
Today, let's look at how to test the security of a company's wireless network relatively quietly. The Raspberry Pi will be used as a basis, which supports Kali Linux installation. Installing the distribution is pretty straightforward:
- Download the official image from kali.org ;
- Burn it to SD disk using Win32image for Windows and Gparted for Linux;
- Launch Raspberry Pi with SD card installed.
Once installed, you can optionally update packages if available. But no further action is required to fully function. The required size of the memory card is 8GB or higher. For the system to function normally, it is desirable to use a larger volume.
The article is for informational purposes only. Do not break the law.
Now, when the system is ready for work, it remains only to configure the launch of programs at system startup, since it is assumed that the Raspberry Pi will be installed directly in range of the desired access point for autonomous collection of Wi-Fi authorization data. There are many tools for working with WPA2-Personal with varying degrees of interactivity, but the aircrack-ng suite is still a timeless classic . It includes various auxiliary modules that allow you to fully test wireless networks from switching the interface to monitor mode to brute-force password detection. In our case, we only need to intercept Wi-Fi handshakes and save them for later analysis.
This can be done using the crontab job scheduler. The corresponding lines need to be added to run the wifi.sh and eaphammer.sh scripts :
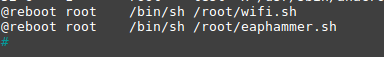
Wifi.sh will switch the wireless interface to monitor mode and run the airodump-ng tool, saving the found WPA2-Personal handshakes to a file for further analysis.

In the airodump-ng launch command, it is necessary to specify the parameters of the wireless interface and the file into which the received handshakes will be saved (data that is transmitted when the user connects to the access point) using the -w switch . Additionally, it is recommended to specify the BSSID (MAC address of the access point) using the key--bssid and the channel it is running on using -c . This is not necessary, but if you specify, then only the necessary data will be intercepted.
The second script will launch the eaphammer tool designed to hijack credentials when using the WPA2-Enterprise protocol.
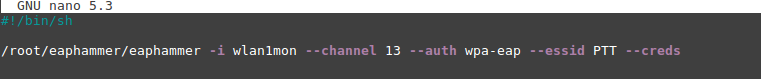
The tool works on the principle of an "evil twin", so it is mandatory to specify in the tool launch parameters:
- -i is the name of the network interface. If several tools using a wireless network are running at the same time, then additional interfaces must be added;
- --essid - access point name;
- --channel - channel on which the access point operates;
- --auth - authentication method;
- --creds - collection of accounts.
Also, to carry out an attack, you need to generate a certificate by running the command ./eaphammer --cert-wizard . In the interactive menu, you can specify absolutely any information, this will not affect the quality of the attack.

We save the settings, and in the future the scripts will run along with the system start.
Testing
To conduct testing, you need to position the Raspberry Pi in any convenient way within the range of the access point so that no one will notice it while the data is being collected. The unit needs to provide 5V and 2-2.5A power supply to operate . Having excluded the possibility of using an adapter to connect to an outlet, you need to think about a powerbank type battery to ensure uninterrupted operation for the entire duration of testing.
In the end, it remains only to pick up the installation and analyze the data obtained. When using eaphammer, data will be written as a handshake to the loot folder, which is located in the same place as the tool itself, but it is better to play it safe and add output redirection for writing to some file in the tool launch script. Then the analysis will only be to find the credentials in the output file.
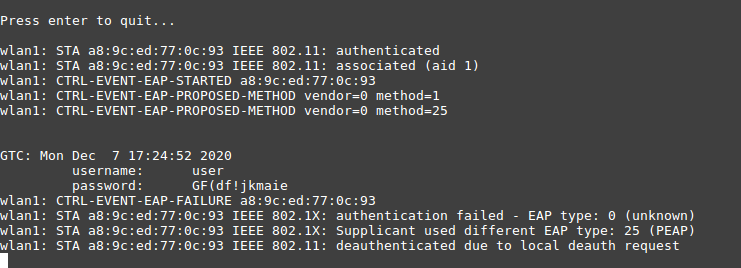
If it was possible to intercept the data for connecting to WPA2-Personal, then all that remains is to try to guess the password using the dictionary. Enumeration can be performed using different tools:
- using Aircrack-ng ;
- the Pyrit tool , which allows you to use when looking through the power of a video card;
- CowPatty - Provides brute force rainbow tables.
And also with the help of fairly popular brute force tools:
- John The Ripper Hashat — CPU, GPU.
Rainbow tables are specially calculated hashes that are used to recover passwords very quickly. They are databases in which a pre-computed hash corresponds to a password. If we talk about Wi-Fi, calculating rainbow tables takes as much time as a regular brute-force attack, but searching for a password using an already created rainbow table will take a few seconds. Therefore, if you need to check only one handshake for an access point, then there will be no difference between brute-force passwords and compiling rainbow tables. Using rainbow tables only makes sense when testing two or more handshakes, since testing multiple handshakes against rainbow tables takes the same amount of time as testing one.It is also worth noting a significant disadvantage of rainbow tables - they take up a lot of space, much more than a regular dictionary with passwords.
If we compare the performance of tools that allow using the power of the CPU and GPU when searching, then the difference between, for example, Aircrack-ng and Hashat will be quite significant. Even if we compare the brute force modes using the CPU and GPU powers separately when brute-force through Hashcat, then in the first case, using, for example, a CPU Xeon E5450, the speed will be ~ 3500 PMK / s, and when using a GPU, for example, GTX 1050Ti, the speed will increase to ~ 130,000 PMK / s.
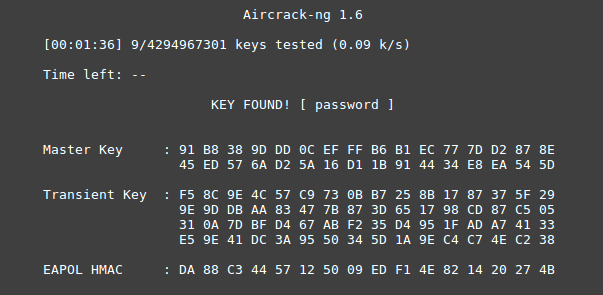
Based on the fact that only one handshake was intercepted, it would be more expedient to brute force the password using Aircrack-ng... Since initially only the number of the channel for which the handshakes were captured were indicated, when reading the dump, the list of access points working on this channel will be indicated, as well as information about whether a handshake was received for any of them.
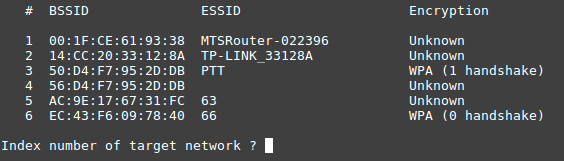
We select the “ PTT ” network of interest , and the search process begins. There are many different resources on the Internet where you can find a dictionary of interest, for example, here or here .
In addition to open resources, there are also specialized tools for generating your own dictionaries. One of these is Crunch , which is pretty simple to use:
crunch 8 9 1234567890 -o wordlist.txt
Where
- 8 9 - minimum and maximum length of passwords in the dictionary;
- 1234567890 - used symbols. It is allowed to use both numbers and letters, and special characters;
- -o is the file to which all variants will be written.
As a result, the password turned out to be " password ".
Tips for Reducing the Possibility of Compromising Your Wireless Network
- when using WPA2-Personal, the recommended password length should be more than the minimum required 8 characters; moreover, the use of dictionary passwords significantly reduces the time to guess them. As of 2020, some of the most popular 8-character passwords are still “12345678” and “password”;
- MAC- . , , , MAC- , . MAC- . , « » , ;
- . . . (VLAN) ;
- ;
- WPA2-Enterprise, , ;
- (WIPS). / . OSI, WIPS , “ ”.