
Hey. We, the CrowdSec project team, are pleased to announce the release of CrowdSec 1.0.0. This release is extremely important because in addition to adding a few new features, the entire project has undergone major architectural changes to become faster, taller and stronger.
First of all, we are glad to present you the main change in this patch - the introduction of the local REST API. Thanks to him, the entire project has seriously changed its architecture towards simplifying and facilitating the interaction of components at the local level. However, overall ease of use has not suffered - using CrowdSec is still easy and pleasant.
For those who do not know about CrowdSec or are wondering how the French startup ended up on Habré, let's make a small digression:
, , , Fail2Ban: «CrowdSec — Fail2Ban ».
, , IT-. . , — .
, . , , . 1.0.0 :)
How it was and how it became
The main thing that happened with the release of version 1.0 was the introduction of changes to the architecture, which happened due to the introduction of the local REST API into the work. From an architectural point of view, our system consists of three main components:
- a constantly running CrowdSec service that monitors logs, attacks, etc .;
- command line, interface for interacting with the service;
- integration modules (bouncers) to ensure the blocking of attacking addresses.
Below is a diagram of how CrowdSec worked before:
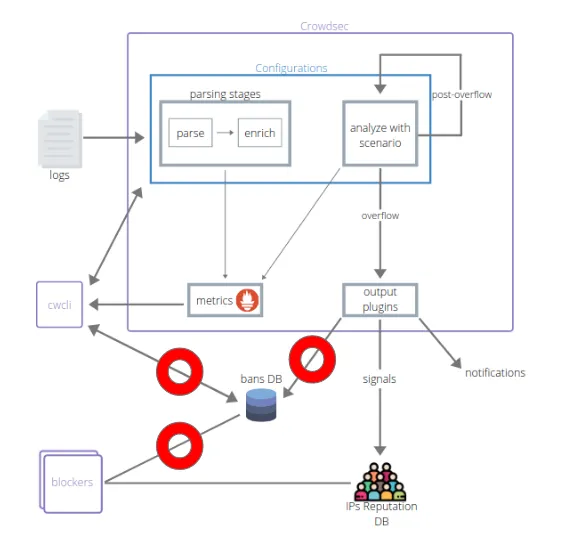
As you can see from the diagram, at least three elements of the system constantly accessed the database directly. In the diagram, these directions are marked with red circles (cwcli-DB, output plugins-DB, Bouncers-DB). At the same time, "Bouncers" means at least five modules that constantly communicate between the reputation database and the database of banned IP addresses.
When you develop a project from scratch, these crutches are an easy, quick and cheap way to create a working prototype of a system. However, if we talk about stability and speed of work, so many points of access to the database are not the best solution. This architecture of the project led to the emergence of a number of limitations that we encountered at the stages of further development of CrowdSec. Therefore, we wanted to get rid of them as quickly as possible.
After redesigning the project at the architectural level, we came to the decision that the best option would be a local REST API, through which the communication of the above components and the database will already pass.
As a result, we got the following architecture:
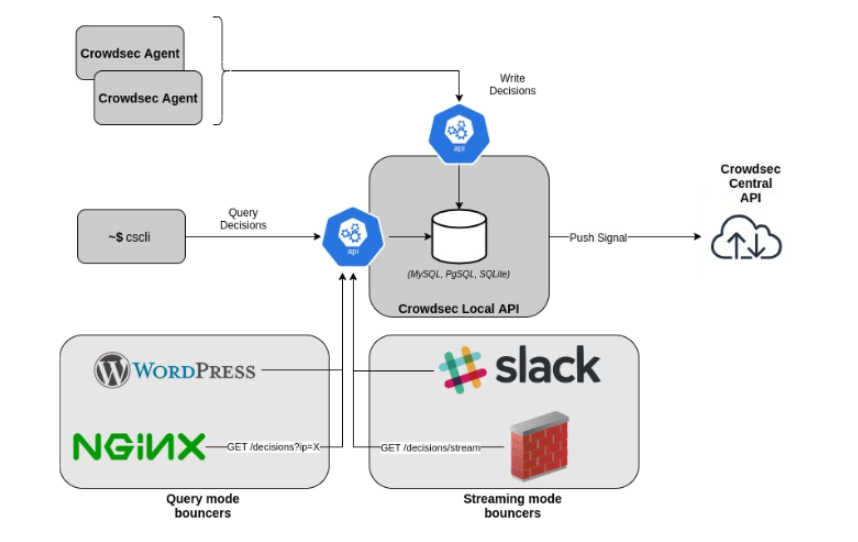
Now all internal modules communicate with each other and with the database exclusively through the REST API.
The main advantage of the API over the old implementation is the simplification of the modules (Bouncers) compared to the old version of CrowdSec. If earlier the bouncer accessed various databases directly, now, thanks to the work through the REST API, he only needs one HTTP-get request with an API token. All other work happens on the API side.
CrowdSec cloud scheme
In the classic view, it is assumed that one of the machines will have the server part of CrowdSec, which, through the new API, will be able to manage modules on other machines within the network defined by the administrator. If desired, the user can use his own database of banned addresses, or access our database on a paid basis. However, creating a single point of communication between the local REST API and our own API creates a new opportunity: the operation of CrowdSec on a model close to cloud SaaS.
Now the administrator does not need to deploy a full-fledged CrowdSec server part with a local REST API on his machine. Instead, it can use our external central CrowdSec API and only use bouncers to secure the network.
Additionally
For those who have used CrowdSec before, we suggest that you check out the full list of changes in version 1.0.0 relative to version 0.3.x on GitHub .
New users are advised to refer to information from our repository on GitHub .
We would like to point out that CrowdSec is an open source tool that is released under the free MIT license. Thus, anyone can use it absolutely free. The project has not yet been monetized , we are at the stage of developing our own ban list and tariff plans. On our site hub.crowdsec.net specially for new users, collections, configurations and ready-made bouncers are collected to facilitate customization and start using CrowdSec.
You can ask any question about our project right here in the comments. Using English will simplify communication - we will not have to use Google.Translate or ask Russian-speaking friends to translate your message for us.