Account lockouts are a hassle for system administrators and are common in Active Directory (AD). According to research , account lockouts are the most common reason for calling IT support.
And the main reason for blocking Active Directory accounts (other than when users forget their password) is a running app or background service on the device that authenticates with outdated credentials. As users are required to use more devices, this problem is compounded. To solve this problem, sysadmins need to find the application that is running with outdated credentials and then either stop it or ask the user to update the credentials.
The way Active Directory handles account locks is not up to date. In the past, when most Office users were logged in from one device, it was easy for them to keep track of their credentials. But now the situation has changed.
In this article, we will explain in more detail how Active Directory account locks occur, how to fix them, and how to create a policy that will reduce the time and resources spent on unlocking accounts.
At a Glance: Most Common Reasons for Blocking Active Directory
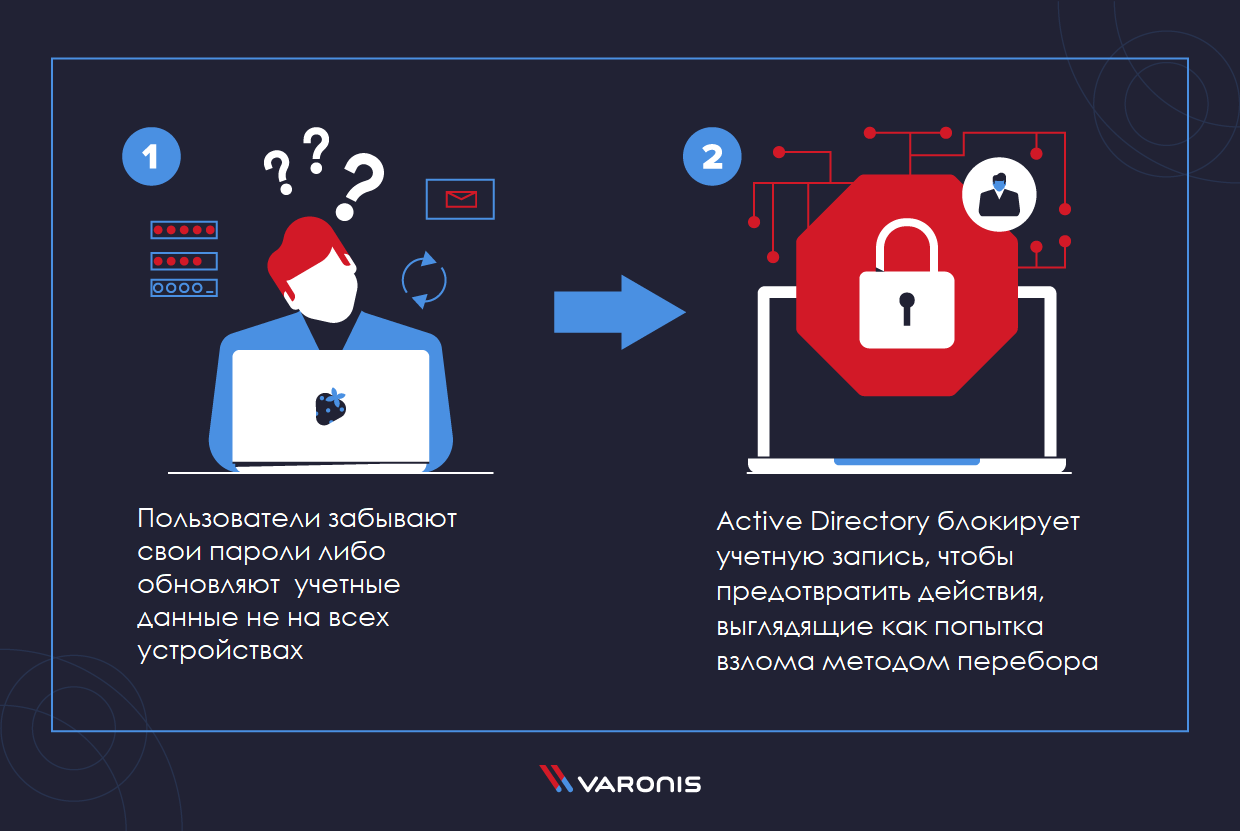
Most Active Directory account locks occur for one of two reasons: either users forget their passwords , or they do not update their credentials on all devices .
In the first case, when a user forgets a password, the administrator just needs to reset the user's credentials, remind them that it is important to create a strong password, or even advise them to use a password manager to reduce the number of passwords to remember. In the second case, when some device or service tries to log in with old data, this problem requires a more complex solution, and this is what we will look at in our article.
The basic mechanics of this type of account lockout are as follows. By default, Active Directory blocks a user after three unsuccessful login attempts. In most cases, when a user is prompted to update their Active Directory account credentials, they do so on their most used device. Any other device for this user can retain the old credentials, and programs or services will automatically continue trying to access Active Directory using them. Since the credentials on these devices are no longer valid, they will not be able to log in, and Active Directory will very quickly lock the account to prevent what looks like a brute-force attack.
In most cases, sysadmins will be forced to identify the source of these illegal login attempts and either block them or ask the user to update their credentials. In today's environment, where users may need to log in from dozens of different sources, finding the root cause can be a daunting task, as well as developing an appropriate blocking policy that can reduce the frequency of such problems. Later in the article, we'll show you how to deal with both.
Common Reasons for Blocking in Active Directory

Before we talk about solutions to help with your account lockout issue, it's worth noting that besides the above two most common account lockout reasons, there are many others.
Microsoft has an entire TechNet article on how to troubleshoot blocking issues, and the list includes:
- Programs that have old credentials in their cache
- changing passwords in service accounts;
- setting too low a threshold for incorrect password entry;
- user login on multiple computers;
- saved usernames and passwords contain outdated credentials;
- scheduled jobs with outdated credentials;
- assigning drives with outdated credentials;
- incorrect replication of Active Directory;
- interrupted terminal server sessions;
- outdated service account logins.
Troubleshooting Active Directory blocking issues will be easier if you have a good understanding of the basics of Active Directory. We've written many tutorials to help you master Active Directory. We recommend starting with our guide to the best Active Directory tutorials . Make sure you understand the difference between users and computers in Active Directory , the way Active Directory services work , and the difference between AD and LDAP .
Once you understand these topics, you will have an excellent understanding of how account blocking works.
Solving the problem of blocking accounts

Because of the many potential causes of Active Directory account lockouts, system administrators often have to go to great lengths to resolve this issue. System administrators should configure the system to track the number of lock-enabled users in a domain forest so that they can troubleshoot lock-out issues before they are inundated with user calls.
The first steps
When you first identify a blocked account, the first and most important task is to determine if the block is caused by a cyber attack.
To make sure you have enough information to investigate, there are several key steps you should take:
- Ensure that the latest service packs and hotfixes are installed on the domain controllers and client computers.
- Configure computers for data collection:
- enable auditing at the domain level;
- enable Netlogon logging;
- enable Kerberos logging.
- Analyze data from event log files and Netlogon log files. This will help determine where and for what reason the locks occur.
- Analyze the event logs on the computer generating account locks to determine the cause.
If, after reviewing these logs, you see hundreds (or thousands) of failed login attempts, you are probably seeing a brute-force attack on your systems and you should take immediate action. If it turns out that the blockage was caused by ordinary reasons, you need to find out how it happened.
Factors to Consider in a Blocking Policy
If you constantly experience multiple types of Active Directory account lockouts, you can fix this by reviewing your lockout policy.
Many administrators will tell you that most, if not all, account lockouts can be addressed by implementing smarter Active Directory account lockout policies . Proponents of this approach recommend that the administrator go to the default GPO for the domain and change the appropriate blocking settings to more appropriate ones.
Account lockout threshold parametershould be changed to a much larger number than 3 - perhaps 20 or 30 - so that the blocking is only triggered by a brute-force attack by a hacker (in this case, there are hundreds of attempts).
The account lockout duration - the time to wait before automatically unlocking an account - should be set to 10 minutes (instead of, say, 12 hours), or the default value of zero (which means permanent lockout) ...
Finally, the tricky "reset account lockout policy after" setting is set to 1 minute by default. You can read more about this approach here .
After getting professional advice from several Varonis engineers, I learned that changing the default Active Directory blocking settings can also help. But you need to be careful with this, as you first need to check the overall strength of employee passwords. If your password policy is strong, then increasing the "Account Lockout Threshold" might make sense, otherwise it might not work. In addition, there is a good argument that this threshold should always be zero. As a result, users will be forced to contact support to unblock their accounts.
Ultimately, the approach you take will depend on your environment and the number of blockages you encounter on a daily basis. You should strive to implement a lockout policy that will control the number of account reset attempts while still being able to catch intruders trying to break into your network.
Three tools for working with Active Directory account locks

Active Directory account lockouts are so common and such a source of frustration for network administrators that several tools have been specifically designed to address the problem. Some are provided by Microsoft and others are offered by third parties. Here is a list of the best ones:
Account Lockout Status Software
This is a standard set of tools that Microsoft provides for managing Active Directory account lockout. It consists of a number of individual components.
Each of these will help you explore different aspects of your network:
- EventCombMT.exe collects and filters events from the event logs of domain controllers. This tool has a built-in search for account locks. It collects event IDs associated with specific account locks into a separate text file that can then be exported.
- LockoutStatus.exe , . , .
- Netlogon Netlogon NT LAN Manager (NTLM). Netlogon — . Netlogon NLParse.exe, .
- Acctinfo ADUC ( Active Directory), lastLogon ( ) Password Expires ( ). , ADUC, « ». , .
ADLockouts
It is a simple program that tries to track down the source of invalid password attempts that resulted in Active Directory blocking.
This tool is great for small networks, but not as effective in a larger environment. The application searches each domain and domain controller for a failed login, and then analyzes all related events. Its purpose is to determine the reason for the blockage. After that, the program analyzes each machine and displays all typical cases of account locks for a number of objects: mapped drives, old remote sessions, scheduled tasks, and more.
PowerShell
Of course, you can take the most direct approach to investigating why Active Directory accounts are locked out and use PowerShell. This process can take a little longer and be more complex than the above tools, but it will also give you more detailed information about what exactly is happening on your systems.
Using PowerShell, you can easily filter the event log for account-specific events to determine the source of the account lockout:
- This can be done using the Get-EventLog cmdlet and the following command:
Get-EventLog -LogName Security | ?{{$_.message -like "*locked*USERNAME*"}} | fl -property *
- Get-UserLockoutStatus . , , , , .
If you're a network administrator, then you probably don't need to explain how much of a hassle it can be to block Active Directory accounts. With this in mind, it is tempting to simply treat account lockout as an integral feature of Active Directory and automatically unlock user accounts as soon as you receive a support request.
However, this is the wrong approach. By taking the time to investigate the root causes of account lockouts, you can prevent them from occurring frequently. In addition, changing blocking policies can be an effective way to identify when a user error is causing the blocking and when a cybercriminal attack on your network.
Ultimately, your understanding of Active Directory will determine how effectively you can prevent and manage account lockouts. If you are often frustrated by the inability to trace the source of these problems, you can use the resources we provide. In particular, check out our Guide to Users and Computers in Active Directory and our Guide to Labeling Sensitive Data to help you better protect your network from cyber attacks.