
Internet of Things, IoT, Internet of Things- a network of electronic devices equipped with embedded technologies to interact with each other and the external environment. The IoT concept has become an integral part of our daily life, providing users with unique experiences ranging from home automation solutions to medical devices. Ultra-fast wireless networks and a modern electronic base allow IoT devices to efficiently and easily collect, process and transfer large amounts of data. Advances in microelectronics coupled with low power consumption have made it even more possible to use IoT devices in remote locations requiring minimal physical surveillance and maintenance. While IoT devices seem harmless, they are not without security and privacy concerns.as there are many threats and vulnerabilities in the modern IoT structure.
, , . McAfee , 176 . DDoS- , Mirai-, 2,5 . , . 2020 26 IoT . , -, IoT , . , , . , , . , , , IoT, .
IoT , , . , . , , . , . ( - ) , ( ), , , . . , , , . , IoT . . 1, IoT :
. (, ) . , . ( , , ). , . , . , « » (DoS) (DDoS), . ( «») , . . « » 2019 — . 105 IoT-, 276 IP-.
-
IoT . , :
, IoT, . , , . , DoubleAgent , .
, . , IoT . “ ”. .
, , IoT . hardware- . 1, IoT. .
IoT . Trusted Platform Module (TPM- , , , ). TPM , , . TPM (dTPM) , . , ARM TrustZone Intel Software Guard Extension (SGX) SoC (system on a chip), , , . , , AEGIS Ascend, . , , .

TPM , , , , , IoT . , , , , , . , . SIEM-(Security information and event management). , , .
(PMU), SoC. PMU - (HPC). , HPC PMU , ( ), , , . PMU ARM Intel x86 , Linux Perf tool. . PMU , SIEM-, , , . , , , PMU , , . . , PMU .
NYU Polytechnic School of Engineering, Brooklyn, New York, USA DDoS- BRAIN (BehavioR based Adaptive Intrusion detection in Networks). DDoS-. DDoS-, . HPC , . DDoS- (DDoSDE), , . DDoS- (DDoSPI) , IP- ( ) HPC, .
, ( ) , , . , , . :
, , HPC. . -, . -, , . , ( .)
, .
( ) . , .
. , , , .
HPC , . . , HPC , . , , , , . , HPC .
HPC +ML . , , , . , . , . ML , , Virtex 7 . , OneR , 81%.
- , , - , , , IoT.
, . , , , - , . , , , , . , IoT . ? , IoT , "" . - .
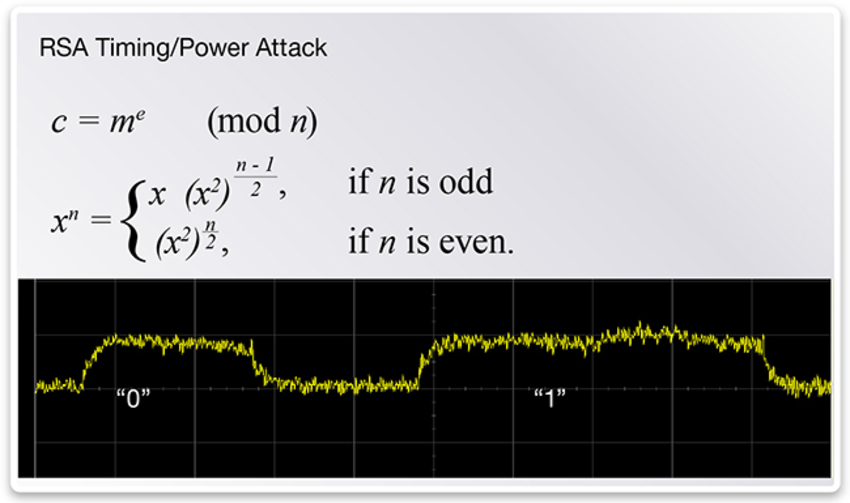
, . . IoT .
, () . , , . . . IoT , , , .
, IoT , .
, TPM, . , plug-and-play IoT, , .
, . , HPC / . , , , . / , , . .
, , , . , , , , . , .
. , . , . , - . .
IoT . . / . PMU , , .
With the advent of IoT devices and IoT applications, it is imperative to provide a reliable and secure platform for this area to maximize protection against current and future cyber attacks. Most existing solutions are inappropriate because such protection methods do not provide broad and reliable coverage. Therefore, it is necessary to use both hardware and software solutions in a hybrid manner. Hardware protection for IoT devices has proven to be effective and versatile. However, there is no doubt that further research is needed to develop appropriate security mechanisms for lightweight IoT applications.