab experts note that physical MFA keys are still more effective than alternatives. At least because you need to try very hard to crack them. And we are not talking about mass hacking of "random" people, but about targeted attacks on a selected victim. that is, if your mail does not store classified Pentagon data, you are unlikely to suffer from this vulnerability.
Ninja Labs adds that adequate security measures can help limit the potential damage caused by a cloned security key. The proposed measures include implementing an MFA system that can detect the cloned key and lock the affected account. For example, the counter mechanism described in the FIDO U2F specification .
Its essence is that the token keeps track of the operations performed and transmits the values to the server, which compares the transmitted information with the values saved during the previous operation with the same token. If the transferred value is less than the stored value, the mechanism concludes that there are several devices with an identical pair of keys. The counter mechanism is already used for authentication in Google services and allows you to block accounts when detecting activity from cloned tokens.
And of course it's worth remembering that the whole operation starts with simple social engineering attacks. This means that attentiveness at this stage will significantly reduce the chances of attackers' success.
