2 years have passed since Russia got the opportunity to deploy IoT systems based on NB-IoT technology. Counters that send their indicators to housing and communal services, automatic micro-weather balloons far from civilization, smart agriculture - all this will soon become a part of everyday life.
It is important that neither the device system, nor the data it collects and transmits, is used against the users of the system. If you are interested in how the NB-IoT standard protects them from network attacks, then I invite you under cat.
About attacks
As already mentioned, in the field of collecting and processing data using the IoT, attacks aimed at reading data (wiretapping a channel, gaining unauthorized access to data) and their substitution are of primary interest and concern. To prevent eavesdropping, encryption is used, and against spoofing, packet authorship verification mechanisms (authentication) are used, for example, a digital signature (which is also an encryption task), or the method for IoT systems described in [1] .
It is no secret that today ordinary computers and smartphones are capable of ensuring the encryption strength of a communication channel encryptor such that breaking it on a modern supercomputer will take time exceeding the lifetime of the universe, but such crypto resistance has a price - the computational encryption time and the power consumed by the device. A smart meter, one battery in which should be enough for 10 years of continuous operation, and will not work for a month if every day only counts the points of an elliptical curve. Speed is also a problem: you do not need a lot of computing power to perform simple operations for taking and sending readings, which cannot be said about reliable encryption.
Standard methods of protecting information from network attacks for low-power devices do not work due to non-standard restrictions on the operations allowed for these devices. On the other hand, the correct construction of the network imposes restrictions on the attacker, and depending on the limitations of the standard, the most suitable lightweight algorithm is selected ( [2] ).
Briefly about NB-IoT
Let's talk about the NB-IoT standard: why is it needed, what it describes and how what it describes works. After that, let's find out what restrictions are imposed on the network.
NB-IoT is designed to serve networks of simple recording devices (Terminal Devices, or OU) by cellular operators. The work of the OU is to collect some data and, at predetermined intervals of the day, transmit it to the processing server, which will dispose of this data further. It is the transmission technology, from physics to the network, that is described in the NB-IoT standard.
In NB-IoT, there is no network connectivity between the internal network of endpoints and the external network of the processing server. In other words, the operator separates the OS network from the external network (in fact, from the Internet), and acts as an intermediary between the two networks.

Operator's tasks as intermediary:
- maintain a radio channel of communication with each OS,
- transfer data streams from the processing server to the OS and from the OS to the server,
- provide access to reading streams and control to the handler server and only to it.
That is, the payload passes through three separate networks: a network of devices, an operator's infrastructure network, and the Internet. An attacker can eavesdrop or substitute when his device is in one of these three networks, so the question of the security of the data stream transmitted via NB-IoT is divided into three: its security in each of the networks separately.
Omitting the issue of data security within the operator's network and leaving it on the operator's conscience, and consider the other two.
Data security on the external network
Let's put ourselves in the shoes of an attacker. Before us are 2 communicating hosts: a handler server and an interface for accessing the data collected by the OU provided by the operator specially for it. We are not interested in what is behind this interface - it is part of the provider's infrastructure.
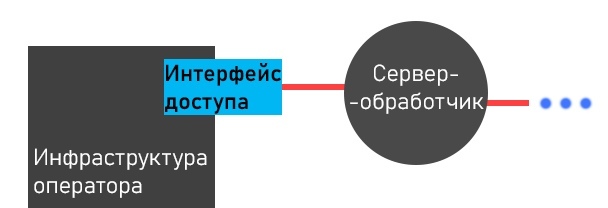
The communication between the handler and the operator interface is the usual communication between two hosts on the Internet. As mentioned earlier, they are powerful enough to provide themselves with cryptographically strong transmission channels, therefore, the issue of data security from an OS in an external network is of no interest.
Data security in the operator's network
Let's now look at the internal network.
First of all, the network is isolated in a certain sense: there is no network path to it from the outside, there is only the possibility of direct interference in its physics. Physical communication between the OS and the operator is carried out by a radio channel on one of the allocated frequencies. Network topology is a set of direct connections between the OS and the operator, and all of them are static - pre-installed. This means that an attacker who wants to interact with a node in this network must impersonate the opposite node, and so that the real node does not detect traffic imitating it. In the case when traffic is transmitted over the radio wave, this in itself is a non-trivial task.

In addition, we will still encrypt packets and authenticate when connecting.
Important!
The Operator is not obliged to provide encryption of traffic in the OU-Operator network. Encryption is possible as a separate service, which is paid for by an organization deploying an IoT system using an NB-IoT operator.
Op-amps are not powerful enough to use heavy cryptographically strong encryption algorithms, and the strength of lightweight algorithms is noticeably lower, which, among other things, means that an attacker needs relatively few packets to analyze before he can figure out the algorithm key.
In NB-IoT, the effectiveness of lightweight encryption algorithms is achieved by the fact that the exchange of packets between the OS and the operator, simply by concept, occurs rarely: packets per day (more precisely, about the "scarcity of traffic" necessary for efficiency, see [2]) It turns out that an attacker simply has nowhere to take a large base of packets for analysis in a short time: any encryption algorithm in a network with low traffic will last longer than in a similar situation in a network with frequent traffic.
Outcome
NB-IoT is a completely reliable service standard. Substitution of traffic in the internal network (standing in the middle) is an expensive enterprise due to the need to hide the radio signal of the nodes from each other. In addition, standing in the middle cannot be started until the node authentication keys are known, which are sufficiently reliably protected by a lightweight encryption algorithm, like all data transmitted from the OS to the operator.
Attempts to read or "stand in the middle" in the operator's network and in the external network will also fail, since the devices on these networks have enough computing power to securely encrypt traffic. On the other hand, if an attacker wants to compromise the data from the OS, he will most likely aim through an external network: the traffic in it is the least dependent on the operator and the customer is responsible for it, who, not being a large company, spends much less money on the security of its network than operator. Therefore, understanding the issue of the security of your data, you must first of all study how the organization that provides the service directly to you approaches the security problem.
Sources and links:
- Yuxiang Feng, Wenhao Wang, Yukai Weng, Huanming Zhang, A Replay-Attack Resistant Authentication Scheme for the Internet of Things
- Saurabh Singh, Pradip Kumar Sharma, Seo Yeon Moon & Jong Hyuk Park: Advanced lightweight encryption algorithms for IoT devices: survey, challenges and solutions
- 3GPP Release 13 Specification - NB-IoT Specification
- The first article from the cycle on the implementation of NB-IoT from MTS - I recommend this cycle as the first step in studying NB-IoT