In this article, you will learn
Who is your block cipher.
What principles did the creators of the algorithm adhere to?
How does the key preparation process look like?
Work algorithm.
And what does RC5 have to do with it?
Introduction to RC6.
RC6 ( Rivest's Cipher 6 ) is a symmetric block cipher based on the Festel network , developed by Ronald Rivest in 1998.
First, let's figure out the terminology:
What does symmetrical mean?
There are two types of cipher people :
Symmetrical (what we need)
Asymmetric (some other time, bro)
In symmetric encryption, the same key is used to encrypt and decrypt data . It must be kept secret . Those. neither the sender nor the recipient should show it to anyone. Otherwise, your data can be intercepted / changed or even worse.
Symmetric encryption algorithms:
AES (Advanced Encryption Standard)
3DES (Triple Data Encryption Algorithm)
RC4, RC5, RC6 (Rivest cipher)
: . , , .
:
RSA (Rivest-Shamir-Adleman)
DSA (Digital Signature Algorithm), DSS (Digital Signature Standard)
Diffie-Hellman
?
. , : , .
, : .
, ?
. . . .
. , .
:
— .
.
2 ( xor)
.
.
( ) .
() .
- ( ).
, .
. , , , .
:

, , .
RC6 . , , .
:
, , . , RC6
. 4 A, B, C, D
.
.
.
, . :
.
.
(.. 4 ).
.
( ).
.
.
:
.
, .
:
:
(),
( ).
.
, , :
. :
1 .
,
,
.
,
:
# x<<<y -
c = [max(b, 1) / u]
for b - 1 downto 0 do
L[i/u] = (L[i/u]<<<8) + K[i]
2 .
. , :
S[0] = P_w
for i = 1 to 2r + 3 do
S[i] = S[i - 1] + Q_w
3 .
, , :
# : b ,
# L[0,...,c-1]
# r
# : w- S[0,...,2r+3]
A = B = i = j = 0
v = 3 * max(c, 2r + 4)
for s = 1 to v do
{
A = S[i] = (S[i] + A + B)<<<3
B = L[j] = (L[j] + A + B)<<<(A + B)
i = (i + 1)mod(2r + 4)
j = (j + 1)mod(c)
}
, RC6. , , RC5. , RC6:
RC5
RC5 , 1994 . RC6
, .
.
, :
RC5 . .. () , .
RC5 , .
RC5 . , 64- , RC5 .
RC5 . .. , .
RC5 . .
RC5 . .
RC5 .
,
RC5 .
RC5 , RC6. . C RC5:
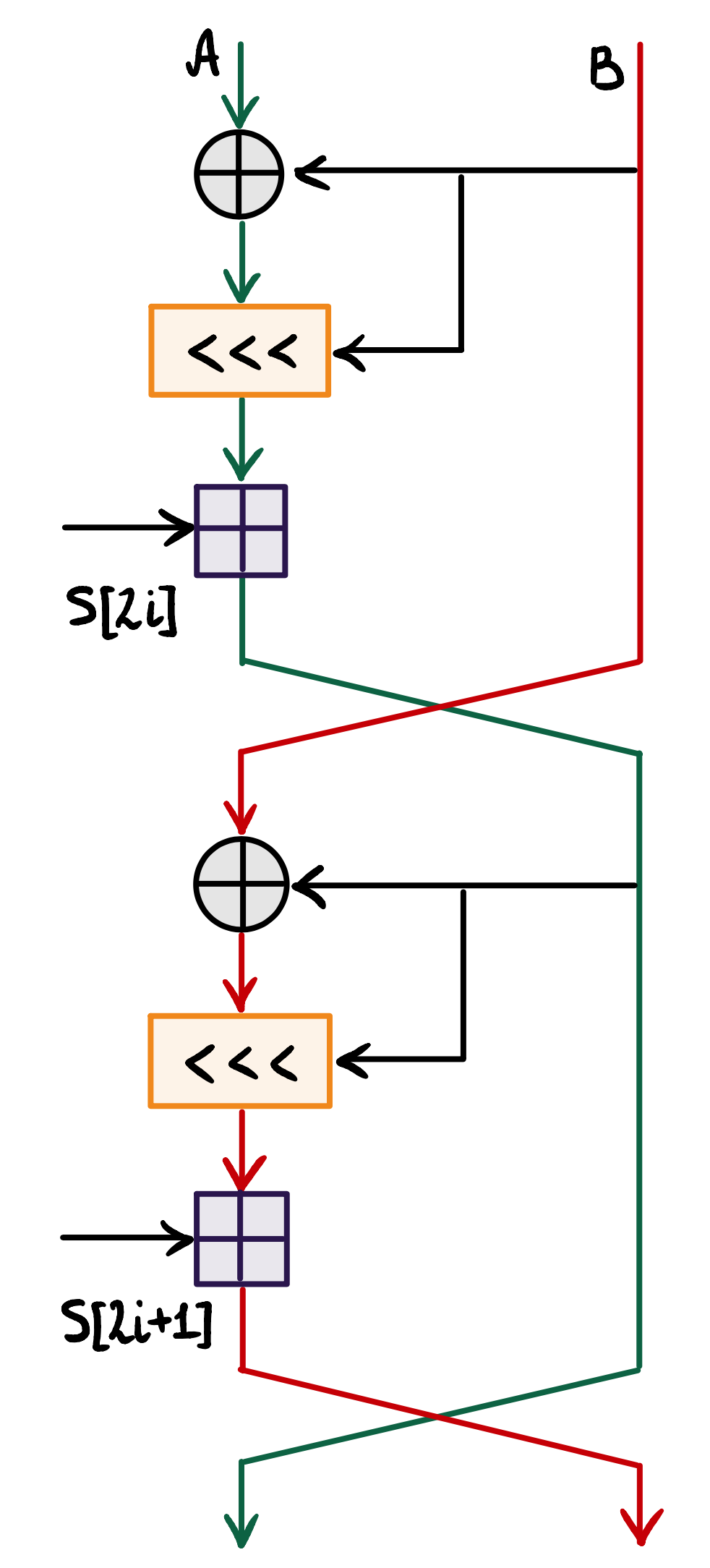
:
A = A + S[0]
B = B + S[1]
for i = 1 to r do
A = ((A xor B)<<<B) + S[2i]
B = ((B xor A)<<<A) + S[2i + 1]
, RC5 .
RC5 RC6
RC5 :
, RC6.
-( ) RC5:
for i = 1 to r do
{
A = ((A xor B)<<<B) + S[2i]
(A, B) = (B, A)
}
RC5. A B, C D:
for i = 1 to r do
{
A = ((A xor B)<<<B) + S[2i]
C = ((C xor D)<<<D) + S[2i + 1]
(A, B) = (B, A)
(C, D) = (D, C)
}
, A B C D, (A, B, C, D) = (B, C, D, A). AB CD:
for i = 1 to r do
{
A = ((A xor B)<<<B) + S[2i]
C = ((C xor D)<<<D) + S[2i + 1]
(A, B, C, D) = (B, A, D, C)
}
AB CD :
for i = 1 to r do
{
A = ((A xor B)<<<D) + S[2i]
C = ((C xor D)<<<B) + S[2i + 1]
(A, B, C, D) = (B, A, D, C)
}
, B D, , . , , .
, :
for i = 1 to r do
{
t = (B * (2B + 1))<<<5
u = (D * (2D + 1))<<<5
A = ((A xor t)<<<u) + S[2i]
C = ((C xor u)<<<t) + S[2i + 1]
(A, B, C, D) = (B, C, D, A)
}
, , ( , pre- post-whitening):
B = B + S[0]
D = D + S[1]
for i = 1 to r do
{
t = (B * (2B + 1))<<<5
u = (D * (2D + 1))<<<5
A = ((A xor t)<<<u) + S[2i]
C = ((C xor u)<<<t) + S[2i + 1]
(A, B, C, D) = (B, C, D, A)
}
A = A + S[2r + 2]
C = C + S[2r + 3]
, , , :
, RC6 A, B, C, D. , . A, D. :
# : 4- w- A, B, C, D
# r
# w- S[0,...,2r+3]
# : , A, B, C, D
B = B + S[0]
D = D + S[1]
for i = 1 to r do
{
t = (B * (2B + 1))<<<lg(w)
u = (D * (2D + 1))<<<lg(w)
A = ((A xor t)<<<u) + S[2i]
C = ((C xor u)<<<t) + S[2i + 1]
(A, B, C, D) = (B, C, D, A)
}
A = A + S[2r + 2]
C = C + S[2r + 3]
# (A, B, C, D) = (B, C, D, A) .
RC6 :
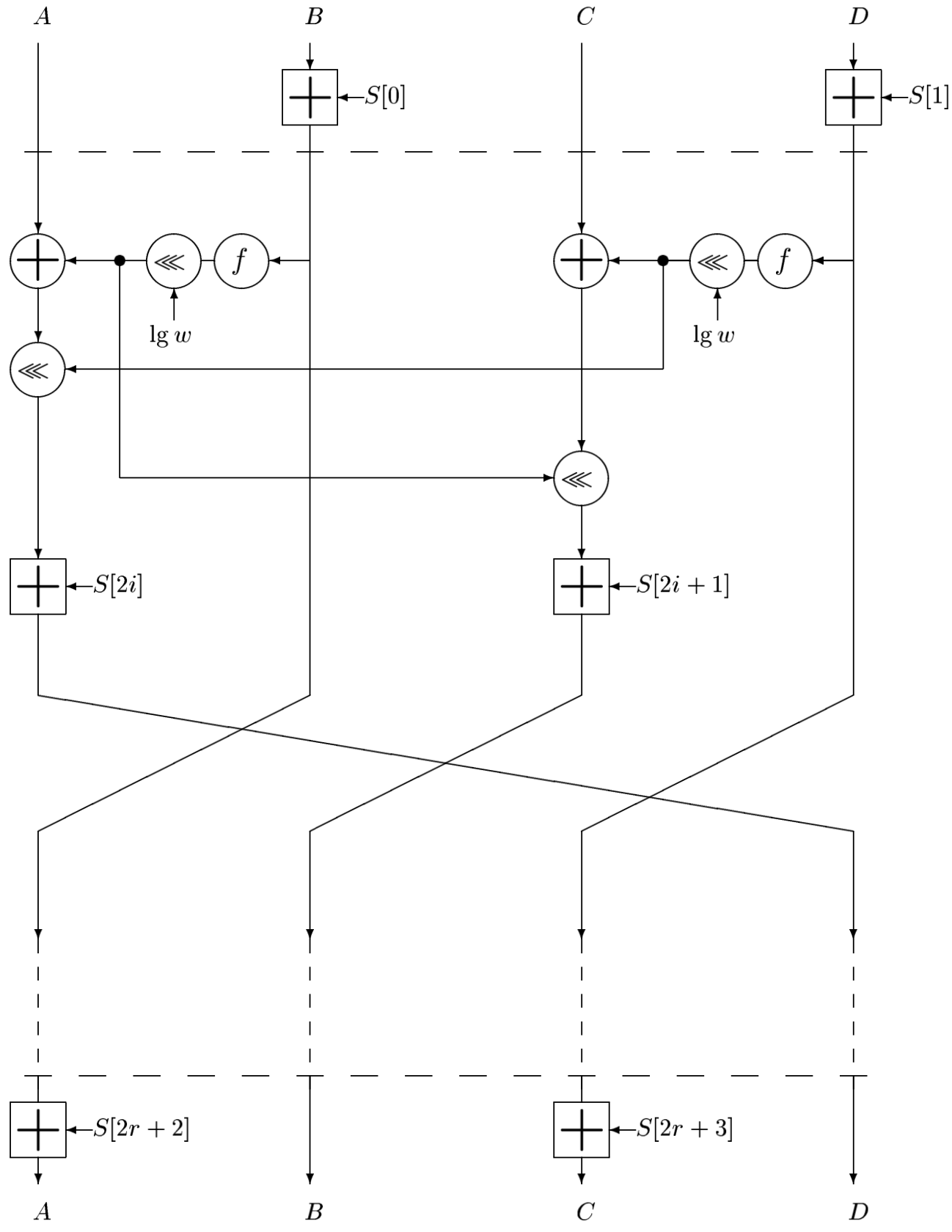
:
# : 4- w- A, B, C, D
# r
# w- S[0,...,2r+3]
# : , A, B, C, D
C = C - S[2r + 3]
A = A - S[2r +2]
for i = r downto 1 do
{
(A, B, C, D) = (D, A, B, C)
u = (D * (2D + 1))<<<lg(w)
t = (B * (2B + 1)) << lg(w)
C = ((C - S[2i + 1)>>>t) xor u
A = ((A - S[2i])>>>u) xor t
}
D = D - S[1]
B = B - S[0]
?
RC6-128/20/b .
, R6
.
. , , ,
. .
, , :
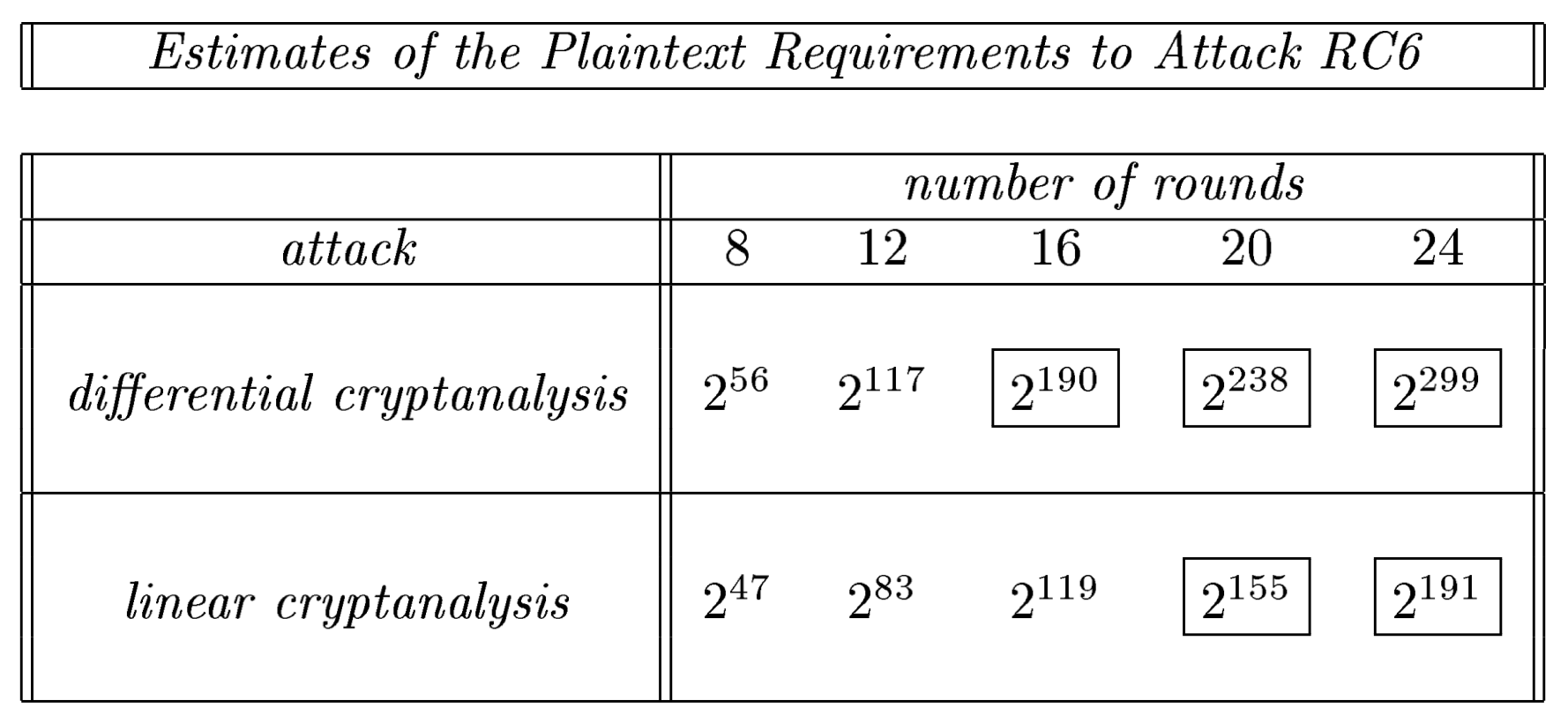
. , .
, , RC6 20 .
RC6 - , . : , . , .
RC6, RC6_en, - .
R.L. Rivest (1994) The RC5 Encryption Algorithm
RL Rivest, MJB Robshaw, R Sidney, and YL Yin. (1998) The RC6 Block Cipher
S. Contini, RL Rivest, MJB Robshaw and YL Yin. (1998) The Security of the RC6