
Many, as I think, upon hearing the phrase "cyberattack", represent cybercriminals who steal many millions of dollars while sitting at home, or a group of Russian hackers who help a candidate advance in the election race, or, at worst, an image pops up in their minds a cracker who picks up a password for a VKontakte or Instagram account, or maybe even Trump's Twitter password . In fact, since the late 20th century, side-channel attacks have become popular in the cryptanalyst community. I want to talk about such encroachments in this article.
Introduction
, (side-channel attacks) - , , . , , , . , : " , ", .
: , , , , , , .
, , , , , , , .
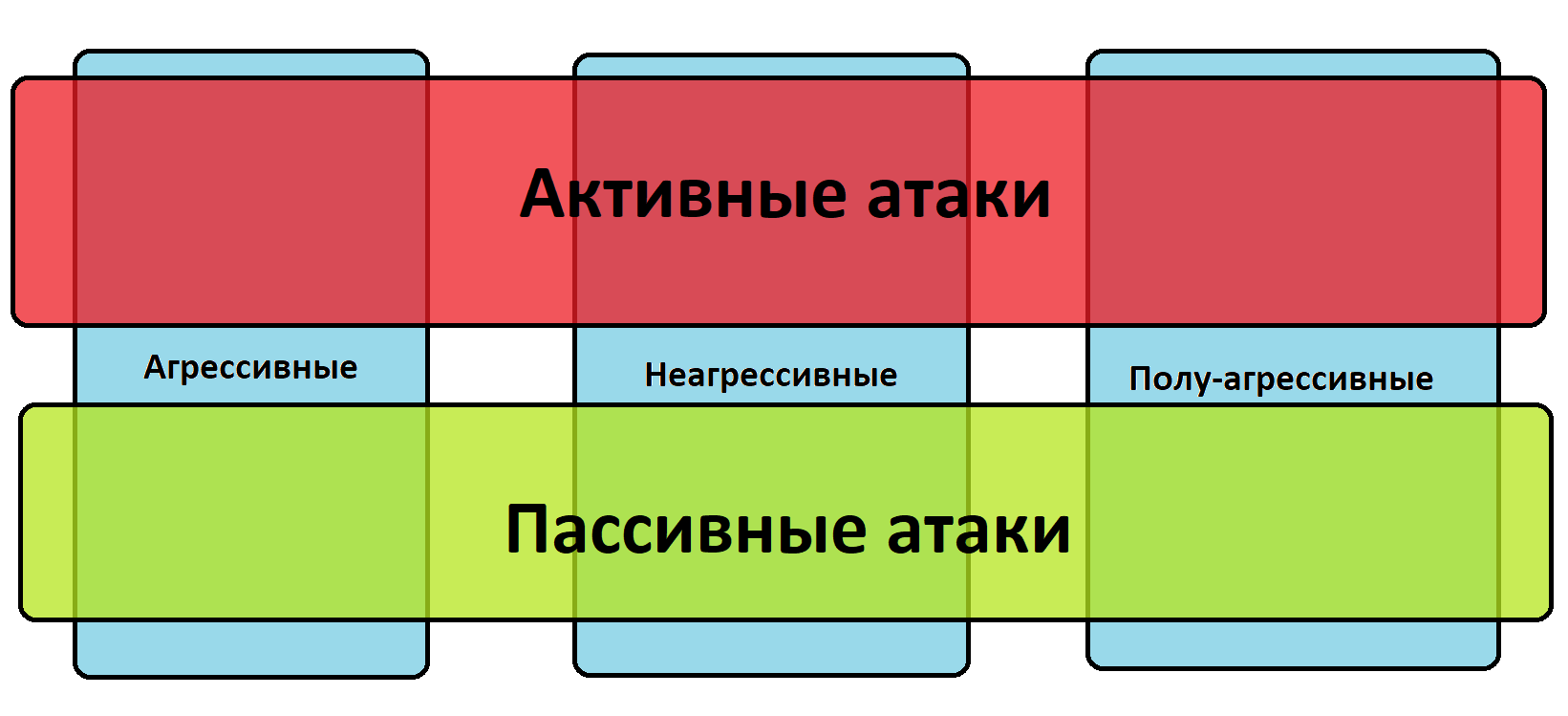
:
(passive) - ,
(active) - , . .
:
(invasive) - .
(non-invasive) - , . , . , .
- (semi-invasive) - , , , , .
:
(simple) - .
(differerntial) - , .
(Data remanence atacks)
- , . , , , , - . , .
(Differential fault analysis)
, , . , / , , , , . - , , .
(Optical attacks)
- , .
RSA, AES.
, . . - , .
(Electromagnetic attacks)
, , , .
, , , , .
, - . , , .
, , . .
(Power-monitoring attacks)
(correlation power analisys) , . , .
2 :
(simple power analysis), .
(differential power analisys) - , , .
, , . . , .
, , , , . , , .
, , . , , , , . : , .
(timing attacks)
, , .
, , . , , , , .
, .
. 1996 RSA.
, - , N - RSA, d - . d, , . , . . , . , .
, . 2% 10% .
- , . , , .
(acoustic cryptanalysis)
, , .
, , . , . , .
. , , , " ". BIOS. .
, , CPU , . , , .
3 :
. - . , , . .
.
, , - . , , .
Side-channel attacks(wikipedia.org)
Timing Attacks on RSA: Revealing Your Secrets through the Fourth Dimension
Fansmitter: Acoustic Data Exfiltration from (Speakerless) Air-Gapped Computers
Optical Side Channel Attacks on Singlechip