The vastness of the Internet has long ceased to be a safe space (if it could ever be considered as such) for the user. It is all the more unusual that many do not consider it necessary (or do not know how) to follow relatively simple rules of so-called IT hygiene.

Within the framework of this article, I would like to summarize somewhat the simplest ways to protect against various misfortunes and unpleasant moments on the way of surfing the web, so that everyone can do it simply and quickly (almost like washing your face and brushing your teeth).
Let's get started.
The nuances of the problematic
Surely everyone, in one way or another, has come across a moment when some kind of left spam, requests to borrow money and something else, starts coming from a friend's account.
Why this happens, I think, is understandable - accounts have been broken and will continue to be broken, global leaks of passwords and credit card numbers happen, perhaps, every year, and there are even more such problems of this kind, if the classic security rules are not followed.
Generally speaking, within the framework of IT hygiene, one can distinguish such relatively simple rules as:
- The presence of separate mails for serious accounts and all others;
- Using ad blockers, and ideally scripts, iframes, cookies and the like;
- VPN presence (at least free);
- Using different passwords for all sites without exception ( Lastpass, Keepass and other password managers help with this );
- Two-factor authentication should be enabled everywhere, and, preferably, not using sms , but code using applications;
- And, perhaps, such a simple but obvious thing, how not to store passwords in obvious places, be it physical solutions like a password on a piece of paper under the keyboard (or a sticker on the monitor) or somewhere in a notebook on the desktop or correspondence in a telegram.
Perhaps, if we talk about the general simplest security, for now, within the framework of this article, that's all. For obvious reasons, things like antivirus and firewall are not mentioned here.
Now let's take a closer look.
Separate mail
The oldest and simplest of the IT hygiene methods can be considered the presence of a separate mail for serious and important things.
For everything else, - including for correspondence, it is recommended to use other mail (mail), and the main one should never be "shine" anywhere - it should be as clean as possible.
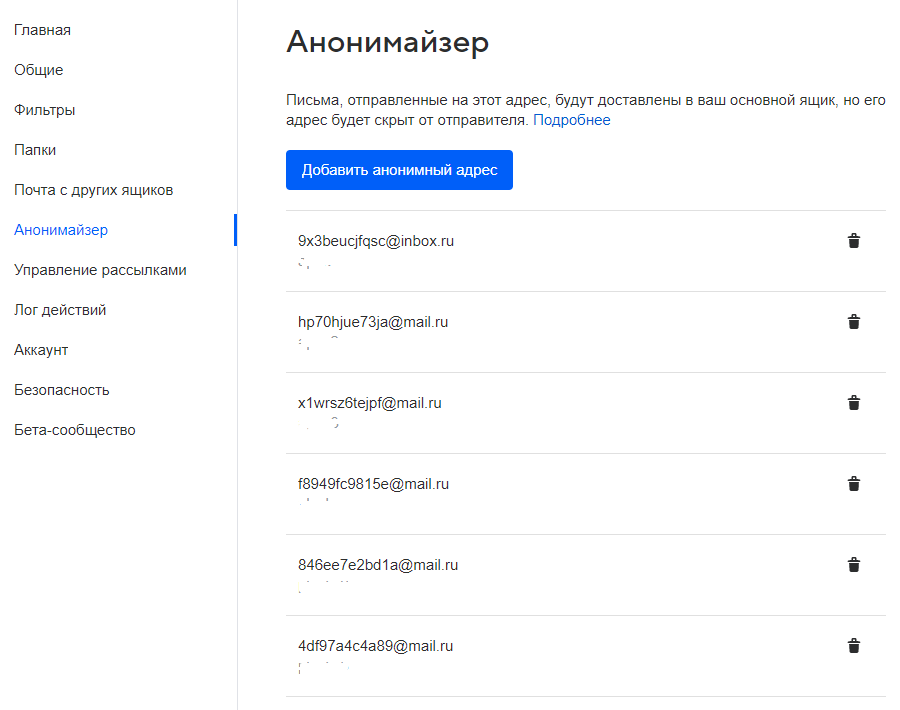
In the case of registration somewhere in questionable places, there are countless services for receiving one-time (and not so) letters. Even the same mail.ru has a built-in anomizer that generates mail like djflksdfj @ , which can and should be used for all letters, except for critical ones.
Ad blockers
By themselves, they are not entirely an element of IT hygiene, because it is not known for certain whether they collect any data and in what form, but, nevertheless, they are strongly recommended for use.
Everyone chooses an ad blocker for themselves, well, I recommend uBlock . There are almost all browsers and works like a clock. It practically does not require any in-depth configuration, it works on the "set and forget" principle.
They help not only to avoid viewing merciless amounts of ads, but also protect against certain types of malware that can carry a potential threat.
Different passwords
To protect against global leaks of the password database by any campaign, it is recommended to use different passwords for all sites in general.
This is not done as difficult as it would seem. There are, of course, many mnemonic techniques, like typing a password with a phrase in a different layout, etc., but after a couple of hundred (or even a dozen) sites, keeping all this in mind is already difficult.
The most convenient way would be to use an extension like Lastpass . It is able to generate, store and organize passwords from all sites, is available for all browsers, is simple and unpretentious to set up.

The only thing that will be very important is a correct, long and memorable master password for you. Well, there are simple rules, like typical ones: try not to log into unknown computers, or at least not remember the entered login-master password pair.
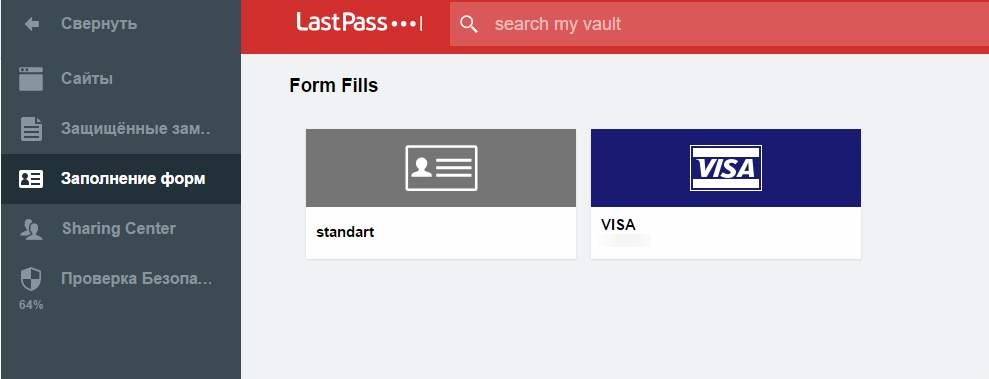
Supports everything you need, can save forms, credit card details, notes and much more. Moreover, it can be installed on a mobile device and just as quickly and easily enter passwords on it, remember application passwords, and so on.
Two-factor authentication
Probably everyone knows, at least because of the banks. When, in addition to passwords, you also enter the code from SMS, this is just it.
There is a second type of authentication, and it is more reliable - this is to use a phone app that generates codes instead of SMS.
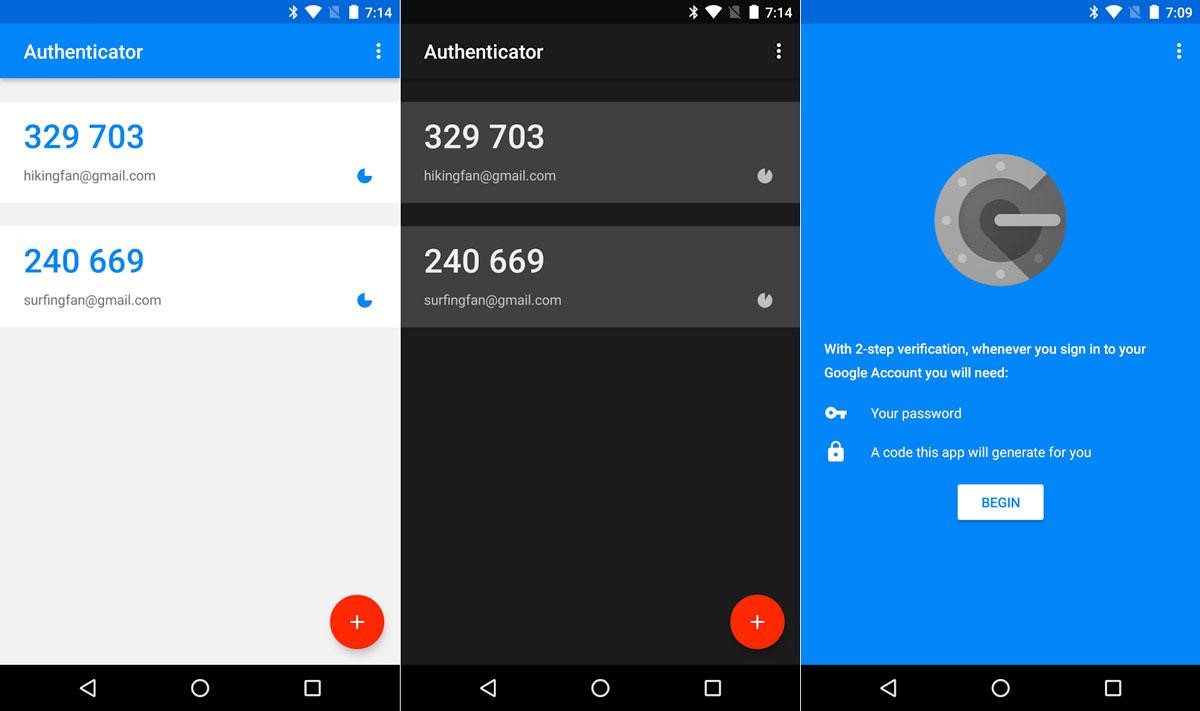
Unfortunately, not all services support it (but there are already a lot of them - this is Google , discords and much more), but where it is, you need to use it. The class increases the protection of the account and, unlike SMS, is not susceptible to standard bypasses, such as forging a SIM card and intercepting codes.
There are already a sufficient number of applications for this. Of the main, this is Google Authenticator and the same Lastpass Authenticator . Some services use their own applications ( Yandex.Key, Microsoft Authenticator ) and do not support third-party ones. It is not very convenient, but better than text messages or no protection at all.
VPN
It is the main criterion for IT hygiene. Gives privacy, protects against IP address leaks (and not only) and does not allow analytics to be tied directly to you, encrypts traffic and hides much more.

It is recommended to use the paid version ( Zenmate as an example) and completely "wrap" the system, but you can also use free solutions in the form of extensions to the browser.
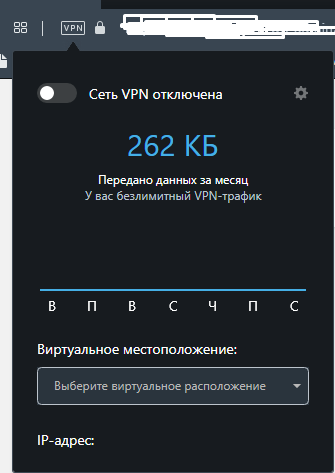
And the browser itself may be able to use it, for example, this is Opera VPN , which works at the browser level and can be turned on / off with two clicks.
Do not store passwords
For some reason, there is still a practice of storing passwords anywhere. Don't do that. Store passwords either in your head and / or in services like the aforementioned Lastpass . Solutions like stickers on the monitor, a password under the keyboard, a telegram, a notepad, etc., are very unsafe (which has already been proven many times) ideas and should not be done at all.
Afterword
As already mentioned, this is the simplest generalized basis. I would like to dive into the topic in more detail, if the post will be interesting and useful to someone.