When preparing material for my next post, I needed to collect a database of images. The solution was to collect screenshots from popular image storage services. I described the principle here . While I was wandering like a hyena through these garbage dumps, I found many screenshots of the same type, which ...
... contain confidential information, namely: logins and passwords from various services. All this is disguised as correspondence, in which one side transmits to the other any private information.
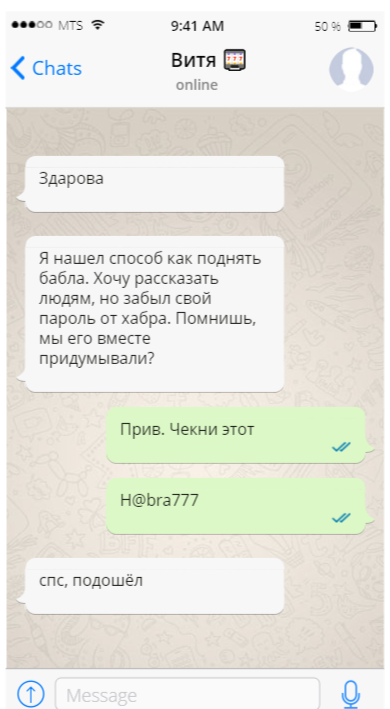
Divorce scheme
The divorce itself is
Example

Does it look realistic?

Let's try to log in using the data from the correspondence.

Yes, we are rich! It's time to multiply the simple state by zero! Withdraw.

To confirm the transfer, you need to make a transfer of your funds. No comment.
Oh well, there are no such mammoth suckers anymore
Let's check the movement of funds on this wallet .

The first transaction was committed on 2020-04-20 06:16. There are days when there are several transactions. For 7 months, the author earned about $ 9 thousand at the current rate. The result is not bad, considering that the costs go only to hosting static content .
How many more such resources are difficult to calculate. In just a couple of hours, a bunch of such screenshots appeared in my folder.

There are different options, with correspondence in Whatsapp, in the mail, etc.
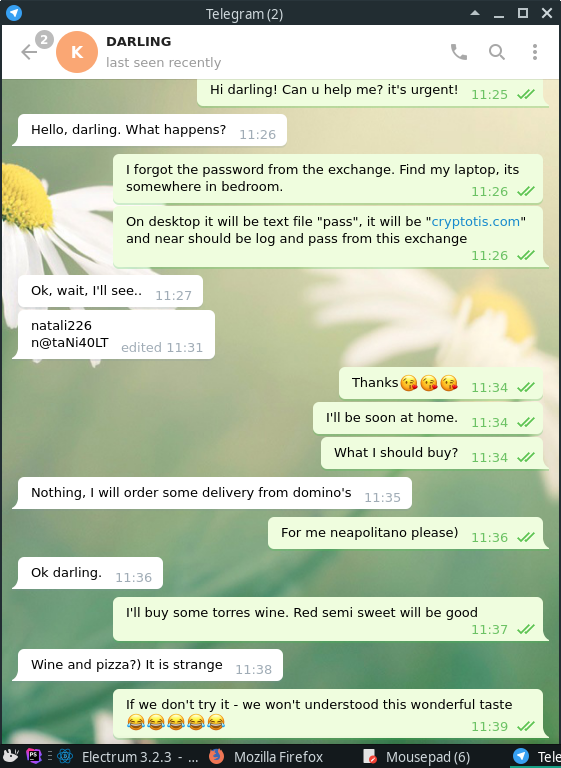
conclusions
The method is interesting and aimed at those who consider themselves smarter than others. I have not seen this before. Remember that if you received some kind of private information by accident, then this "accident" could not be accidental at all.