
Can I just once again state my love for [WireGuard] and hope it gets merged soon? Maybe the code isn't perfect, but I've skimmed it, and compared to the horrors that are OpenVPN and IPSec, it's a work of art.
Linus Torvalds, on the Linux Kernel Mailing List
I am sure that many have already heard about Wireguard. Some even felt it live. I quite liked it in production, both in terms of performance and ease of configuration. Yes, there are no million mysterious configurations for all occasions like OpenVPN and XFRM + StrongSwan in IPSEC VPN. It is simple and concise both in code and in configs. It will not become bold and clumsy yet. In short, such a positive version of the "burn the legacy and write everything right" scenario.
I decided not to write another guide "how I installed Wireguard", but to share some useful utilities. Some with a very successful GUI for my taste, which is appropriate for services with many users. We will analyze the use of this VPN for communication between nodes in different Kubernetes clusters, several web-GUIs for generation and a couple of useful resources.
Why is it needed at all?
The key question. One of the coolest things about him is that he is very productive. In most cases, there is less latency and higher throughput with an equal CPU load. If you pay for the resources spent or plan to rent virtual machines taking into account peak loads, then this type of VPN will also save you money. I think it is not necessary to explain why it is bad to drive traffic over open networks between individual nodes.
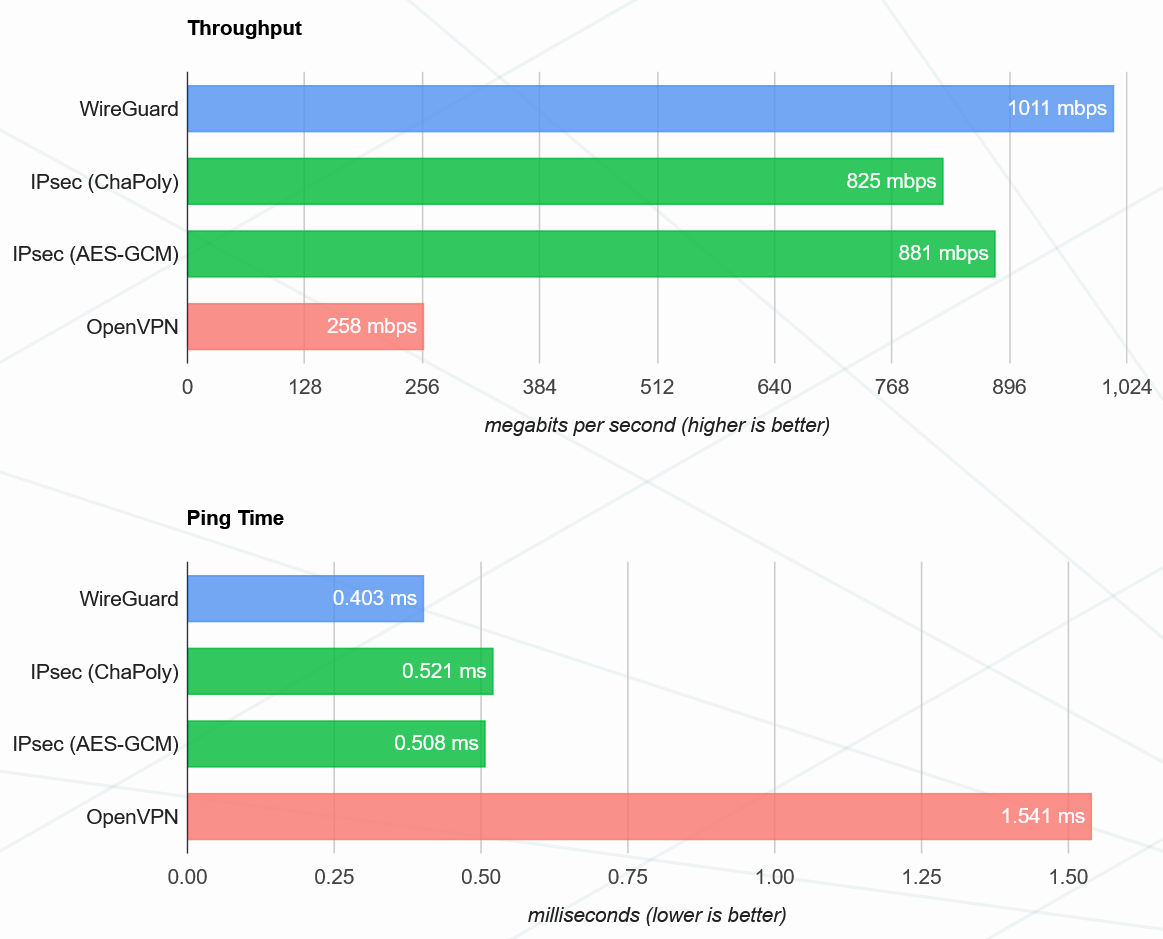
Source: www.wireguard.com/performance
Moreover, it is worth noting that it has been included in the kernel since Linux 5.6, and since the spring of this year it has also been included in the main branch of the Android kernel, which gives us excellent energy efficiency on mobile phones ... Although, I must say that he did not particularly strain the phone battery before.
Kilo - wireguard for Kubernetes
Very often, companies larger than the average have situations where they need to use several different clouds. The reasons are different - fault tolerance, good presence in the region and low pings. Sometimes prices are for specific products. For example, you can run the frontend and main logic on your own servers, and outsource GPU-hungry tasks to AWS instances.
How it works? Kilo requires a wireguard kernel module on all nodes. If you are using kernels newer than 5.6, then the module will already be in the main branch and you will not have to add anything. Next, the kilo agent, "kg", runs on each node in the cluster, setting up private and public keys to set up a VPN. Traffic routing rules between separate regions are also automatically configured. Kilo can also work in conjunction with other networking solutions for clusters, such as Flannel. At the same time, kilo will provide communication between regions, and Flannel will take care of traffic within one location.
When building a network topology, it relies on topology.kubernetes.io/region , but you can also mark up regions manually.
Requirements:
- Kernel newer 5.6 or separate wireguard module
- White IP at the nodes, to organize a direct connection between them.
For more information, see last year's developer talk at the Kubernetes Forums in Seoul and the documentation .
wg-gen-web

What is called "yet another config generator". But very pleasant to work with. The main difference in the approach is that the author does not try to edit the configuration of a running service on the fly, but only provides a convenient GUI for generating rules. Then you yourself implement the update of the configs to your taste.
Key features - generates convenient QR codes for mobile clients and sends all the necessary data for connection to the client's mail. Well, dockerized, of course. The repository is here .
Deploy is pretty simple:
docker run --rm -it -v /tmp/wireguard:/data -p 8080:8080 -e "WG_CONF_DIR=/data" vx3r/wg-gen-web:latest
Subspace

Another GUI for easy work with many client devices.
Main features:
- Single Sign-On using SAML. You can go under Google account.
- Add and remove devices in a few clicks
- Generation of individual configs for each device. Well, the QR code, of course.
- Let's Encrypt HTTPS out of the box and automatic redirect to port 443
Easy to deploy to VPS. By the way, we have them. We can sleep)
The wireguard must be installed on the server and the ports must be open: 80 / tcp, 443 / tcp, 51820 / udp (WireGuard). In this case, you need to remove the standard dnsmasq, since it will be launched in the container.
Then everything is pretty typical, only replace --env SUBSPACE_HTTP_HOST with your domain:
# Your data directory should be bind-mounted as `/data` inside the container using the `--volume` flag.
$ mkdir /data
docker create \
--name subspace \
--restart always \
--network host \
--cap-add NET_ADMIN \
--volume /usr/bin/wg:/usr/bin/wg \
--volume /data:/data \
--env SUBSPACE_HTTP_HOST=subspace.example.com \
subspacecloud/subspace:latest
$ sudo docker start subspace
The repository is here .
Instead of conclusions
If you haven't tried this VPN yet, I highly recommend it. Often he is able to revive not very powerful hardware, which could not cope under load earlier. It is also not very difficult to configure. True, its main task is still to pierce straight, pre-configured tunnels. Any dynamic configurations are not available to him in the usual sense. A price to pay for simplicity and performance.
By the way, if you don't know yet, wireguard is already included in the beta version of RouterOS 7.1 from MikroTik. You can try it now, but, according to my feelings, it is still damp.

Well, traditionally I can invite you to try to deploy wireguard on our VPS... For example, to wrap some of your home network traffic to Switzerland or the Netherlands. We have many different locations and the pricing policy is very pleasant for such tasks.
As I said, Wireguard is very resource efficient, so a minimal configuration with 1 core and 1 GB of RAM will be more than enough to support a large number of clients. The prices are also quite humane:
- Location in Amsterdam, London, Frankfurt - 503 ₽ / month
- And on the Moscow site, with a slightly simpler processor - 240 ₽ / month.

