
Each company has its own secrets. Perhaps any application and service owns confidential information such as usernames and passwords, license keys, database login credentials, etc. - which must be hidden from unauthorized persons.
One of the most important categories of data stored by modern applications is TLS certificates , which allow encrypted transmission over HTTPS. The good news for Traefik Enterprise users is that it is now easier than ever to manage sensitive data thanks to Vault support in Traefik Enterprise 2.3.
Vault is an open source tooldeveloped and maintained by HashiCorp, offering a secure and encrypted central repository for sensitive information. Vault in Traefik Enterprise 2.3 can be used to manage certificates in two ways. First, Vault can be used as a key store for certificates. Second, Vault can be a certificate resolver, which allows it to dynamically generate certificates on the fly. Let's look at both use cases.
Using Vault as a Key Store for Certificates
Traefik has long supported key-value repositories such as Consul, etcd, and ZooKeeper. Vault provider for Traefik Enterprise 2.3 and later can connect to Vault in the same way, using it as a key-value data store for storing and retrieving TLS certificates.
The first step is to configure the Vault secrets mechanism for use with Traefik Enterprise. Traefik Enterprise currently supports the KV Secrets Engine - Version 2 , which is currently the default engine and is easily enabled from the command line. It is recommended to use a separate KV store for TLS certificates, and remember that all certificates must be base64 encoded and stored in the root of the KV secrets engine.
Further, it remains only to include the Vault Provider in the static configuration of Traefik Enterprise. It only takes a few lines of code, and a typical example (in YAML) might look like this:
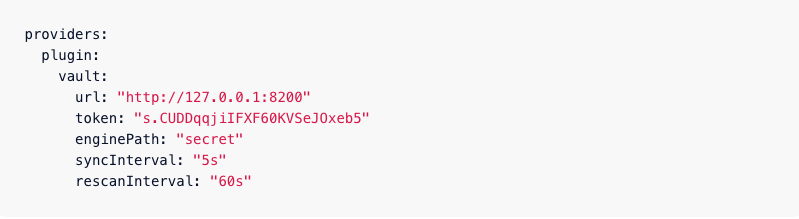
This snippet points to the URL of the Vault server and sets the token required to authenticate with it. (Currently, the Vault only supports token authentication.) It also specifies how often the provider will fetch data from the KV Vault.
That's all! Once configured, Traefik Enterprise recognizes certificates in the store for processing. And as usual with Traefik Enterprise, the configuration is updated automatically whenever you add or remove certificates from the Vault.
If you would like to learn more about how to set up the Vault Provider for Traefik Enterprise, check out the documentation .
Using Vault as a PKI Certificate Resolver
Experienced Traefik users are aware of support for automatic certificate generation using the ACME protocol and compatible service providers such as Let's Encrypt . Traefik Enterprise 2.3 adds new, additional tools for automating the process of generating certificates in the form of support for public key infrastructure - Vault Public Key Infrastructure (PKI) .
The Vault PKI secrets mechanism includes built-in authentication and authorization functionality that allows certificates to be generated on the fly, without the traditional process of manually generating keys and submitting them to a Certificate Authority.
This automation is especially valuable in dynamic, microservice-based environments where services tend to be short-lived and containers are quickly created and destroyed on demand.
Configuring Vault as a certificate resolver is almost as easy as configuring the Vault Provider discussed earlier. After installing Vault with PKI Secrets Engine enabled, configuring the feature requires adding just a few lines to the static Traefik Enterprise configuration. For example:
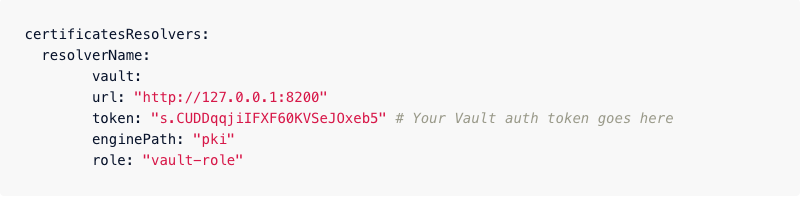
After completing the settings for the certificate resolver and assigning it to Routes in Traefik Enterprise, Vault will start generating certificates for requests that match the patterns. To learn more about how it works, refer to documentation .
There is also a handy user guide that walks through the process of deploying a simple TLS-compliant service from Vault to Kubernetes.
Keep your data safe with Traefik Enterprise
Traefik Labs is proud to offer Vault support in Traefik Enterprise as further proof of our commitment to deliver the best-in-class features that security organizations demand. Using Vault to manage sensitive information is a step forward in securing your network; using Vault with Traefik Enterprise makes this step even easier. Using Vault to manage sensitive data is a step forward in securing your network; using Vault with Traefik Enterprise makes this step even easier. Start your 30-day free trial and see how Traefik Enterprise can help make your infrastructure more flexible, reliable and secure.