We find out how and where you can get an electronic signature using the example of the RSA cryptosystem.
Content
Introduction
Definitions and notation
Description of the RSA cryptosystem
Asymmetric Cryptographic Systems
Generating keys
Encryption and decryption
Receiving message signature over RSA
Electronic signature of documents
Conclusion
Introduction
Surely you have come across such a concept as "electronic signature". If you turn to federal law , you can find the following definition:
« - , ( ) , »
, , , , - , . , , .
, , . , (DSA, 34.10-2012, RSA-PSS ..), .
, , RSA, , 1978 . . , .

, :
– ,
– ,
– , ()
– , .
– .
– .
a b , 1.
φ(n) – , , n .
, , RSA, ,
. :
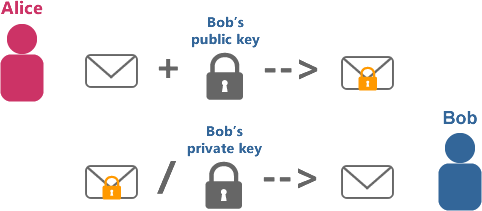
. ( ). , , . , , , . , , . , RSA.
. , , , , "" . : ? ? ? .
. y=f(x), x, x . , y=f(x, k), x, k x y , k – .
:
φ(n) – n. , , . , , . c, m, n, e, d.
. c m. . , m , c – . c e, m, n, . (e, n) . .
. d , m c. , .
, , – . n , :
p q – . n :
n . , d , e. p q, , . n. , n ( ), , n ( , RSA, n 2048 ).
. e:
d:
. (e, n), d, .
, ...
m (m ∈ [1, n − 1]). , e n. :
, . , c ∈ [1, n − 1], m. , d:
, m ≡ m′ . , () , , .
:
:
, m ≡ m′ :

:
, m . (e, n) d, , . d , . "" m d:
. , , , . , m, s (e, n). , s e:
, m ≡ m′, .
" "!

, "". – . , , - ( , -, ). , - ( ) , .
, . :
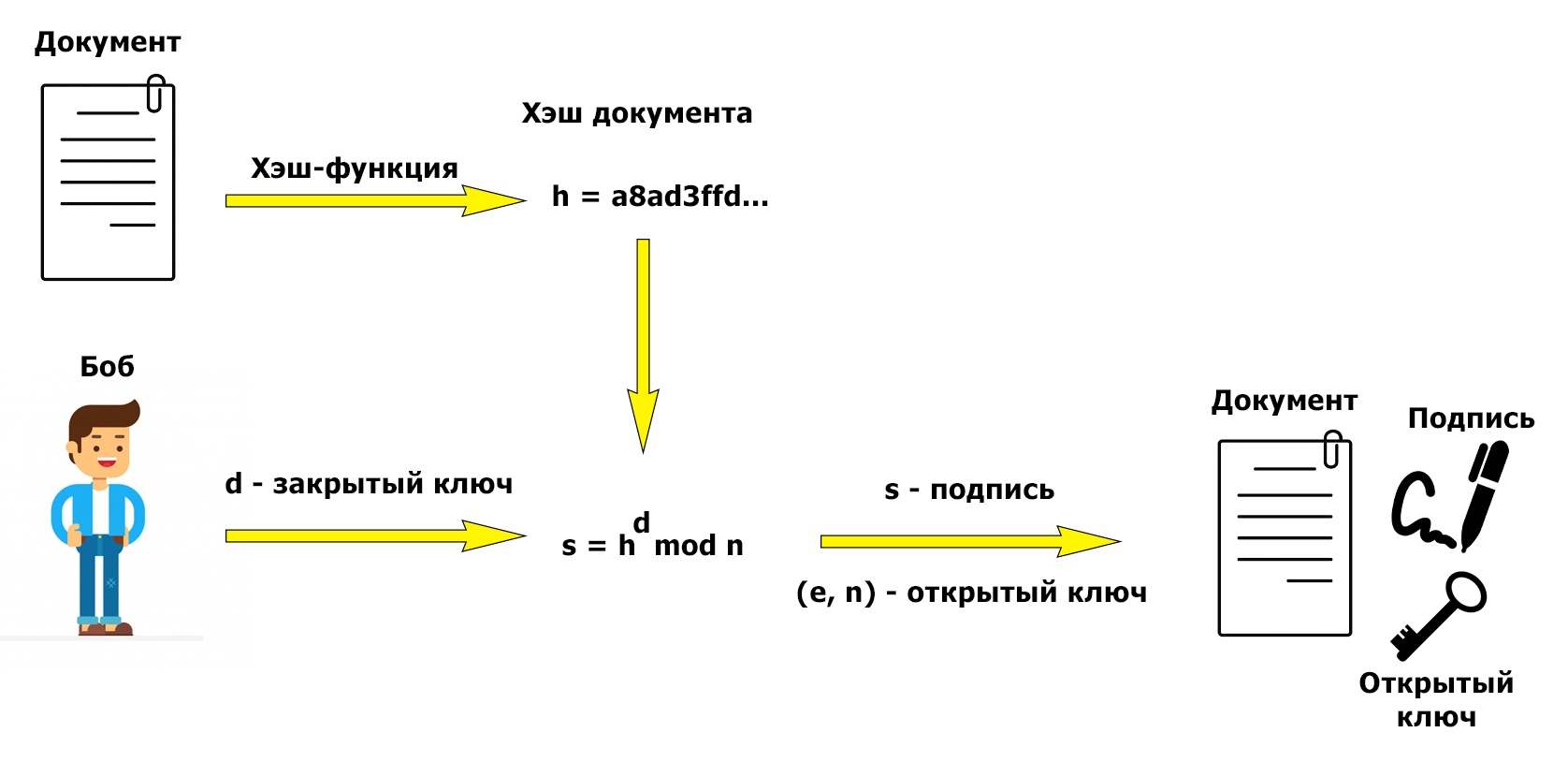
:

, , , . , , . , , .
, , , . " " -, .
!
Handbook of Applied Cryptography by A. Menezes, P. van Oorschot and S. Vanstone
: . / . . , . . , . . , . . ; . . . . – .: , 2016
. . - — .: , 2006.
NIST Special Publication 800-57 Part 3 Revision 1
.. . – .: -, 2010. -