
Computers have always been a battleground. The eternal battle of hacking and protection began with the appearance of the first mass PC and will continue as long as humanity exists. The first hackers were researchers looking for ways to optimize computing, find more efficient modes of operation, and make the most of the meager capabilities of computers. Then there was no term "hacker", people who were engaged in "hacking" would now be called system programmers and programmers of microcontrollers, still beating for every extra byte and writing at a low level.
It is difficult to say when entertainment became malicious and then self-serving. Initially, damage to data or hardware did not lead to profit, because writing viruses was the lot of loners, amateurs in a good sense of the word, people not looking for profit.
The network changed everything ...
Prerequisites for EDR
For a very long time, computer viruses were extremely specific programs. They had to survive in the very cramped conditions of weak computers with limited resources, the authors of the viruses were gurus of the Assembler, they thoroughly knew all the subtleties of computers at a low level. But computers became more powerful, they were connected by a network, and it all smelled of big money. Hacking was put on stream, now it is a serious and large business, vulnerabilities are sold for a lot of money, the main traffic of computer networks is DDoS. Defense against attacks has become a big business as well. Gone are the days when antivirus software was bought on floppy disks and protected only one computer. Even the very concepts of "virus" and "antivirus" are already becoming obsolete, entire organizations are becoming targets of attacks, and this is no longer a single enthusiast.
But the attack programs remained specific for quite a long time; they could be recognized by their characteristic signatures, behavior patterns, and attack vectors. Antiviruses working according to ancient "dosovskiy" principles were quite effective; heuristic analysis allows you to quickly find encrypted and polymorphic viruses. Security specialists have developed new protection methods based on a comprehensive analysis of various signs of malicious activity, such as: atypical network traffic, suspicious activity of user accounts, the presence of suspicious programs on computers, etc. SIEM (Security Information and Event Management) systems identify infected computers by analyzing corporate network logs. And local systems EPP (Endpoint Protection Platform) keep order at the employee's workplace according to the principle of classic antivirus and firewall.
It would seem that everything is under control, but the problem came from the other side.

Kevin in his early years, photo from the police station
Since the time of the famous Kevin Mitnick- classical social engineering is not only successfully used until now, but also develops in step with the times. You no longer need to call all the numbers belonging to the company yourself to find a careless employee who will agree to open the door or enter the command the burglar needs. The simplest script will send tens of thousands of fake emails, the bot will knock on instant messengers and social networks, and phishing sites will collect a rich harvest of passwords. Such an attack has no special signatures and cannot be traced back to the firewall logs. A highly specialized program written for specific security measures of a pre-selected company will also be passed by the antivirus without raising an alarm.
More recently, in 2013, Symantec investigated the activities of a hacker group called Thrip... Their actions were very successful precisely because they practically did not use the traditional "hacker software", which leaves familiar traces and is well known to modern security systems. These hackers use social engineering to infiltrate an organization. To obtain administrator privileges, the usual utility is modified once, without flashing the same signature in different hacks. Moreover, such programs or scripts are used very briefly and then delete themselves without leaving any traces, or worse, they exist only in RAM, never writing their code to files, storing data in the registry, and calling standard powershell to work. exe or wmic.exe, which do not raise the alarm for conventional antiviruses. After entering the system, the most common utility utilities are used,which are allowed by security policies. For example, Thrip used a modified penetration test program to penetrate Mimikatz , “designed to learn C and experiment with Windows security,” and then, to remotely control compromised computers, they used Microsoft's PsExec utility from the PsTools package and another completely legal program, LogMeIn . To steal data, they used not cunning spyware, but the most common WinSCP FTP client .
Such activity is almost invisible for tools like SIEM and EPP.
How EDR works
In the same 2013, Anton Chuvakin (a Russian computer security specialist who graduated from the Physics Faculty of Moscow State University, working abroad) proposed to single out a new category of tools for preventing hacker attacks and called them ETDR (Endpoint Threat Detection & Response), later the abbreviation EDR became generally accepted. ... Endpoint refers to a server, desktop workstation, laptop, and smartphone.

Anton Chuvakin
How does EDR differ from other, more traditional methods of protection?
The main difference between EDR and SIEM is work with local data and logging of events occurring on a specific computer. SIEM monitors global network traffic in an organization, making this system collect data from each individual computer is very expensive and requires too much power.
In fact, this is a logical development of the usual antiviruses and EPP systems that monitor suspicious traffic activity and search for known malicious programs. But if antiviruses catch malicious software at the moment it is launched, EDR tools go deeper.
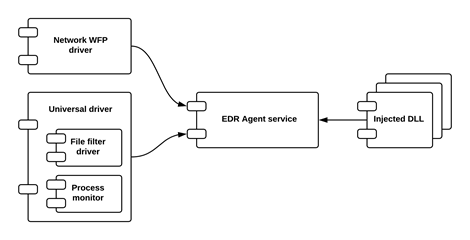
Any EDR system consists of several typical modules, the interaction of which can be seen on the example of EDR from Comodo Cybersecurity, which posted the source code for Open EDR to share:
- Core Library - a basic framework that contains the main functions and is the core of the system;
- EDR Agent service - the EDR application itself;
- Process Monitor - DLL-library that is injected into various processes to intercept API calls and tools for working with it;
- File filter driver - a mini-file system filter that intercepts file system I / O requests, monitors access to the registry, protects EDR components and settings, etc.
- Network monitor - component for monitoring network activity;
Flexible settings allow filtering out false alarms and adjusting the system for a specific network in the organization, and the core of the system is buried at a very deep level using “hacker technologies” such as Rootkit.
In addition to signature and heuristic analysis, EDR continuously scans the system for IoC (Indicator of Compromise) and IoA (Indicators of Attack) , tracking down certain signs that may indicate an intrusion attempt: phishing emails, access to suspicious IP -addresses, tracking hashes of malicious files, registry values, etc.
It seems that all this is not very different from the usual antivirus and firewall? Not really.
Artificial intelligence is on guard
The non-profit organization MITER Corp has accumulated a large array of data from the scan logs of corporate networks and endpoints collected during the penetration of intruders into systems, as well as penetration testing and its own research, systematizing them and identifying the main attack tactics. The first version of the database was presented in 2013, every year it expanded and supplemented.
Threat Intelligence refers to the analysis of scanned EDR data when it is matched against known attacker tactics. When positively correlated with MITER ATT & CK patterns , the system will raise an alarm and, if necessary, can encapsulate the threat in a sandbox and disconnect suspicious machines from the computer network. At the same time, the collection of very detailed and systematized logs allows security engineers to quickly find a breach upon detection of the fact of intruders entering the system and further investigation of the incident.
Recently, the British company Micro Focus International presented a report on the current trends in information security. The 15-item survey was sent out to several hundred professionals from different countries. It turned out that 90% use the MITER ATT & CK base and 93% use AI and ML technologies.
AI-powered data analysis takes you to the next level, from Threat Intelligence to Threat Hunting. Security professionals simulate a variety of attacks on their company's infrastructure, identify vulnerabilities in advance, and take steps to strengthen them.
Another vector for AI applications in security is the analysis of employee behavior.
A map of the usual activity in the employee's account is drawn up, according to which his traffic and running programs are more or less the same day after day. And if it suddenly turns out that he logged in late at night, launches software that is atypical for him and tries to access an unknown address on the Internet, the system will raise the alarm and may block the account.
The future is near

Canadian science fiction writer Peter Watts in his gloomy Rifters trilogy, which takes place in the near future, describes a "brawn" - a clever gel consisting of nerve cells of the cerebral cortex, cultured on an artificial substrate. Scientists have learned to form connections in it, like those in the human brain, and to create high-performance biocomputers on its basis, surpassing computer neural networks in power. The main intrigue of the trilogy is connected with the peculiarities of the “thinking” of such devices, but I will tell you only about one area of their application.
In the future, computer viruses and network attacks clogged all information channels so much that the Internet, in our modern understanding, ceased to exist. Then, as antiviruses, they adopted “smart gels”, which could not be fooled by simple encryption and polymorphism; they tracked hacking patterns on the fly and immediately stopped them. This measure completely cleared computer networks of such threats.
Who knows. Maybe databases like the one MITER and machine learning collects will clear the internet of viruses faster than Peter Watts imagined? Although, cybercriminals can also use AI technologies. Moreover, there is evidence that they have already mastered them ...

