
The customer has a main system through which he makes sales of everything. Contractors who develop and supplement this system have access to it, as well as staff from within. When it comes to hardware, everything is quite simple: a contractor comes to the data center, and a security officer from the office controls him by video. But when it comes to development, it will not work to control the "bookmarks" or take out information.
To prevent contractors with access to the combat system and the test bench from doing something malicious, control is needed either on the side of the contractor or on the side of the customer. The customer does not know anything about the contractor's people: they do not sit in his office, they cannot breathe down the back of their heads. It's hard to figure out who is connecting with what task.
Actually, then we began to implement a security system.
First and foremost, we issued personalized certificates to identify each employee. Then we deployed a terminal server through which everyone connects. The terminal server hosted ObserveIT agents to record and analyze the contractor's actions. That is, in fact, forensics, the evidence base was collected. Contractors were warned in advance that their actions were being recorded.
The second part of the challenge was to check for leaks. We caught the first malicious "spill" one week after the introduction.
What did
The customer has implemented the DLP (Data Leak Prevention) system, which allows finding insiders, well, or people who potentially unknowingly “leak” some data. It works in much the same way as antivirus heuristics: they compare the normal behavior of executable modules with abnormal ones. In this case, the behavior of specific people was compared with normal, that is, "the average for the hospital." This was not suitable for normal protection, because it identified only the simplest cases, plus it gave a lot of false alarms: the roles of people are very different.
The customer wanted more granular control and better protection. A system based on StaffCop solutions was introduced, which allows, in fact, to control directly certain people who were suspected of dishonest behavior, and to identify specific cases of fraud for them.
Actually, already on the tests, the strange behavior of one of the specialists became visible. The security officers took him into the investigation, the case was confirmed. The man was caught red-handed. This happens quite rarely, usually during tests, one of the security guards staged attacks, and the rest watch, as can be seen in the system. This is an unexpected bonus.
Why do we need protection of this class in principle
The customer's system is, let's say, too big to fail. Stopping a workflow means multi-billion dollar losses. I'm not kidding, there are things tied to prod that directly affect several hundred thousand people a day. Of course, the system is duplicated, there is a possibility of degradation to critical functions in case of very severe damage, and so on. In the production there is work with bank data, personal data and a pretty tasty base for attackers. Accordingly, the insider presumably singled out a certain segment of customers and tried to take it away.
Infrastructure has often been the target of attacks. More precisely, we cannot now judge whether these were attacks or actions out of stupidity. It was common for employees to work on weekends or on vacation and move some of the data outside the perimeter just to have access to it. They sent data in messengers, sent something to their personal mail: when it was important to do something quickly, it was economically justified, but still I wanted to beat it up for it. Almost any company has communication outside of official channels (clouds, instant messengers), and until it comes to sending specific files, it is relatively safe. Files should only be sent inside the security perimeter.
Systems of this class usually pay off within a year. We are talking about risk reduction, and each risk has a certain probability of realization over a certain period (usually a year) and cost. I would say that these systems are, rather, a hygienic thing, without which you cannot work on any product where there is something important. But often a financial justification is required, and this is where the term of one year appears. Calculation of reputational damage due to business stoppages, publications in the media after that, fines for disclosing personal data or bank data, and so on are used.
Frankly speaking, in the banking sector, we have several times caught on such implementations of people who took out data on customer balances for subsequent resale on the darknet to "break through" specific people. This is a reputation loss for the bank.
In many cases, “drain” also means a loss of competitive advantage.
How did the implementation go?
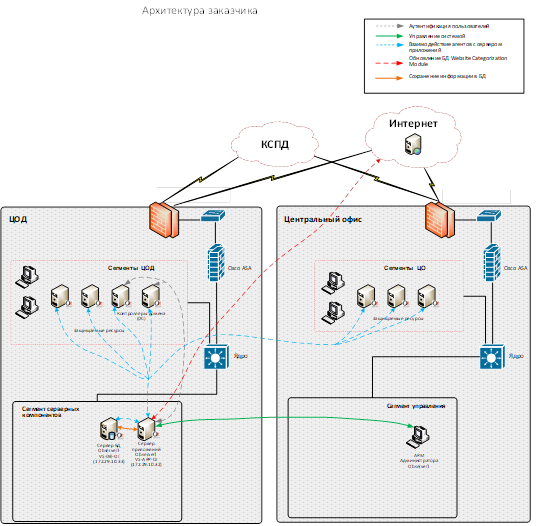
DLP was from the start of the system. After suspicions of incidents, the UAM (User Activity Monitoring) system was implemented. According to the plan, it was supposed to be implemented a little later, when the system would have reached a certain size, but due to a number of activities, the security officers decided to speed up this process. As it turned out, not in vain.
The systems are quite simple in their architecture. They are agents that are installed on end user workstations or terminal servers.
One part is usually set for everyone (we are talking about contractors and their employees), and the second (slightly more complicated) - for information security employees who have access to the first part. That is, so that they can also control each other, because the development, implementation and support of such a system must also be safe.
In general, there is a set of agents that can be virtually invisible. These are hidden or modified processes that cannot be killed. The user does not know that he has such an agent. The data is added to a centralized database. In a centralized database, the collected data can be viewed and analyzed accordingly.
The software writes metadata on top of the data. These are commands executed, windows open, keys pressed and so on - this is to simplify the search. Imagine you need to watch ten developers take action. Potential incidents, such as a server reboot, are almost always flagged up for a possible flashback that preceded it.
We work with all data streams. These are mail, web, USB media, and so on.
We chose ObserveIT as a solution. But this decision has now gone from Russia, so now a search for analogues is being carried out. And the second solution is StaffCop. DLP - InfoWatch.
ObserveIT, like StaffCop, creates a log of actions that helps to reproduce the picture of an employee's day. In normal cases, logs are simply stored on the server, and in the event of incidents, all insider activity is raised. In our case with an insider, we raised activity in a month and noticed several anomalies.
InfoWatch, like any DLP, works with content. Downloading an Excel file to a USB flash drive? The system looks at the content of the file by keywords. In our practice, there was a case when an unscrupulous employee of a large industrial company wanted to "take out" important financial data simply by renaming the file and changing the extension. He was, of course, caught.
What does DLP work for?
DLP monitors cases when something critical appears among data resting on disks or in traffic. For example, the word “contract” appears in the data stream on a USB-drive (this is how dictionary search works) or a fragment of a specific document (this is how digital prints and citation work). As soon as such an event occurs, a report is created, an alert is sent, and the security guard sees it. Sometimes a solution is required, but more often the incident is simply tagged and saved for further investigation. This often happens because the manager or one of the top managers took this risk to speed up some task bypassing the information security requirements.
We also recorded, for example, the following incident: a user enters an apartment rental agreement from a USB stream to a workstation, then edits it and sends it to another person from the workstation via a messenger. It turned out to be a private contract, it was just that one person rented an apartment to another - but the pattern was typical of malicious actions.
What does UAM work for?
UAM records and analyzes the user's actions, compares them with those usual for him or a group of employees. Various markers are used as an assessment, for example, sending commands to the server, working time with corporate applications, working on the Internet - all this helps to assess productivity and highlight risks for security personnel and management.
In the banking sector, UAM is often used to build a picture of the working day, analyze the actions that occurred at the time of an important incident, or so that the sysadmin or contractor does not “slam the door” when leaving, leaving the crown task for sale with a deadline of three to four months. UAM monitors how critical actions the user performs and helps restore the entire chain of actions.
That is, security personnel see all data on a workstation, even personal data?
Yes. For example, if you buy a ticket on a business trip and enter your personal credit card number, then you show it to IB.
Usually, at the enterprise level, when hiring, an additional agreement to labor stipulates that only work data is processed at workstations, that is, personal data should not be there.
Screenshots from StaffCop.
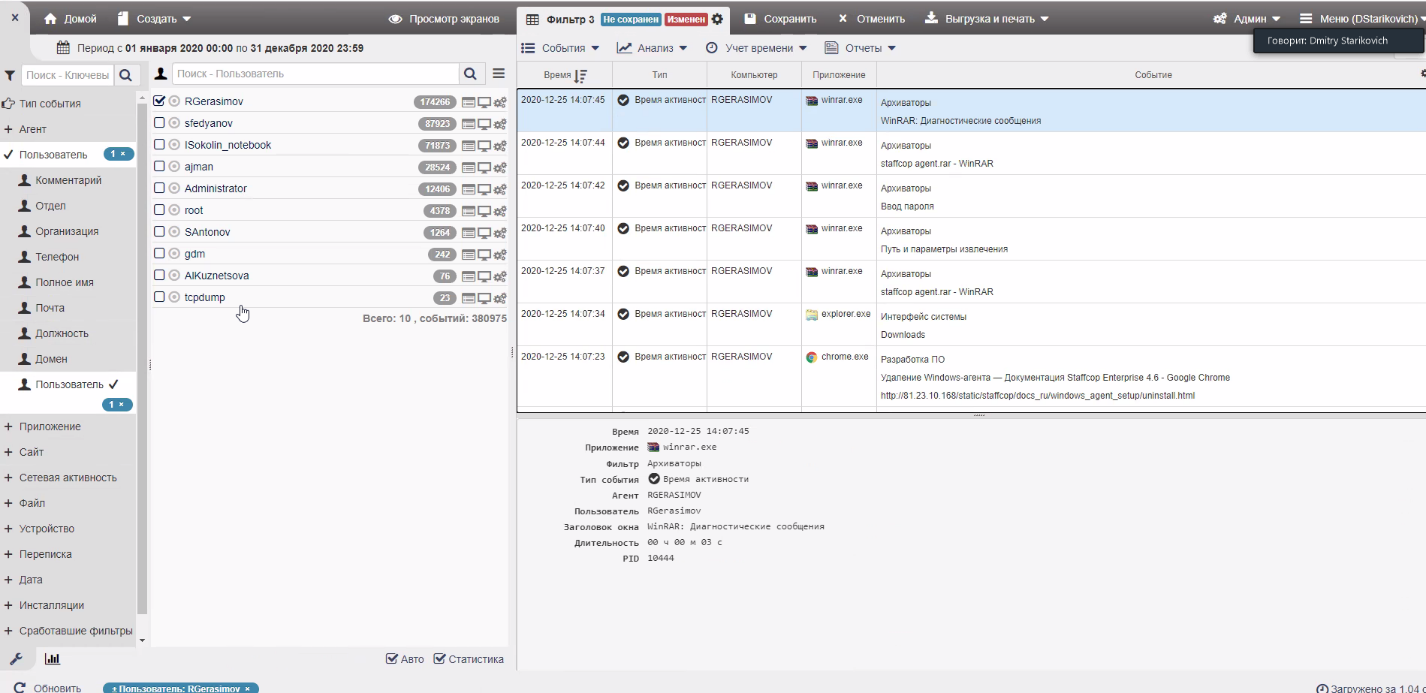
A log of user activities at his workplace, where we can understand what applications the user worked with, what exactly was on the screen at that moment.
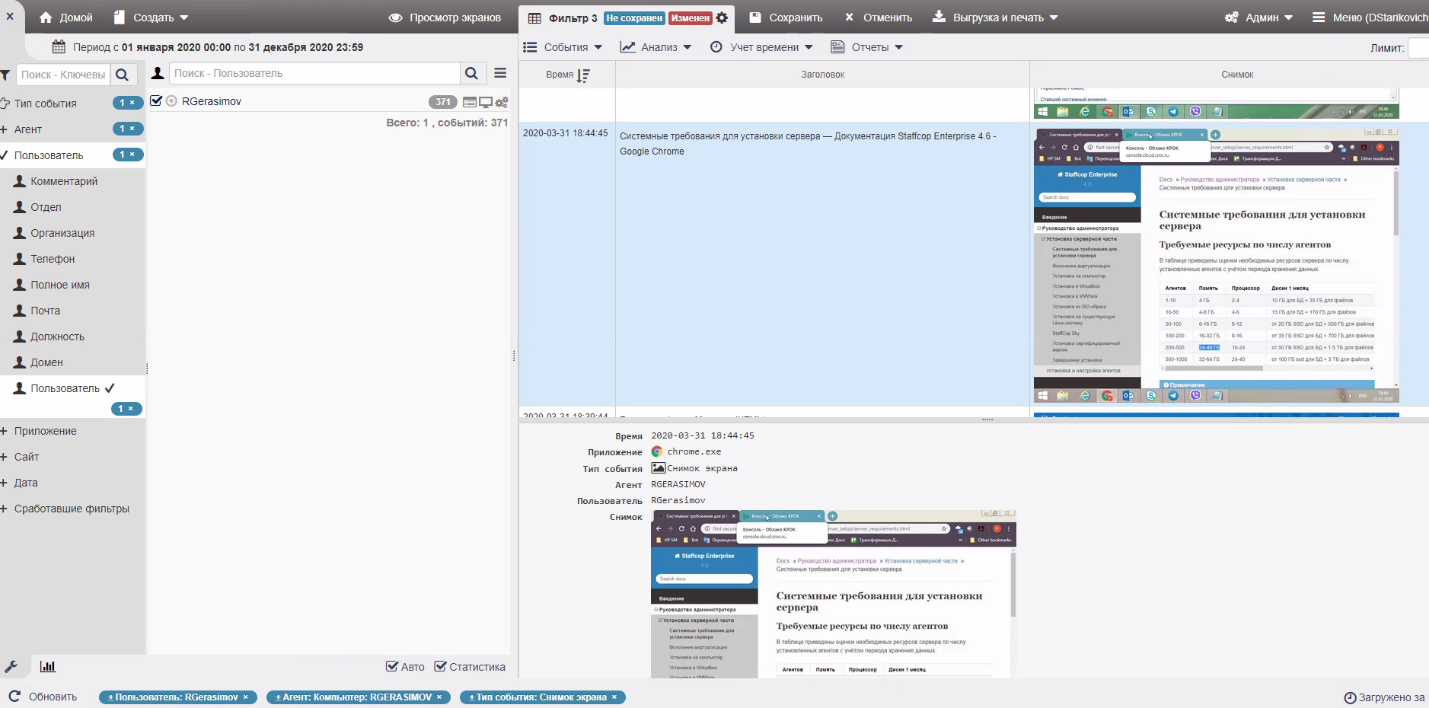
Screen of the user's screen at the moment of a certain action.
For example, screenshots from another Teramind UAM system.
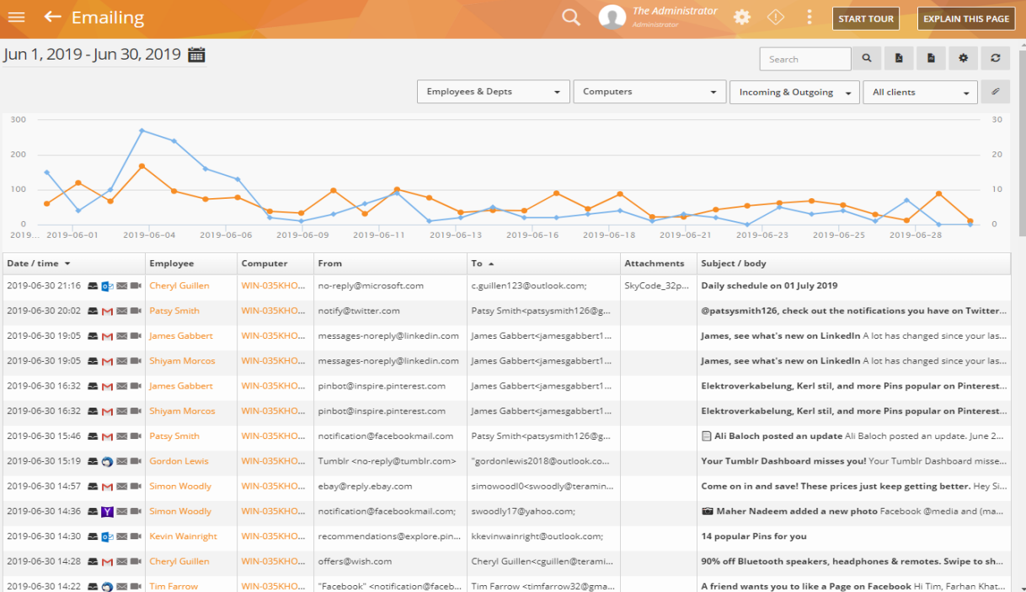
A behavioral analysis screen showing predictive and situational analytics based on machine learning, regression analysis, and a risk assessment algorithm.
Creating a behavioral profile taking into account user activity, data template and other attributes (time of day, schedule, assigned project, etc.) helps to detect anomalous activity in applications, web traffic, file operations.

A screen of the reporting system, where you can track potential insiders, the departments where they work, as well as applications through which a leak can occur.
How did people react?
Employees - nothing special. Contractors - easily accepted the new rules of the game. But for them, nothing has changed, that is, since they were only associated with the NDA with the customer, so there was also an additional method of control.