With the rise of cybersecurity threats, it becomes more and more imperative for developers to update their web application security standards while ensuring that user accounts are safe. To this end, many online applications are now asking users to add an extra layer of security to their account. They do this by enabling two-factor authentication. There are various methods to implement two-factor authentication, and TOTP (Time Based One Time Password) authentication is one of them.
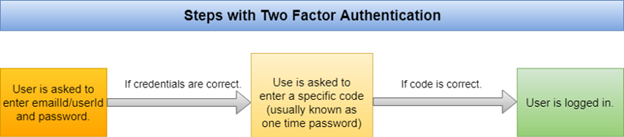
To understand what TOTP is and how it is used, it is necessary to first briefly review the more basic concepts. The first of these is two-factor authentication. Two-factor authentication (or multi-factor authentication) is a method of identifying a user in a service (usually on the Internet) by requesting authentication data of two different types, which provides two-layer, and therefore more effective, account protection against unauthorized entry. This means that after enabling two-factor authentication, the user must go through one more step to successfully log in. The standard steps for logging into an account are entering a username and entering a password (Figure 1).

Enabling two-factor authentication adds an additional step to the login order (Figure 2). This method is more secure as the attacker cannot gain access to the user account if he does not have access to both the user's regular password and the one-time password.
There are currently two widely used methods for obtaining a one-time password:
Based on SMS . Each time the user logs in, he receives a text message to the mobile phone number specified in the account, which contains a one-time password.
TOTP. QR- , .
SMS . , . , SMS , . . NIST 2016 . SMS, TOTP - .
, , , , . :
, ,
( ), ,
, , ,
, , , . , SMS , , . . SMS , TOTP , , .
, TOTP, ( ) . , . . , , , , .
TOTP – , .
:
,
,
,
, . , . TOTP – HOTP.
HOTP « HMAC». (IETF) RFC4226. HOTP .
:
HMAC ( SHA-1)
hmacHash = HMAC-SHA-1 ( , )
20 . . , . HOTP
hmacHash[19] means 19th byte of the string.offset = hmacHash[19] & 0xf;
truncatedHash = (hmacHash[offset++] & 0x7f) << 24 | (hmacHash[offset++] & 0xff) << 16 | (hmacHash[offset++] & 0xff) << 8 | (hmacHashh[offset++] & 0xff);
finalOTP = (truncatedHash % (10 ^ numberOfDigitsRequiredInOTP));
, 4 hmacHash [19]
. hmacHash [offset]
hmacHash [offset + 3]
31 truncatedHash
. , , .
HOTP. RFA4226 , .
, . ? TOTP. TOTP « ». IETF RFC6238. TOTP HOTP . , «» «», . , HOTP OTP. , , . , , Unix, . Unix , . , , . . , Google Authenticator 30 .
counter = currentUnixTime / 30
, . : . QR-. , , . , , QR-, . , – QR- . (, Google Authenticator App, Authy ..), . . TOTP -.
When user request to enable 2-factor authentication
// Generate a secret key of length 20.secretKey = generateSecretKey (20);
// Save that secret key in database for this particular user. SaveUserSecretKey (userId, secretKey);
// convert that secret key into qr image.qrCode = convertToQrCode (secretKey);
// send the qr image as responseresponse (qrCode);
QR-. QR-, . , Unix HOTP, . QR-. , , .
User types the code displayed in the application.
// Fetch secret key from database.secretKey = getSecretKeyOfUser (userId);
if (codeTypedByUser == getHOTP (secretKey, currentUnixTime / 30)) {enableTwoFactorAuthentication (userId);}
HOTP , OTP Unix. OTP , . , , , . , , . , .
User types the code displayed in the phone application to login
// Fetch secret key from database.secretKey = getSecretKeyOfUser (userId);
if (codeTypedByUser == getHOTP (secretKey, currentUnixTime)) {signIn (userId);}
, . , , QR- . , Google Authenticator App, . , , . SMS, , .
Two-factor authentication is gaining popularity. Many web applications implement it for added security. Unlike the SMS-based method, the TOTP method also requires little effort. So this feature is worth implementing for any application.