
Nowadays, everyone has heard of the next generation 5G cellular networks. 5G is an integral part of the support for scripting of the Internet of Things . What is the Internet of Things in general? In simple terms, this is a set of devices that must interact with each other with minimal human intervention. Researchers believe 5G networks can be used for a wide variety of IoT scenarios , such as medicine , smart cities , traffic congestion control , emergency services , and industrial operations.etc. To implement such scenarios, 5G networks provide for new network architectures, services, applications and other mechanisms.

At the same time, the most important task in the design of such networks is to ensure security during the transfer and storage of data. Particular attention should be paid to the problem of security of multimedia content, which is supposed to be transmitted in a large number of scenarios. Modern classical (non-quantum) cryptography methods are still robust enough for use in modern technology. However, the rapid development of quantum computing calls into question , , . . - , 5G.
, , . , , . , . , «» , . , .

. - , , - , . , N . : «» ( ) «» ( ). « » . , , . .
«» |c⟩ «a» |x⟩:
:
« »:
«»:
w :
:
, . S. .

: . . , .

S-
- . . .
S-, B :
, : N, , «» « ». N.
B S-, R.
R , S.
S- R S.
:

, 5G. , f m x n 3 :
, : N, , , “” “ ”. N × N.
.
K 0 255.
xor ( ) K.
S- n m .
S-
. .
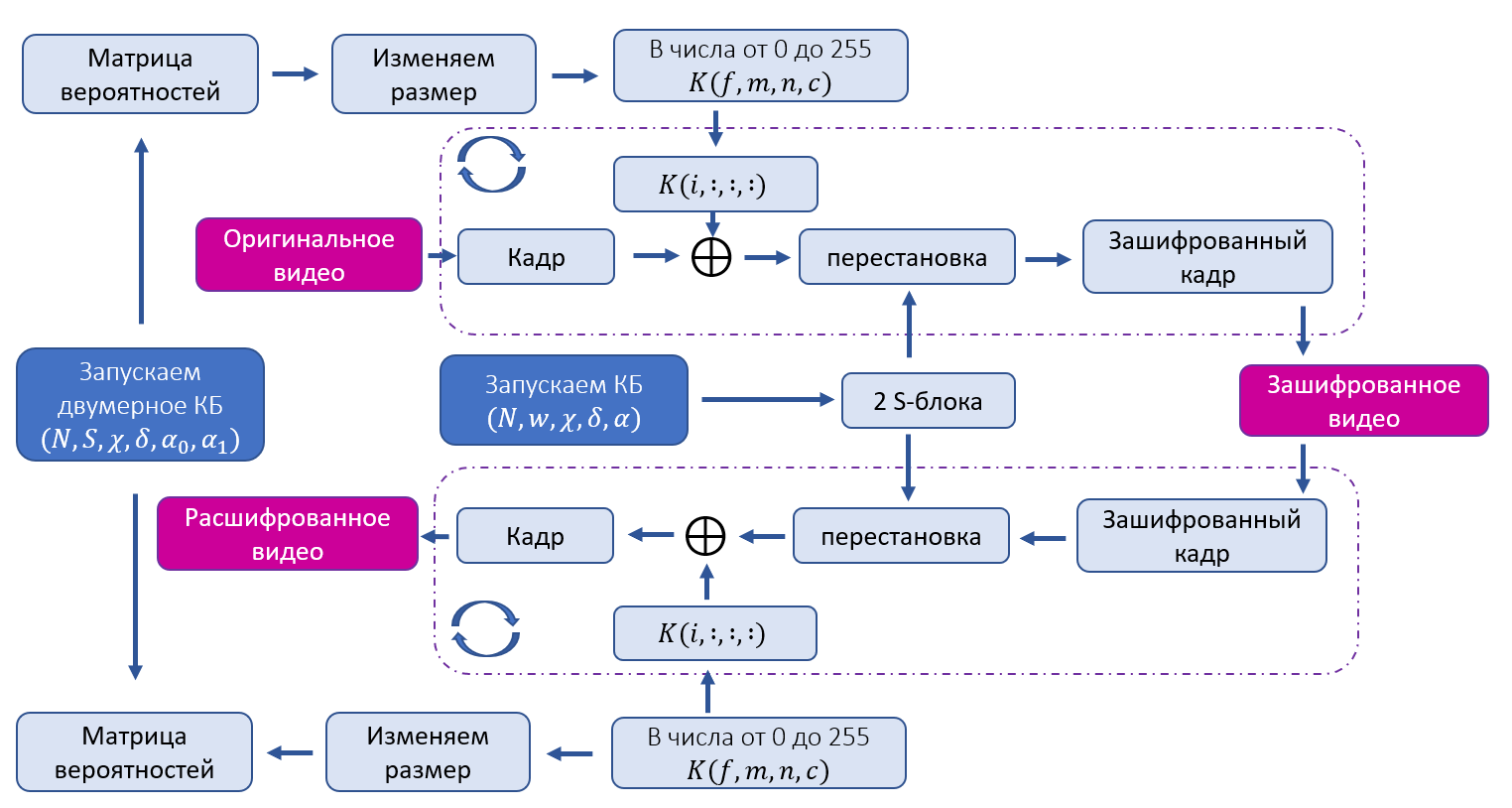
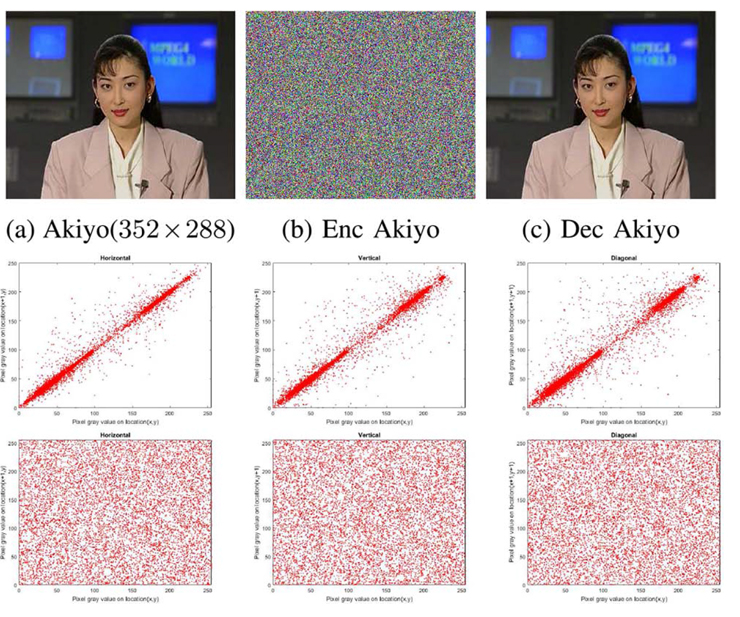
. () () . , , .
5G. : , , , .., . BF :
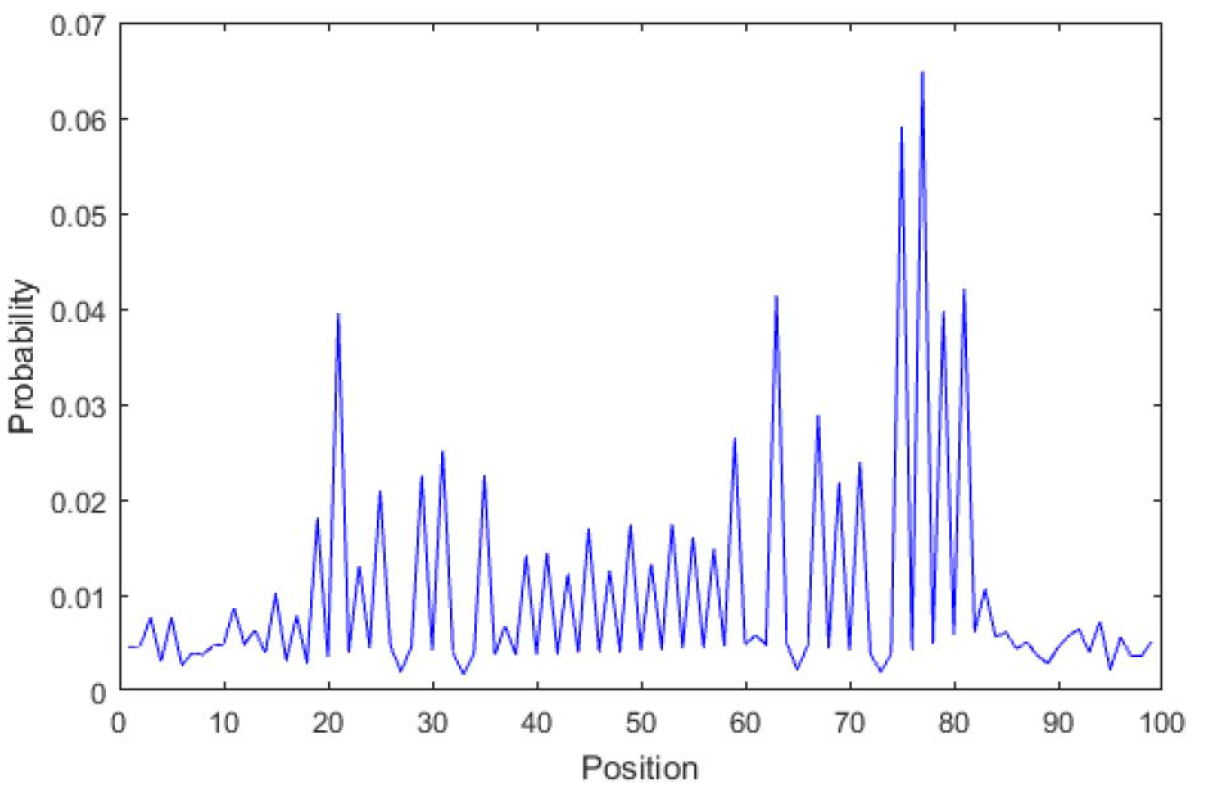
P N × N ( 1 ).
P PK length(BF) / 8.
PK K.
xor ( ) BF K.
S- 256
S- .
. .
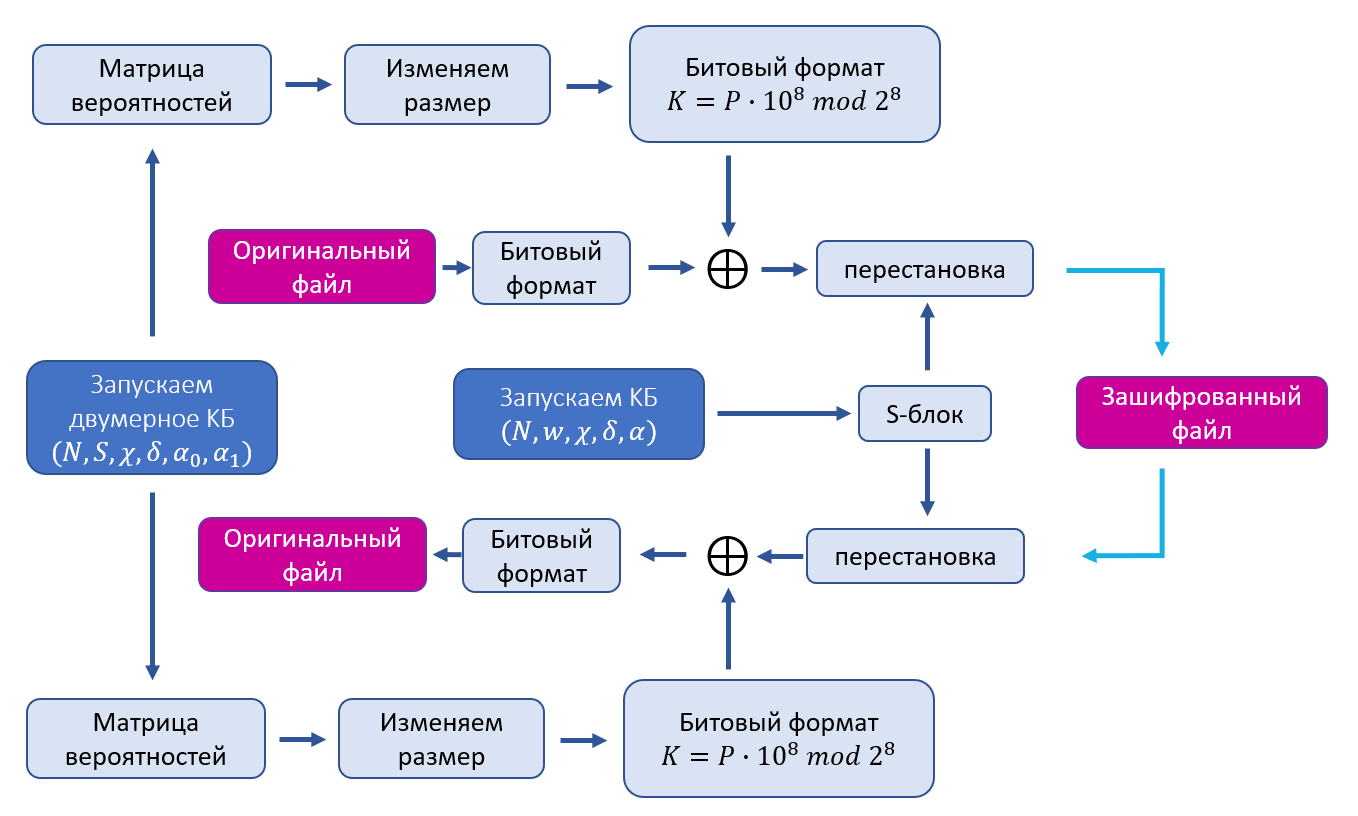
, , . . , .
5G
, 5G, . 5G, . . . . , .

In conclusion, it is worth noting that despite the fact that in the original work these algorithms are proposed for use in 5G networks, nothing prohibits their use in any other networks and systems. So do not be surprised if in the near future such algorithms will become a part of our everyday life.