There are now many IM messengers with end-to-end encryption, but there are far fewer options that you can quickly deploy on your server.
While studying the options, my eyes fell on Delta Chat, which was already mentioned on Habré - a messenger without a centralized server infrastructure, using mail servers to deliver messages, which allows you to deploy it, for example, on your home server and communicate from devices, including not with Internet access.
Among the advantages of this approach are:
- You manage your information yourself, including encryption keys.
- You don't give your address book to anyone.
- There is no need to use a phone number to register.
- Clients for all popular systems: Windows, Linux, Android, MacOS, iPhone.
- Additional STARTTLS / SSL encryption for message transmission provided by the mail server.
- Ability to configure the deletion of old messages from the device (disappearing messages).
- The ability to configure the deletion of messages from the server upon receipt.
- Fast delivery thanks to IMAP push.
- Group protected chats.
- Support for transferring files, photos and videos.
- The server and client are both open source and completely free.
Possible disadvantages:
- There is no way to create native audio and video conferences.
- The need to export / import encryption keys to set up one account on multiple devices.
Interesting fact: Roskomnadzor already demanded that Delta Chat developers provide access to user data, encryption keys and register in the state register of providers, to which Delta Chat refused, because do not have their own servers and do not have access to encryption keys.
End-to-end encryption
Delta Chat can use StartTLS or SSL connection to the server to connect to the server, messages by default will be encrypted according to the Autocrypt Level 1 standard , after the first messages are exchanged (they are transmitted in unencrypted form). Thus, if communication is between users of one server, information will not be transmitted to other servers, only our server and users' devices will be busy in the transmission of messages.
Server Tuning
Setting up a server for Delta Chat comes down to installing Postfix + Dovecot with StartTLS / SSL configured and setting up domain records.
To configure the server, I will use CentOS 8, for other distributions there may be minor discrepancies. We select the appropriate server parameters for our task.
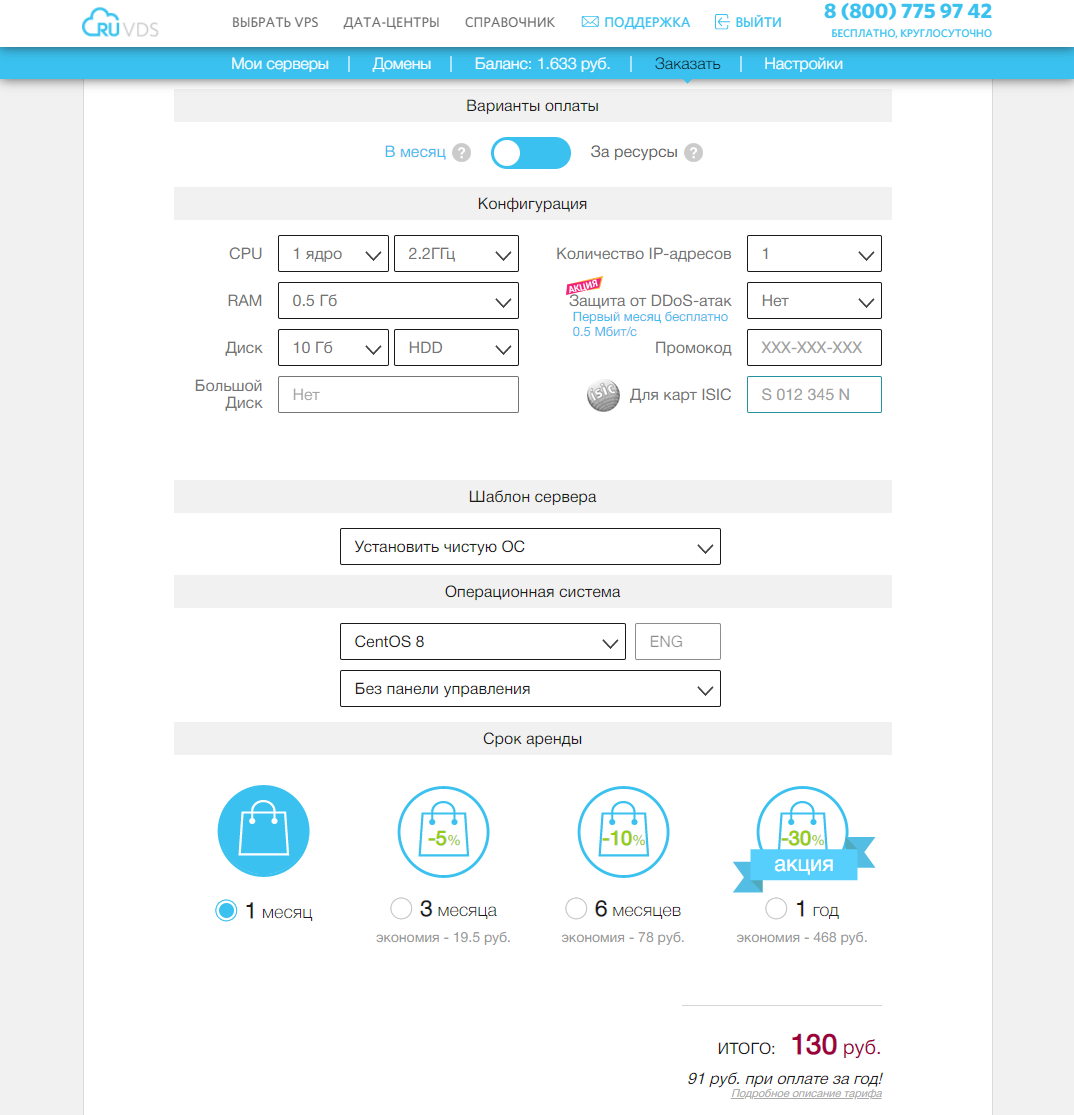
In DNS, I created two records: the third-level domain will be both the mail domain and the name of the mail server:
secureim.example.com A <ip> secureim MX secureim.example.com
Let
hostname
's set and install postfix, dovecot and nginx (nginx - to get let's encrypt certificates, wget - to install certbot-auto, nano - editor):
hostnamectl set-hostname secureim.example.com
dnf install postfix dovecot nginx wget nano -y
Let's allow Postfix to receive mail from outside and configure the hostname, domain and origin of the server, since the mail domain and server address are the same, the domain will be the same everywhere:
postconf -e "inet_interfaces = all"
postconf -e "myhostname = secureim.example.com"
postconf -e "mydomain = secureim.example.com"
postconf -e "myorigin = secureim.example.com"
In order for Delta Chat to be available for connection from the Internet, you need to open ports 80, 143, 443, 465, 587, 993. Also, open ports 80, 443 to get let's encrypt certificates and update them in the future. If you plan to receive letters from other mail servers, you will also need to open port 25 (in my case, I do not plan to connect using other servers, so I do not specify the 25th port). And you may need to add port forwarding 80, 143, 443, 465, 587, 993 on the router if the server is going to be used on a local network.
Let's open ports 80, 143, 443, 465, 587, 993 in the firewall:
firewall-cmd --permanent --add-service={http,https,smtps,smtp-submission,imap,imaps} systemctl reload firewalld
Let's create site settings for our domain name in order to get let's encrypt certificates using certbot-auto
nano /etc/nginx/conf.d/secureim.example.com.conf server { listen 80; listen [::]:80; server_name secureim.example.com; root /usr/share/nginx/html/; } }
Let's enable and run nginx:
systemctl enable nginx
systemctl start nginx
Install certbot-auto:
cd ~
wget https://dl.eff.org/certbot-auto
mv certbot-auto /usr/local/bin/certbot-auto
chown root /usr/local/bin/certbot-auto
chmod 0755 /usr/local/bin/certbot-auto
yes | certbot-auto --install-only
Let's generate certificates for the site (in the future we will use them for TLS encryption of the connection to the server):
certbot-auto certonly -a nginx --agree-tos --staple-ocsp --email my_mail@example.com -d secureim.example.com
Certificates will be created and their location will also be displayed in the console:
# /etc/letsencrypt/live/secureim.example.com/fullchain.pem
# /etc/letsencrypt/live/secureim.example.com/privkey.pem
Correctly correct the Postfix configuration file to allow receiving messages on ports 465 and 587:
nano /etc/postfix/master.cf submission inet n - y - - smtpd -o syslog_name=postfix/submission -o smtpd_tls_security_level=encrypt -o smtpd_tls_wrappermode=no -o smtpd_sasl_auth_enable=yes -o smtpd_relay_restrictions=permit_sasl_authenticated,reject -o smtpd_recipient_restrictions=permit_mynetworks,permit_sasl_authenticated,reject -o smtpd_sasl_type=dovecot -o smtpd_sasl_path=private/auth smtps inet n - y - - smtpd -o syslog_name=postfix/smtps -o smtpd_tls_wrappermode=yes -o smtpd_sasl_auth_enable=yes -o smtpd_relay_restrictions=permit_sasl_authenticated,reject -o smtpd_recipient_restrictions=permit_mynetworks,permit_sasl_authenticated,reject -o smtpd_sasl_type=dovecot -o smtpd_sasl_path=private/auth
Let's run the commands to specify the location of the TLS certificate and server private key:
postconf "smtpd_tls_cert_file = /etc/letsencrypt/live/secureim.example.com/fullchain.pem"
postconf "smtpd_tls_key_file = /etc/letsencrypt/live/secureim.example.com/privkey.pem"
If necessary, we can enable logging of TLS connections:
postconf "smtpd_tls_loglevel = 1"
postconf "smtp_tls_loglevel = 1"
Add the requirement to use protocols not lower than TLS 1.2 at the end of the Postfix configuration file:
nano /etc/postfix/main.cf smtp_tls_mandatory_protocols = >=TLSv1.2 smtp_tls_protocols = >=TLSv1.2
# Enable and run Postfix:
systemctl start postfix
systemctl enable postfix
Install, enable and run Dovecot:
dnf install dovecot -y
systemctl start dovecot
systemctl enable dovecot
Modify the Dovecot config file to enable imap protocol:
nano /etc/dovecot/dovecot.conf protocols = imap
Let's configure the mail storage so that messages are saved in user folders:
nano /etc/dovecot/conf.d/10-mail.conf mail_location = maildir:~/Maildir mail_privileged_group = mail
Add Dovecot to the mail group so that Dovecot can read incoming messages:
gpasswd -a dovecot mail
Deny authorization without TLS encryption:
nano /etc/dovecot/conf.d/10-auth.conf disable_plaintext_auth = yes
Add domain auto-substitution during authorization (only by username):
auth_username_format = %n
Let's change the location of the certificate, key, the location of the Diffie-Hellman key file, the minimum TLS 1.2 version, and the preference for choosing server encryption protocols over the client:
nano /etc/dovecot/conf.d/10-ssl.conf ssl_cert = </etc/letsencrypt/live/secureim.example.com/fullchain.pem ssl_key = </etc/letsencrypt/live/secureim.example.com/privkey.pem ssl_dh = </etc/dovecot/dh.pem ssl_min_protocol = TLSv1.2 ssl_prefer_server_ciphers = yes
Let's generate a Diffie-Hellman key, key generation can take a long time:
openssl dhparam -out /etc/dovecot/dh.pem 4096
Let's change the service auth section so that Postfix can connect to the Dovecot authorization server:
nano /etc/dovecot/conf.d/10-master.conf service auth { unix_listener /var/spool/postfix/private/auth { mode = 0600 user = postfix group = postfix } }
Let's enable the auto-creation of system mail folders (in case we use the server for regular mail as well) by adding the auto = create line in the mail folders section:
nano /etc/dovecot/conf.d/15-mailboxes.conf
mailbox Drafts {
auto = create
special_use = \Drafts
}
mailbox Junk {
auto = create
special_use = \Junk
}
mailbox Trash {
auto = create
special_use = \Trash
}
mailbox Sent {
auto = create
special_use = \Sent
}
mailbox "Sent Messages" {
auto = create
special_use = \Sent
}
Let's configure Dovecot to deliver messages to the configured storage by adding the lmtp parameter:
nano /etc/dovecot/dovecot.conf protocols = imap lmtp
Let's configure the LMTP service as follows:
nano /etc/dovecot/conf.d/10-master.conf service lmtp { unix_listener /var/spool/postfix/private/dovecot-lmtp { mode = 0600 user = postfix group = postfix } }
Add the following settings to the end of the file to tell Postfix to deliver mail to local storage via the Dovecot LMTP service. Also disable SMTPUTF8, since Dovecot LMTP does not support this extension:
nano /etc/postfix/main.cf mailbox_transport = lmtp:unix:private/dovecot-lmtp smtputf8_enable = no
Let's create users who will use the server by creating a corresponding entry in the system and giving it a password that will be used for authorization via smtps and imaps:
adduser user1 passwd user1
# Restart Dovecot and Postfix:
systemctl restart dovecot systemctl restart postfix
Add a task to / etc / crontab to automatically renew certificates:
nano /etc/crontab
30 2 * * * root /usr/local/bin/certbot-auto renew --post-hook "nginx -s reload"
At this stage, the server should function as a mail server, i.e. you can connect with a mail client and try to send and receive letters to other mailboxes of this server, or if you have opened port 25 above, then to other mail servers.
Now let's set up the Delta Chat client on a PC and Android smartphone.
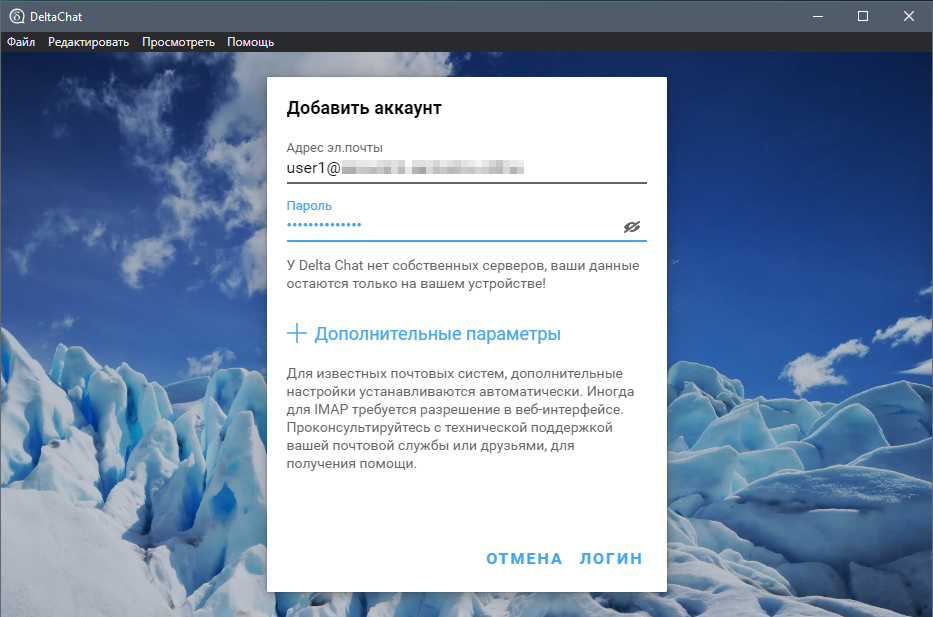
To connect, it is enough to enter the mail address and password created earlier on the server, Delta Chat will determine which ports can be used, after which it will be possible to add a new contact, also by e-mail address, using a valid mail address.
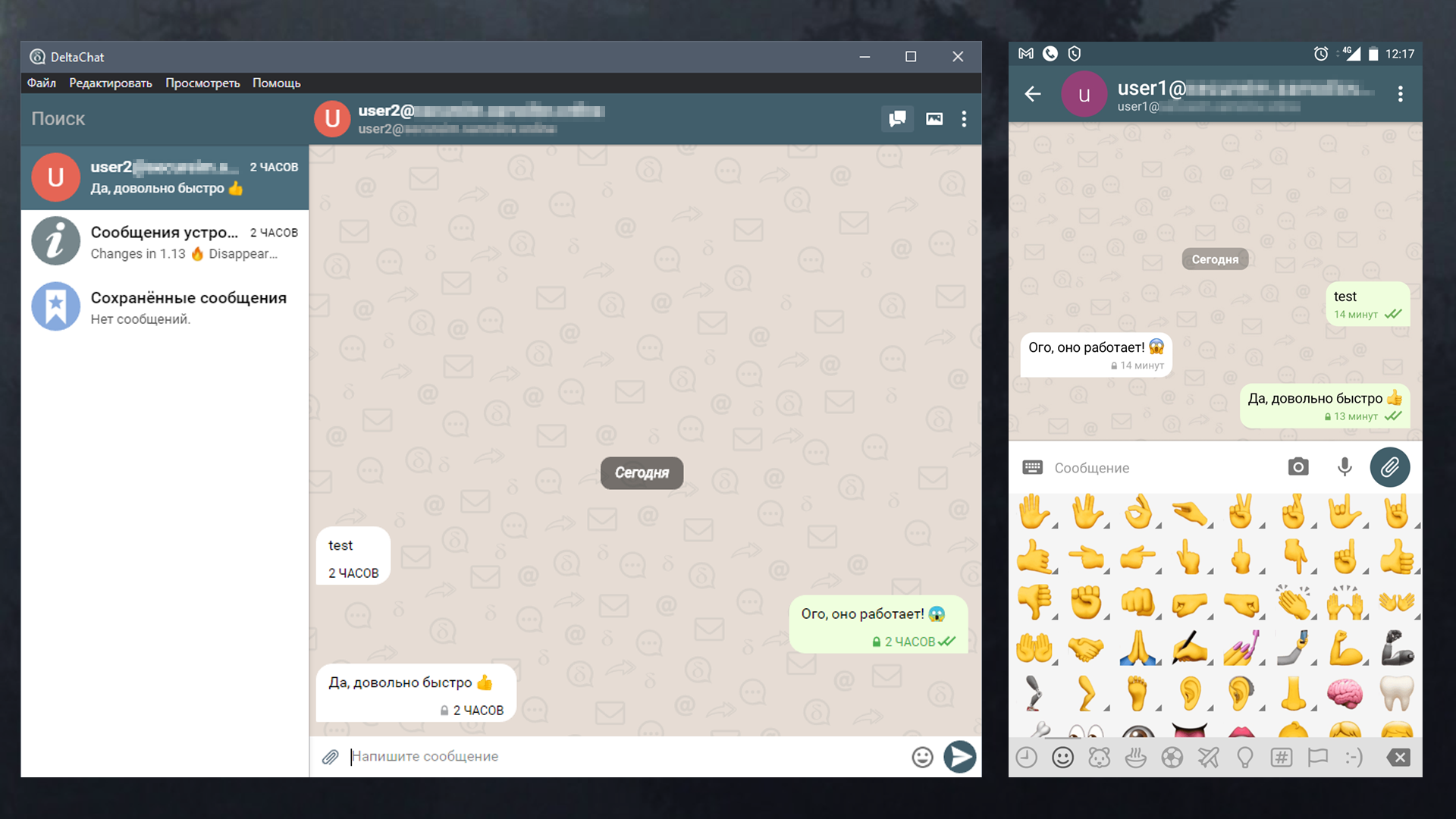
The first messages will be sent unencrypted, at this stage the key exchange is in progress. Further, messages will be encrypted in addition to TLS used for data transmission, end-to-end encryption Autocrypt Level 1.
It is also possible to create a group verified chat - where all messages are encrypted end-to-end encryption, and participants can join by scanning the invitation with a QR code. In this way, all participants are linked to each other by a chain of invitations that guarantee cryptographic consistency against active network attacks or provider attacks.
One of the most interesting things I wanted to check was to see what the message looks like in the server store. To do this, I sent a message to an inactive account - in this case, the message will wait for its recipient on the server, and we, having access to the server, will be able to view it:
Message content
Return-Path: <user2@secureim.example.com>
Delivered-To: user1@secureim.example.com
Received: from secureim.example.com
by secureim.example.com with LMTP
id g/geNIUWzl+yBQAADOhLJw
(envelope-from <user2@secureim.example.com>)
for <user1@secureim.example.com>; Mon, 07 Dec 2020 14:48:21 +0300
Received: from [127.0.0.1] (unknown [192.87.129.58])
by secureim.example.com (Postfix) with ESMTPSA id AA72A3193E11
for <user1@secureim.example.com>; Mon, 7 Dec 2020 11:48:21 +0000 (UTC)
MIME-Version: 1.0
References: <Mr.DoII3_YQLLv.2m_e6hIHc0e@secureim.example.com>
<Mr.YwnXrWVn2Ai.FAQ-abJC0kt@secureim.example.com>
In-Reply-To: <Mr.YwnXrWVn2Ai.FAQ-abJC0kt@secureim.example.com>
Date: Mon, 07 Dec 2020 11:48:20 +0000
Chat-Version: 1.0
Autocrypt: addr=user2@secureim.example.com; prefer-encrypt=mutual;
keydata=xjMEX83vexYJKwYBBAHaRw8BAQdAYgkiTiHDlJtzQqLCFxiVpma/X5OtALu8kJmjeTG3yo
7NIDx1c2VyMkBzZWN1cmVpbS5zYW1vaWxvdi5vbmxpbmU+wosEEBYIADMCGQEFAl/N73sCGwMECwkI
BwYVCAkKCwIDFgIBFiEEkuezqLPdoDjlA2dxYQc97rElXXgACgkQYQc97rElXXgLNQEA17LrpEA2vF
1FMyN0ah5tpM6w/6iKoB+FVUJFAUALxk4A/RpQ/o6D7CuacuFPifVZgz7DOSQElPAMP4AHDyzcRxwJ
zjgEX83vexIKKwYBBAGXVQEFAQEHQJ7AQXbN5K6EUuwUbaLtFpEOdjd5E8hozmHkeeDJ0HcbAwEIB8
J4BBgWCAAgBQJfze97AhsMFiEEkuezqLPdoDjlA2dxYQc97rElXXgACgkQYQc97rElXXhYJgEA+RUa
RlnJjv86yVJthgv7w9LajPAgUGCVhbjFmccPQ4gA/iiX+nk+TrS2q2oD5vuyD3FLgpja1dGmqECYg1
ekyogL
Message-ID: <Mr.qg4Mj0zMVZw.lT9nBnZMoKs@secureim.example.com>
To: <user1@secureim.example.com>
From: <user2@secureim.example.com>
Subject:…
Content-Type: multipart/encrypted; protocol=«application/pgp-encrypted»;
boundary=«OfVQvVRcZpJOyxoScoY9c3DWqC1ZAP»
--OfVQvVRcZpJOyxoScoY9c3DWqC1ZAP
Content-Type: application/pgp-encrypted
Content-Description: PGP/MIME version identification
Version: 1
--OfVQvVRcZpJOyxoScoY9c3DWqC1ZAP
Content-Type: application/octet-stream; name=«encrypted.asc»
Content-Description: OpenPGP encrypted message
Content-Disposition: inline; filename=«encrypted.asc»;
-----BEGIN PGP MESSAGE-----
wU4DKm2PBWHuz1cSAQdA4krEbgJjac78SUKlWKfVyfWt2drZf41dIjTH01J52HIg
aY/ZzCn/ch8LNGv3vuJbJS8RLHK7XyxZ4Z1STAtTDQPBTgNyNpRoJqRwSxIBB0AC
OVrbhsjNPbpojrm/zGWkE5berNF7sNnGQpHolcd+WyCdpqQAk3CaiQjxsm7jdO0A
gMtmXABw/TWcpTU/qOfW/9LBVwFZ/RPCKxCENfC0wau4TI+PMKrF0HODyWfBkEuw
e3WlQpN/t0eSUPKMiMhm7QM0Ffs52fPz0G6dfVJ2M6ucRRyU4Gpz+ZdlLeTLe3g2
PkKbb6xb9AQjdj/YtARCmhCNI48sv7dgU1ivh15r37FWLQvWgkY93L3XbiEaN/X9
EWBQxKql/sWP01Kf67PzbtL5uAHl8VnwInCIfezQsiAsPS2qiCb1sN3yBcNlRwsR
yTs2CPJTIi7xTSpM1S/ZHM5XXGnOmj6wDw69MHaHh9c9w3Yvv7q1rCMvudfm+OyS
/ai4GWyVJfM848kKWTCnalHdR4rZ3mubsqfuCOwjnZvodSlJFts9j5RUT87+j1DM
mQa4tEW8U5MxxoirFfbBnFXGUcU/3nicXI5Yy6wPP8ulBXopmt5vHsd68635KVRJ
2GMy7sMHcjyzujNCAmegIQgKqTLO5NUOtxW7v1OXL23pKx32OGcy8PtEJp7FBQYm
bUNAaz+rkmC971S2FOU0ZGV8LNp8ULioAbL629/JpPHhBOBJCsVnsXDIh6UBPbuM
06dU7VP6l8PNM87X/X1E3m2R1BCNkZghStQrt16fEoA+jm9F6PNtcap2S5rP9llO
klo/ojeciqWl0QoNaJMlMru70TT8a9sf6jYzp3Cf7qFHntNFYG1EcEy9YqaXNS7o
8UOVMfZuRIgNqI9j4g8wKf57/GIjtXCQn/c=
=bzUz
-----END PGP MESSAGE-----
--OfVQvVRcZpJOyxoScoY9c3DWqC1ZAP--
As you can see, letters are stored on the server in encrypted form, and if the server is seized by interested parties, the messages will not be at risk.
For greater reliability, you can use full disk encryption of the server and the device on which the client is running, as well as use keys to connect to the server via ssh and use strong, complex passwords for mail accounts.
Conclusion
Delta Chat is an interesting alternative for a self-hosted IM messenger, which allows you to exchange messages using existing mail protocols (which in the future allows you not to worry about blocking), and high resistance to interception of messages, the absence of a central server and the ability to deploy on your server, allows you not to worries about your data falling into the wrong hands.

