
What is this article about
Good day, reader. In this article I would like to talk about one of the most common symmetric encryption algorithms - the AES algorithm.
Introduction
80- DES (Data Encryption Standard). 90- . , 56 . , .
1997 NIST (National Institute of Standards and Technology,) . :
128- ;
3 (128, 192, 256 ), ;
, , ;
, ;
, AES – Advanced Encryption Standard, Rijndael ( AES). , . , , , .
, .
, AES , F(28). , , , . :
xor. , P = { p7, p6, p5, p4, p3, p2, p1, p0 } Q = { q7, q6, q5, q4, q3, q2, q1, q0 } R = { r7, r6, r5 , r4, r3, r2, r1, r0 }, ri = pi xor ri .
. : p(x) = p7x7 + p6x6 + p5x5 + p4x4 + p3x3 + p2x2 + p1x + p0 , F(28) m(x) = x8 + x4 + x3 + x + 1. , , F(28), p(x) q(x), m(x) p(x) q(x), r(x) = p(x)q(x) mod (m(x)), r(x), 8- F(28).
AES c 128 .
16 , 16 , , 16 . 4x4 — state. state 2-4. , :
- KeyExpansion;
- state ;
9 , :
· SubBytes
· ShiftRows
· MixColumns
· AddRoundKey
, :
· SubBytes
· ShiftRows
· AddRoundKey
:
SubBytes - state S-box. b = (x, y), x 4 b, y — 4 . S-box 16x16 : b' x y S-box b.
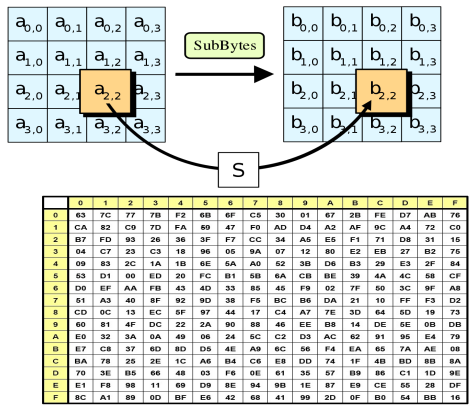
ShiftRows — state. , 1 , 2 3 .

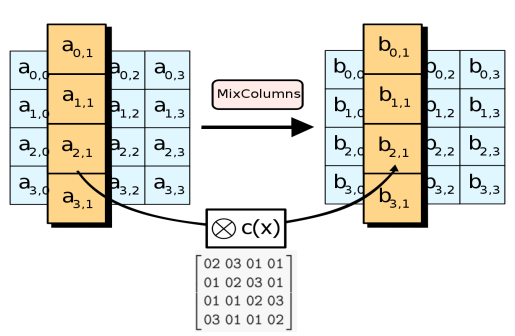
MixColumns — state . state. , .
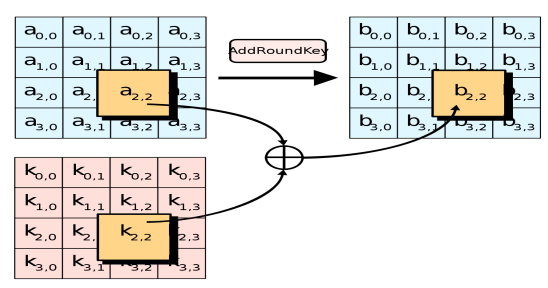
AddRoundKey — state XOR.
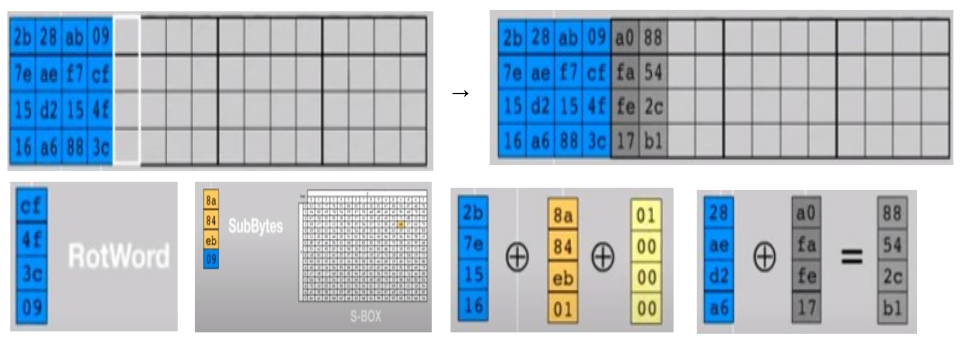
KeyExpansion — , . 44 (wi): 4 4 10 . , 1408 .
Rcon :
.
i 4, wi =SubBytes(RotByte(wi-1 )) xor Rconi/4 .
: wi = wi-4 xor wi-1 .
RotByte : { x0, x1, x2, x3 } → { x3 , x0 , x1 , x2 }.
, 2 .
, , . , :
- KeyExpansion;
9 , :
· AddRoundKey — state ;
· InverseMixColumns — state;
· InverseShiftRows — state;
· SubBytes — state InverseS- box;
:
· AddRoundKey
· InverseShiftRows
· InverseSubBytes
AES
state— 128 3 AES. : AES-192 192 — 12 , AES-256 — 256 14 .
. , AES-256 . , , .
, , Nk - , Nb - Nr - .
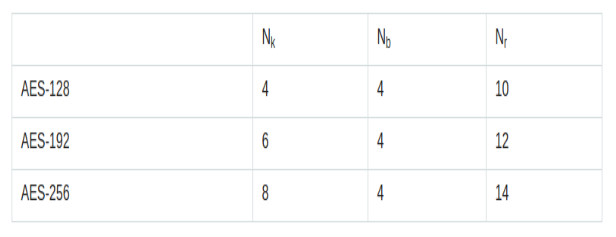
AES
. 2 .
.
, . , , .
, ( ), AES , , .
:
· , . , , , .
· , .
.
. , , .
:
· — .
· .
, - ?
, .
32- : w0, w1, w2, w3, …, w40, w41, w42, w43, w0, w1, w2, w3 - 128- AES, w40, w41, w42, w43 - . wi = wi-4 xor Fi(wi-1), Fi - , KeyExpansion. w0, w1, w2, w3 .
, AES-128. : wj = wj+4 xor Fj+4(wj+3). j = i - 4 . , , w40, w41, w42, w43 ,c w0 .
AES-192 AES-256. , 256- AES, AES 2256 2128, .
AES
:
— .
— .
, : , , square — .
Byte-oriented structure, which gives good prospects for implementing the algorithm in future processors.
High performance across multiple platforms.
Conclusion
In this article, I tried to describe in detail the principle of the AES algorithm. I would like to note once again that the algorithm really deservedly won the competition for a new standard due to the large number of its advantages. Thank you for your attention.