A hash function is a function that converts an arbitrary length of input data into a bit sequence of a fixed length. Hash functions play an important role in modern cryptography. Technology advances, new requirements for security and computational complexity are emerging. The SHA family of algorithms remains the leader among hashing algorithms in many areas, but there is another family of algorithms based on cellular automata that deserves general attention.
Cellular automata
The cellular automaton is a fairly common thing that deserves a separate post . However, in a nutshell, this is a discrete model, which is a grid of arbitrary dimensions, each cell of which at each moment of time can take one of a finite set of states, and the rule for the transition of cells from one state to another is determined.
In the case of elementary cellular automata, the grids of cells have a one-dimensional dimension.

In a cellular automaton, for each cell, there is a set of other cells, called a neighborhood, that determine the next state of the cell. The initial state is the state in which the cell values and their neighborhoods are determined at time t. Now a new generation of cells is created when "t" is incremented by 1.
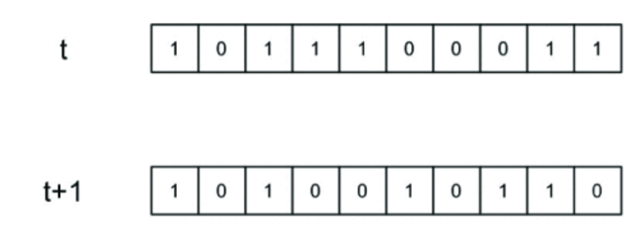
30, :
:

, .
( ).
.
.
?
, : 128, 192 256 .
:
.
.
.
512 .
512 , 8 64 .
512 30.
5 512 ().
XOR 5 512 .
, 1.
6, 7 8 , 512 , .
, .
, .
64 .
,
,
,
,
1.
,
4.
ROTL — , ROTR — .
. :
'1' (512 )
'0' (512 )
.
30 , - . . , .
:
-
Building Secure and Fast Cryptographic Hash Functions Using Programmable Cellular Automata
LCASE: Lightweight Cellular Automata-based Symmetric-key Encryption
Cellular Automata Based Hashing Algorithm (CABHA) for Strong Cryptographic Hash Function
A New Cryptographic Hash Function Based on Cellular Automata Rules 30, 134 and Omega-Flip Network