Content
History reference
The essence of the Schnorr protocol
Schnorr signature scheme
Why are Schnorr signatures considered better than ECDSA?
Comment from author
This article is intended for people who are already familiar with the basics of information security. If the words Proof of Knowledge Protocol, Public Key Cryptosystem are not spells for you, you're welcome!
History reference
The Schnorr circuit was invented in the 1980s. Klaus-Peter Schnorr. Klaus Schnorr is a German cryptographer, academician, at that time professor and researcher at the University of Frankfurt. Before the publication of the circuit itself, Klaus Schnorr got confused with patents, which made it difficult to use it directly until 2008.
In 2008, the same year that Satoshi Nakamoto introduced Bitcoin to the world, Klaus Schnorr's patent expired. Even though Schnorr signatures were already usable, Satoshi Nakamoto chose ECDSA for Bitcoin. This is due to the fact that the Schnorr scheme was not yet standardized and widely used.
Although ECDSA is often considered a failure by cryptographers, it is still used today. By the way, DSA, the predecessor of ECDSA, was a hybrid of El Gamal and Schnorr schemes, created exclusively to circumvent Klaus Schnorr's patents by the US National Institute of Standards and Technology (NIST). After his appearance in the Coderpunks mailing list, what is called an intelligent shit began, and Klaus Schnorr began to defend his patents even more actively.
The essence of the Schnorr protocol
Generally speaking, the Schnorr scheme is one of the variants of zero-disclosure proof protocols. We prove that for some public key h, which is an element of a group with a fixed generating element g, a secret x is known such that g of degree x is our public key h.
, , .. .
k q, . I .
.
s .
.
, r - , .
, - m ( , ), I , .
r ( ): -, . r pk. - 2010- , , , , , Helios.
public key (pk) - , .. n ( 33 ). , 2 , .. 2n (64 ). .. .
(, , k). , k . , .
ECDSA?
, ECDSA .
ECDSA
, ECDSA , , ECDSA . 2009 ECDSA x3+7 , - , . ECDSA . , .
. ? :
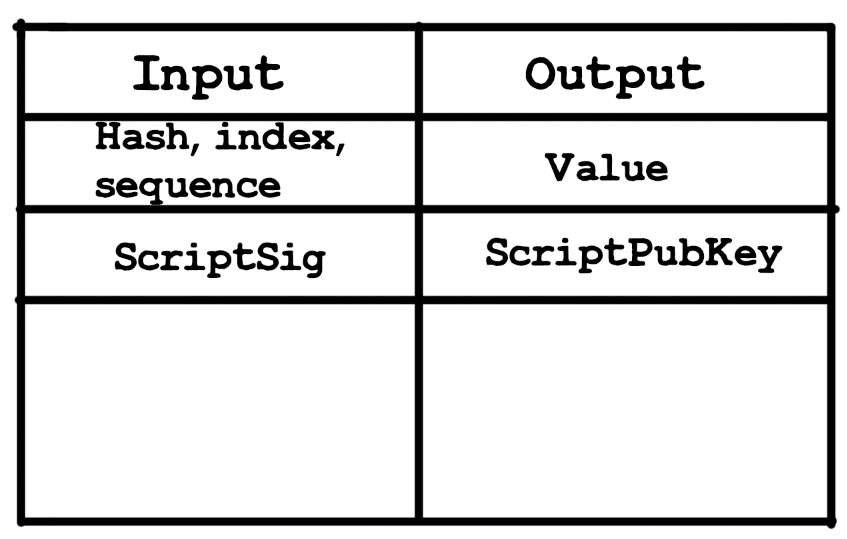
, , sequence scriptSig - , , .
value scriptPubKey - , , , .
, - ECDSA . , .. ?
ECDSA . , , .
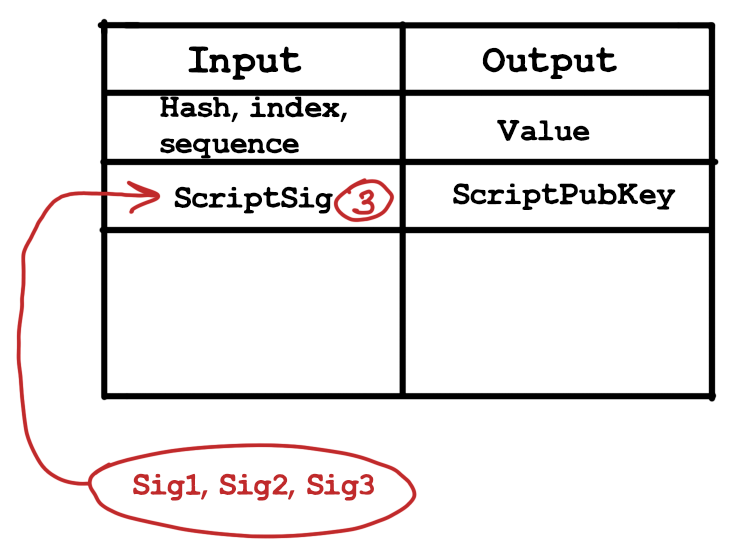
ECDSA
, . , , , . , , , , , . , .

ECDSA
: scriptSig , , scriptPubKey, . . , ( , ). . ECDSA, , n , m .. .
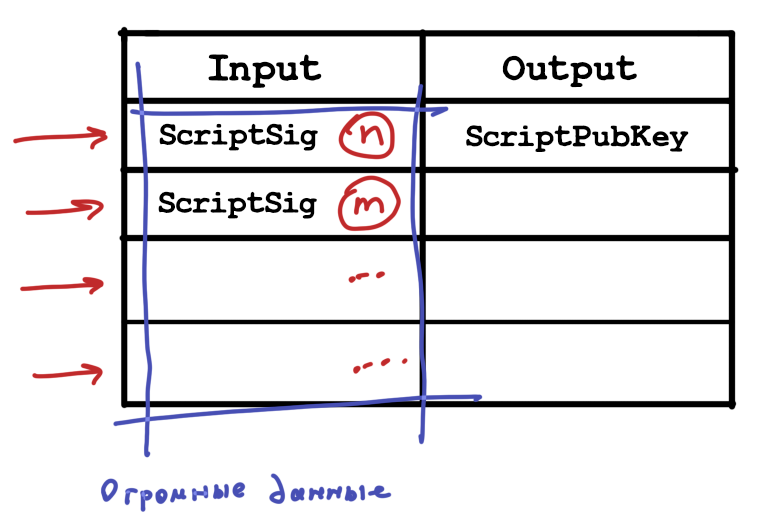
?
. ? 4 , ECDSA , 4 . , , .
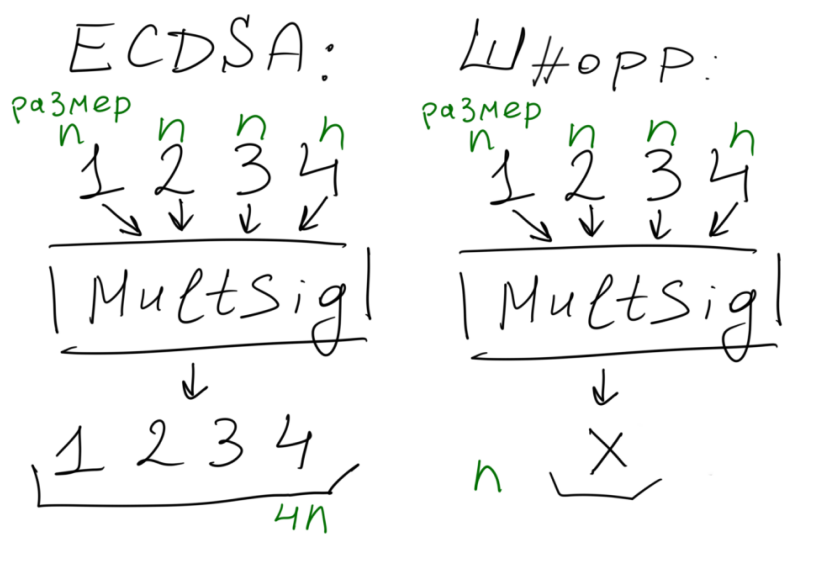
, , , .
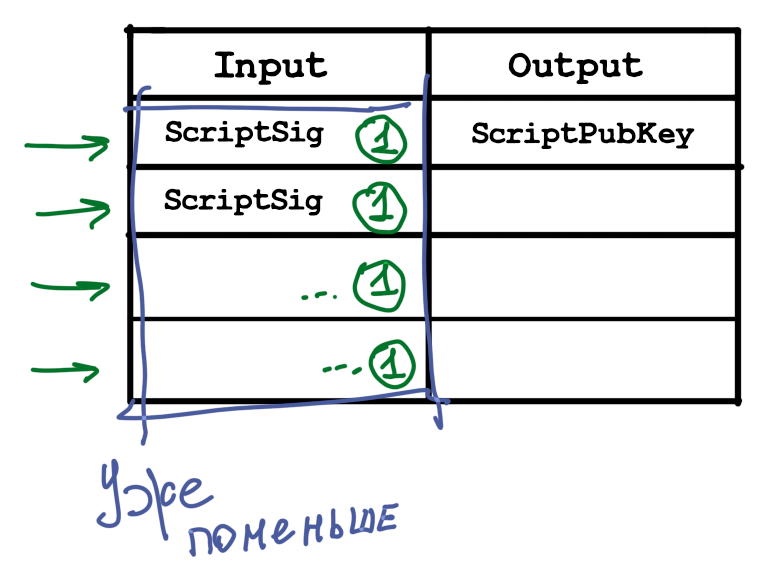
, , , . , .

, , . , , , .
. ? , . , . . , , . , , . , .
The Schnorr scheme is one of the most efficient and theoretically grounded authentication schemes. It turned out to be not very popular due to the lengthy patent, which lasted until 2008. Although the scheme has undergone some changes since its inception, its basic ideas have remained intact and are highly valued in cryptography.
Sources
Article Schnorr Signatures and the Inevitability of Privacy in Bitcoin
Wiki
ITMO Seminar on Schnorr Scheme
Lecture on Schnorr Signatures in Bitcoin