Intro
We are all subject to some degree of the Trojan Threat today. Any device that was bought in the nearest store under the house can serve not only you as a consumer, but also an attacker for his purposes. Therefore, the threat is called Trojan: in ancient Greek mythology, there is a case of the capture of an entire fortress with the help of a gift that only at first glance seems like that. What can we say about the capture of data of modern users: passwords, requisites, private messages.
There are two main types of Trojan: software and hardware. Software trojan is a type of malware masquerading as legitimate software. As a rule, this is an emulation of free software or an attachment in an e-mail, and the installation of this program makes it possible to perform its hidden true tasks: full control over a PC, personal data, transactions, etc. The hardware trojan pursues approximately the same goals, which is a malicious change in the electrical circuits in devices (most often with the aim of stealing data and passwords). Let's say you buy a keyboard from an unverified store, and this device inside contains a built-in antenna (any radio transmitter) that is capable of transmitting the entered characters to an attacker via radio communication. In general, this problem often arises,when a company designs an integrated circuit (hereinafter referred to as an IC), but for the production of such circuits it has to turn to another unreliable company. Sounds not safe at all, right?
Today, there are many ways to protect against software Trojan threats and, most importantly, they are constantly updated, as both malware and hardware do not sleep, improving over time. The simplest recommendations for the user are to regularly update the software, use an "antivirus" and do not go to unverified links in the mail and on the Internet. However, what to do with hardware threats? It turns out that machine learning threat analysis is gaining popularity lately. This is what I wanted to talk about today.
Basic research
, , . . , () , .
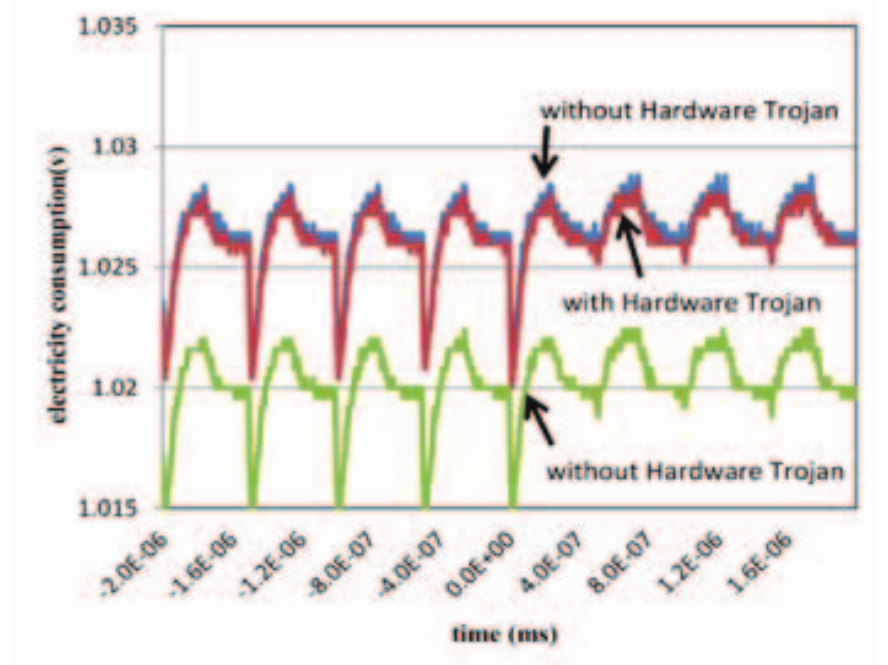
, ( - , - +-1( )) (SVM), . , FPGA - .
, , "Journal of Hardware and Systems Security" 2018 . , , . : () ( , ). .
, : - , - , . , , . - .
:
( ); \ , , ..; NAND NOR ;
; , \ .
:
;
;
.
, . . . , (dwelling time) ( , ., ; machine learning ).
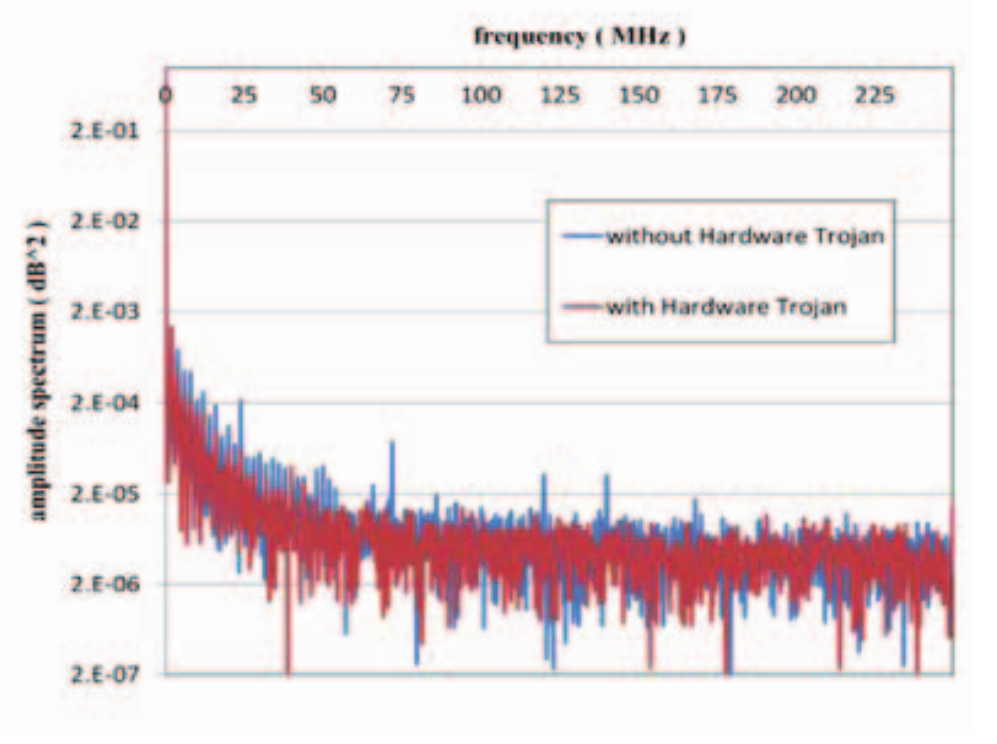
: "" . .

. , , .
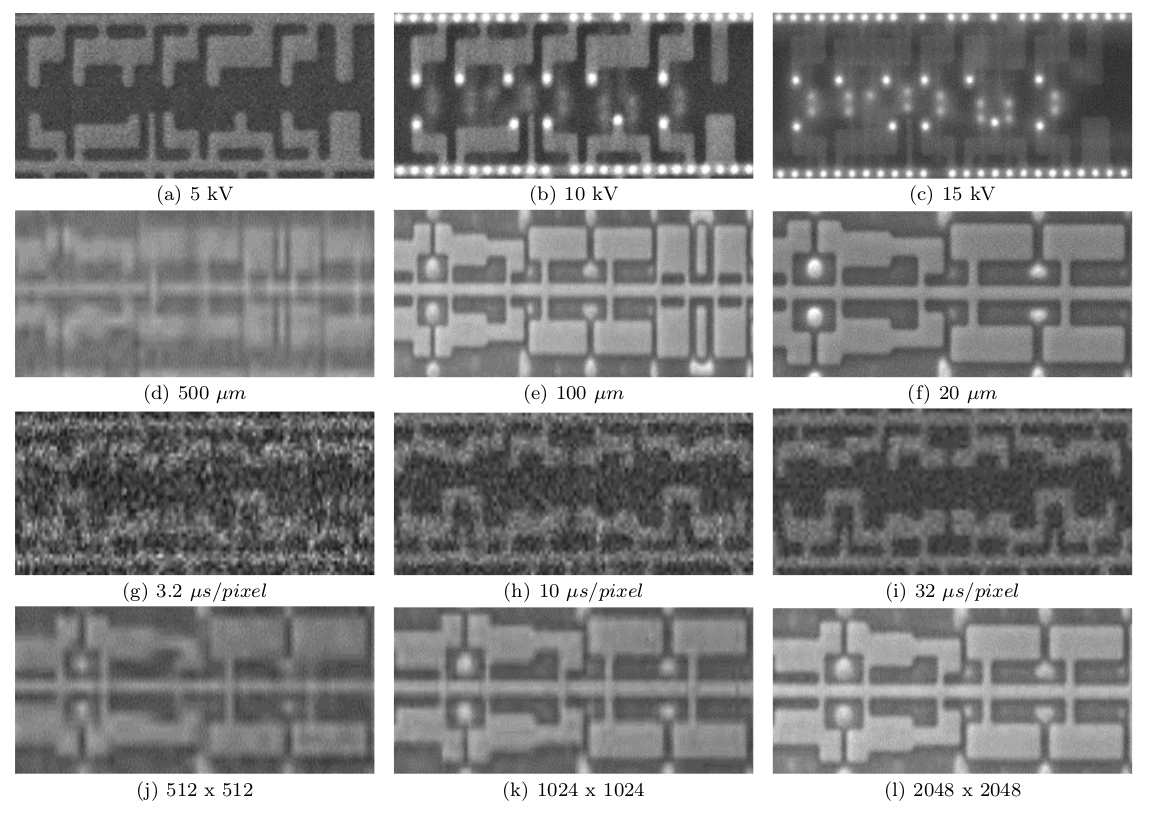
, - . , . - SVM RBF ( ). , , , .
RBF
RBF(radial basis function) - . , SVM . . :
rbf_kernel_svm_clf = Pipeline([
("scaler", StandardScaler()),
("svm_clf", SVC(kernel="rbf", gamma=5, C=0.001))
])
rbf_kernel_svm_clf.fit(X, y)
, , - . -. ,
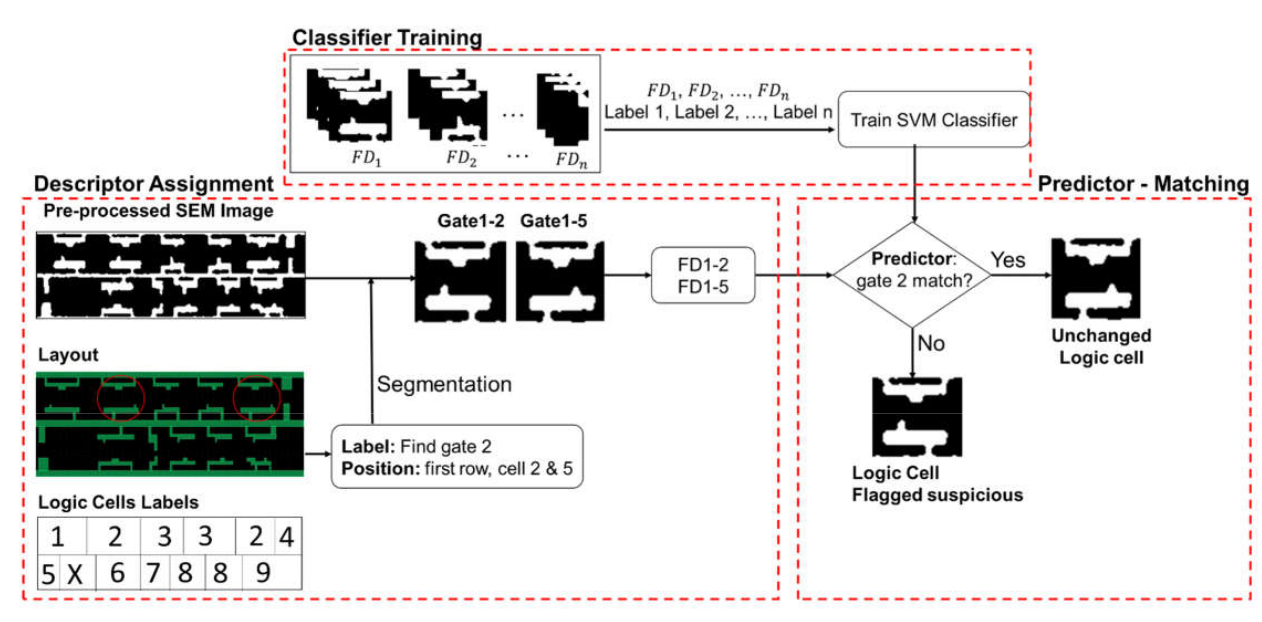
, , , . .
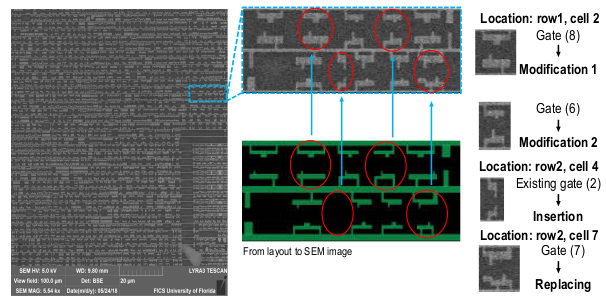
- , . , , . ( ) . , , . . !
Takato Iwase, Yusuke Nozaki, Masaya Yoshikawa, "Detection Technique for Hardware Trojans Using Machine Learning in Frequency Domain", 2015 IEEE 4th Global Conference on Consumer Electronics (GCCE)
N. Vashistha, M. Tanjidur Rahman, H. Shen, D. L. Woodard, N. Asadizanjani, and M. Tehranipoor, “Detecting Hardware Trojans Inserted by Untrusted Foundry using Physical Inspection and Advanced Image Processing,” Springer journal of Hardware and Systems Security, special issue on Hardware Reverse engineering and Obfuscation 2018.
Nidish Vashistha, Hangwei Lu, Qihang Shi, M Tanjidur Rahman, Haoting Shen, Damon L Woodard, Navid Asadizanjani and Mark Tehranipoor, "Trojan Scanner: Detecting Hardware Trojans with Rapid SEM Imaging combined with Image Processing and Machine Learning".
M. Tehranipoor and F. Koushanfar, “A Survey of Hardware Trojan Taxonomy and Detection,” IEEE Des. Test Comput., vol. 27, no. 1, pp. 10–25, Jan. 2010.
Joseph Clements and Yingjie Lao, "Hardware Trojan Attacks on Neural Networks", Department of Electrical and Computer Engineering Clemson University, Clemson, SC 29634.
Yuntao Liu, Yang Xie, and Ankur Srivastava, "Neural Trojans", 2017 IEEE 35th International Conference on Computer Design.
X. Zhang and M. Tehranipoor, “Case study: Detecting hardware Trojans in third-party digital IP cores,” in 2011 IEEE International Symposium on Hardware- Oriented Security and Trust, 2011, pp. 67–70.
K. Xiao, D. Forte, Y. Jin, R. Karri, S. Bhunia, and M. Tehranipoor, “Hardware Trojans: Lessons Learned after One Decade of Research,” ACM Trans. Des. Autom. Electron. Syst., Vol. 22, no. 1, pp. 1-23, May 2016.
F. Wolff, C. Papachristou, S. Bhunia, and RS Chakraborty, “Towards Trojan-free trusted ICs: Problem analysis and detection scheme,” in Proceedings of the conference on Design, automation and test in Europe, 2008, pp. 1362-1365.