With the advent of computer technology, it has become more productive to store information in databases rather than on paper. Web applications that require user authentication typically check login passwords against real passwords, which are usually stored in private company databases. If intruders gain access to the aforementioned database, personal data of users will be lost. Currently, databases use hash algorithms to protect stored passwords, but security concerns are still relevant. Every year hackers publish a large list of hacked passwords from well-known social networks or data stores. These attacks were successful due to the use of a weak hashing algorithm.
Cryptographic hash functions, often referred to simply as hashes, are an indispensable and ubiquitous tool used to perform a variety of tasks, including authentication, data integrity checking, file protection, and even malware detection. It is a mathematical algorithm that converts an arbitrary array of data into a fixed-length string of letters and numbers. Moreover, provided that the same type of hash is used, this length will remain unchanged, regardless of the amount of input data [2]. There are many hashing algorithms that differ in cryptographic strength, complexity, bit depth, and other properties. It is believed that the idea of hashing belongs to an IBM employee, appeared about 50 years ago and has not changed fundamentally since then.Nowadays, hashing has acquired a lot of new properties and is used in many areas of information technology.
The MD5 message hashing algorithm is the 5th version of the message hashing algorithm developed by Ron Rivest in 1991 to produce a 128-bit output message. This version [5] was presented as improved in terms of reliability relative to the previous MD4 algorithm.
Converting a message of arbitrary length to a hash value involves five steps of the algorithm, each of which has its own specific task. Let's take a closer look at the steps of the algorithm:
Step 1: Align the flow
It is necessary to add extra bits to the original message in such a way that the length of the original message with the extra bits is equal to 448 modulo 512. The addition is performed even if the length of the original message is already comparable to 448. In the padding bits, only the first bit is 1 and the rest of the bits are 0.
2.
64- ( ) . , 512 . 512 .
3: MD-
(A, B, C, D) . A, B, C, D 32 - ,
Word A |
01 |
23 |
45 |
67 |
Word B |
89 |
AB |
CD |
EF |
Word C |
FE |
DC |
BA |
98 |
Word D |
76 |
54 |
32 |
10 |
4:
MD5 , 32- 32- [1].

OR, XOR, AND, NOT. ( ) , . , .
5.
A, B, C, D MD5, .
MD5 . - , . MD5 , - .
MD5 , «» MD5:
1)
— - , . , , . , . .
— , , , ( ) [7].
. , , . , , – . ( ), . - .
PasswordsPro, MD5BFCPF, John the Ripper.
2)
- , , , . - , -, [4].
- H n P. - : , h p P, H(p)=h, , . — H(p) p P, , -.
— . — R, P. , R -. - [11]:
1) - ;
2) .

, , .
H R, .
h, ( ), R(…R(H(R(h)))…). - - - , . h, .
-. , : H, R1, H, R2, …, H, Rk.
. , k .
-, . — . , 100% . , , , -, .
MD5
- ( ) . -, «» .
MD5 2004 . 2004 MD5- .
[10] , 512- , -. MD5 1 . , ( ):
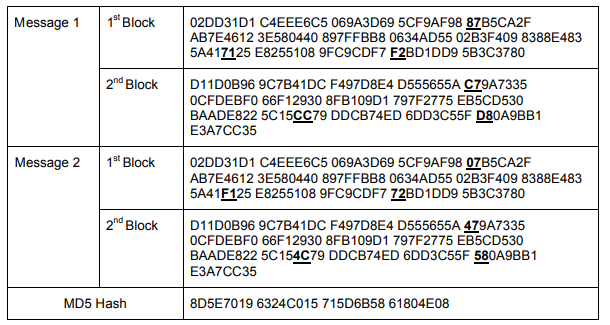
, , . , MD5 .
,
. , , , .
N L — . H . [9]
, , , . , , 2 , « » . , . , . : , .
“”
, . , , , , . - , , ( ), [8]. , , , . , 48 . :
1) : , , . .
2) () : , . , . . , , , , .
3) . , , username, . , . , , , “root” “admin”.
, − , . , - : -, , - -, , . , , MD5 . IETF (Internet Engineering Task Force) MD5 , .
MD5 , .
:
1. MD5 // wikipedia.org. ( : 20.11.2020).
2. A.. , .. , .. , .. . . 2- , . -2006.
3. - // wikipedia.org. ( : 5.12.2020).
4. // wikipedia.org ( : 2.12.2020).
5. Rivest, R. (1992, April). The MD5 Message Digest Algorithm. Request for Comments (RFC) 1321. Retrieved from https://www.rfceditor.org/rfc/rfc1321.txt
6. Kioon M. C, Wang Z. S, Shubra D.D Security Analysis of MD5 Algorithm in Password Storage // Scientific.Net. 2013. . 2706-2711.
7. Nechaev V.I. Elements of cryptography (Fundamentals of information security theory): Textbook. A manual for high fur boots and ped. universities. / Ed. V.A. Sadovnichy - M .: Higher. shk., 1999.
8. John Black, Martin Cochran, Trevor Highland Fast Software Encryption. FSE ed. 2006.S. 262-277.
9. Information entropy // ru.wikipedia.org/ (date of access: 12.11.2020).
10. How to Break MD5 and Other Hash Functions // (date accessed: 10/17/2020).
11. Data structures / Hash chains // medium.com (date accessed: 10.12.2020).