Winter. Time to wallow in the snow and play snowballs. Or read an article on stream ciphers. Who likes what more.
This article is an overview. We will talk about the principle of operation of version 1 of SNOW 1.0, briefly about the various attacks performed on the cipher and the use of its modifications.
basic information
And the most important, in my opinion.
SNOW cipher refers to word stream ciphers. It works with 32-bit words and supports both 128- and 256-bit keys and consists of a combination of a linear feedback shift register (LFLR) and a finite state machine (FSM).
It has 3 modifications. And one of them - SNOW 3G, is used for mobile data transmission. The latest version of SNOW-V was developed for 5G networks, but is not used yet.

A little about history
SNOW 1.0 , originally just SNOW, was developed in 2000 at Lund University (Sweden).
, SNOW NESSIE. 2003 SNOW 2.0, . ETSI SAGE , . 2006 SNOW 3G.
2019 Ericsson Research SNOW 3G , SNOW-V.
SNOW
. .
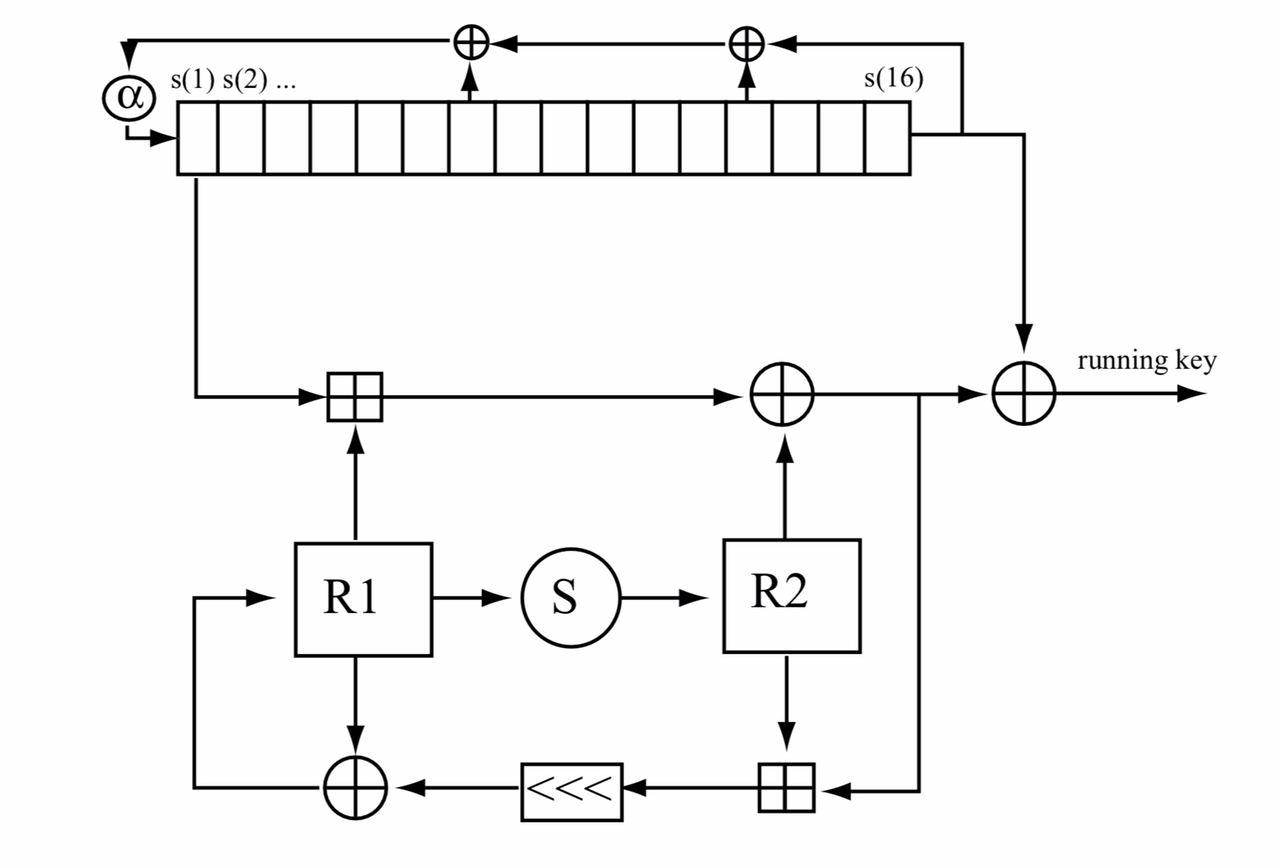
16 . . 32- , R1 R2, ( R1 R2). . . , R1, R2 . 32 . , 32 . .
t = 0 32- s(1), s(2),…, s(16) , .
,
,
.
. :
.
s(16) 2 ,
mod 2.
R1 R2 :
- ,
, S-, S(x), c S- 8×8 . 4 , 8 8 . , S-
2.
2002 «Guess and determine attack» SNOW 1.0, , . -, , s(1). . — SNOW 1.0.
-
2010 SNOW 3G SNOW 3G ⊕ . IV 18 33 SNOW3G ⊕
.
2020 Lin Jiao, Yongqiang Li Yonglin Hao SNOW-V «Guess and determine attack». .. , SNOW 1.0. , , . ?
SNOW 2.0 — , ISO/IEC 18033-4, , .
SNOW 3G 3GPP UEA2 UIA3.
SNOW-V , !
STRUMOK ( : 8845:2019 ""), SNOW 2.0.
(The difference is in the length of the secret key and the initialization vector. SNOW 2.0 is also aimed at using in 32-bit computing systems, and STRUMOK in 64-bit ones).
Small summary
This cipher, of course, is not perfect .. Who is perfect? But it is modern and I think it has a future. The problem of secure data transmission has always been relevant and still remains!