Introduction
A cryptographic hash function is a set of steps that transform an arbitrary block of data into a fixed-length sequence. Any change in the input data leads to a change in the value of the function. Hash functions are used to calculate checksums, when generating an electronic signature, when storing passwords in security systems in the form of a hash code, etc.
The CubeHash family of hash functions was proposed as the new SHA-3 standard in the 2009 National Institute of Standards and Technology (NIST) hash competition .
This article describes the principle of operation of this family, and also discusses the resistance of the algorithm to various attacks.
Algorithm Description
The following is an algorithm of work ![]() according to the specification [1].
according to the specification [1].
The operation of the algorithm is determined by 3 parameters:
 - the size of the output sequence in bits,
- the size of the output sequence in bits, 
 - the number of rounds,
- the number of rounds, 
 - the size of the blocks of the input message in bytes,
- the size of the blocks of the input message in bytes, 
The idea of the algorithm is to sequentially transform the ![]() state based on the input sequence. The algorithm consists of 5 steps:
state based on the input sequence. The algorithm consists of 5 steps:
initialization of internal state
breaking a message into blocks
iterative state transformation
.
32 - ![]() ( little-endian).
( little-endian).
3 ![]()
![]() . .
. . ![]()
![]() .
.
. ![]() . . .
. . .
. ![]()
![]() .
. ![]()
![]() .
.
![]() 1,
1, ![]()
![]() .
.
![]() .
.
F
![]() , , , .
, , , . ![]() 10 :
10 :



 ,
, 

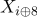 ,
, 
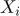
 ,
, 

 ,
, 
1
 ,
, 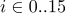

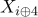 ,
, 
4

 ,
, 
![]() [2]:
[2]:

-
:
: - .
: 2 .
-, , - , , , .
CubeHash
, . .. , , .
50% ![]() . . , 128 [3].
. . , 128 [3].
. . , . ![]() . , 64 [3].
. , 64 [3].
![]() .
.
[4] , ![]() ,
, ![]() .
.
![]()
![]() .
. ![]() ( ),
( ), ![]() .
. ![]()
![]()
![]()
![]() ,
, ![]()
![]()
![]() , .
, .
, , , ![]() . ,
. , ![]() ,
, ![]() , [2]. , , ,
, [2]. , , , ![]() .
.
F
![]() 128- [2]. 15
128- [2]. 15 ![]() :
:
|
AABBCCDD |
EEFFGGHH |
IIJJKKLL |
MMNNOOPP |
|
ABABCDCD |
EFEFGHGH |
IJIJKLKL |
MNMNOPOP |
|
ABBACDDC |
EFFEGHHG |
IJJIKLLK |
MNNMOPPO |
|
ABCDABCD |
EFGHEFGH |
IJKLIJKL |
MNOPMNOP |
|
ABCDBADC |
EFGHFEHG |
IJKLJILK |
MNOPNMPO |
|
ABCDCDAB |
EFGHGHEF |
IJKLKLIJ |
MNOPOPMN |
|
ABCDDCBA |
EFGHHGFE |
IJKLLKJI |
MNOPPONM |
|
ABCDEFGH |
ABCDEFGH |
IJKLMNOP |
IJKLMNOP |
|
ABCDEFGH |
BADCFEHG |
IJKLMNOP |
JILKNMPO |
|
ABCDEFGH |
CDABGHEF |
IJKLMNOP |
KLIJOPMN |
|
ABCDEFGH |
DCBAHGFE |
IJKLMNOP |
LKJIPONM |
|
ABCDEFGH |
EFGHABCD |
IJKLMNOP |
MNOPIJKL |
|
ABCDEFGH |
FEHGBADC |
IJKLMNOP |
NMPOJILK |
|
ABCDEFGH |
GHEFCDAB |
IJKLMNOP |
OPMNKLIJ |
|
ABCDEFGH |
HGFEDCBA |
IJKLMNOP |
PONMLKJI |
32- . . , ![]() , , . , .
, , . , .
.
( )
,
.
,
, . .
.
(cycle per byte cpb). , 1 .
SHA-256, SHA-512 CubeHash16/32 Intel Core 2Duo 6f6 (a) Intel Core 2 Duo E8400 1067a (b) [5]:
11.47 cpb: CubeHash 16/32, (b), amd64 architecture.
12.60 cpb: SHA-512, (b), amd64 architecture.
12.60 cpb: SHA-512, (a), amd64 architecture.
12.66 cpb: CubeHash 16/32, (a), amd64 architecture.
12.74 cpb: CubeHash 16/32, (b), x86 architecture.
14.07 cpb: CubeHash 16/32, (a), x86 architecture.
15.43 cpb: SHA-256, (b) x86 architecture.
15.53 cpb: SHA-256, (b), amd64 architecture.
15.56 cpb: SHA-256, (a), amd64 architecture
17.76 cpb: SHA-512, (b), x86 architecture.
20.00 cpb: SHA-512, (a), x86 architecture
22.76 cpb: SHA-256, (a), x86 architecture
CubeHash SHA-3 -, NIST. Cubehash , . , CubeHash , .
![]()
![]() . , CubeHash 8 / 1-512 CubeHash 1 / 1-512, CubeHash 1 / 1-512 , CubeHash 1 / 2-512. - CubeHash 1/128- h.
. , CubeHash 8 / 1-512 CubeHash 1 / 1-512, CubeHash 1 / 1-512 , CubeHash 1 / 2-512. - CubeHash 1/128- h.
: ![]()
![]() .
.
DJ Bernstein. Cubehash specification (2.b.1)
Vikash Jha. Cryptanalysis of Cubehash.
Philip Doughty Jr. A Generic attack on CubeHash, a SHA-3 candidate.
Benjamin Bloom and Alan Kaminsky. Single Block Attacks and Statis-tical Tests on CubeHash.
DJ Bernstein. CubeHash parameter tweak: 16 times faster.