This article was written in order to tell the reader what scramblers are, identify their areas of application and touch on some practical subtleties, as well as reveal the secrets of the scrambling algorithm.
Why and why?
Sometimes it becomes necessary to encrypt traffic without resorting to methods that require a lot of time and resources to encrypt and decrypt, as well as to implement the algorithm. This happens when we try to protect data from users or primitive Trojans with sniffers (traffic analyzers), but this data is not worth resorting to serious encryption methods, since we do not need high cryptographic strength. From the side of communication methods, it is sometimes necessary to reduce the level of radiated interference by distributing energy evenly, and to increase the reliability of synchronization of devices. Scrambling copes with these tasks.
What is a scrambler?
A scrambler (from English to scramble - to mix, encrypt) is an algorithm developed for bit-by-bit sequential transmission of information, which allows encrypting a digital stream in such a way that the output is a sequence that has the properties of a random: equiprobable occurrence of zero and one. This is what makes it possible to reliably isolate the clock frequency and constant power of the transmitted signal, which gives the reliability of synchronization. It should be noted that such a stream conversion does not change the transmission rate, and is also reversible, that is, the data is restored by the reverse algorithm.
How it works?
We have a transmitting side, on which scrambling is performed, as well as a receiving side, on which descrambling is performed, that is, the reverse operation. The original sequence is fed to the input of the scrambler, and also it is it that is selected by the descrambler from the received encrypted sequence.
The main part of the scrambler is a linear n-stage feedback shift register that generates a pseudo-random sequence (PRS) of maximum length . The main operation performed during encryption is addition modulo 2, that is, XOR (exclusive OR).
Scrambler types
: (-) (- ). , , .
-
, , . , . , .
.
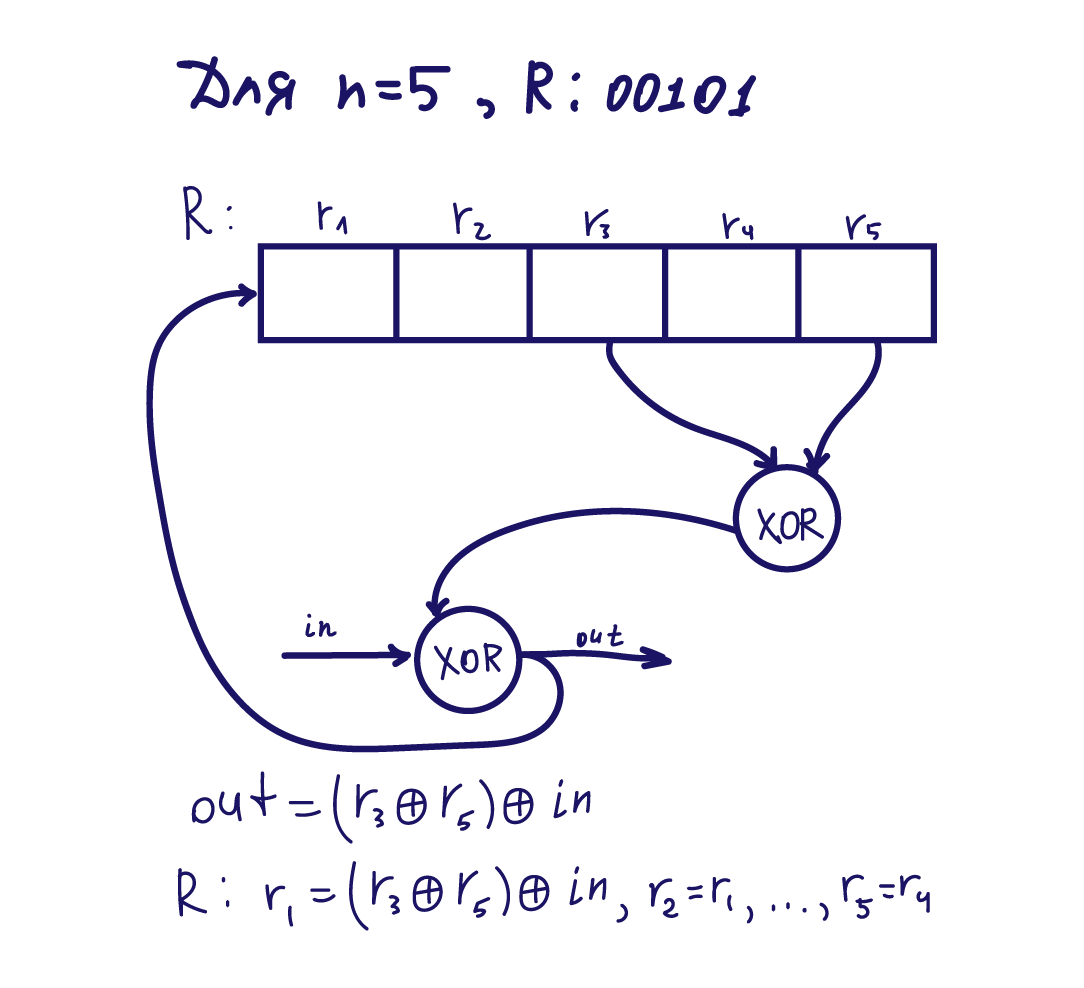
, " " . - , . , n ( n – ), 2n . , k . , .
-
, , – . , , .
.

, .
- , . , , , , , " " . , . , RSA -.
– – . . , , . - , n , ,
. , .
, n , .
. , , n, 2 . , ().
:
n
,
,
1
,0
–
, , 15-
1000000000000011
. 000000000000011
, : .
?
– , -, , .
, .
Nevertheless, scramblers are widely used today, both because of the simplicity of their implementation and because of other obvious advantages of this algorithm.