The basic idea here is to connect to a remote computer on a network and make all your network traffic look like local to that network.

The first reason someone might need it is to improve security and eliminate potential threats early. For example, you may need to print to a network printer without "exposing" this printer to the regular Internet. As a result, for example, someone can sit in a cafe and, having connected to the network via VPN, print documents on the printer, feeling as if he is at his desk, and the printer is standing a couple of meters from him. Using a VPN will also mean that the data transmitted over the cafe's WiFi network will be encrypted.
The second reason is to hide the user's real location from prying eyes. Let's say someone likes to watch BBC videos but lives in Ecuador. This means that in order for the videos not to be blocked for him, he will need to connect via VPN to a network located in the UK. If the authorities of a certain country monitor and censor the Internet, then the residents of this country can also benefit from the opportunity to disguise their traffic.
Using SSH to establish a VPN connection is fine for both of the above tasks. However, if you are mainly interested in the first of them, then you might be better off using a dedicated router or a small computer, like the Raspberry Pi, aimed at solving your problem. I must say that if you rent a server somewhere, then "VPN over SSH" is not for you.
Preliminary preparation

VPN
You only need root access to both machines. An SSH server must be installed on the remote computer. You will, of course, need an SSH client as well. Both local and remote machines will need to do some configuration. I use KDE, so I use NetworkManager to make the necessary settings, but you can go the other way. Using NetworkManager just makes things easier.
Some special settings need to be made on the server, but it is quite possible that they are already done on it. So, the file
/etc/ssh/sshd_config
must contain a line
PermitTunnel=yes
. In addition, you may need to set the value to a
yes
parameter
AllowTCPForwarding
. The firewall may also need some settings. However, the instructions for configuring the NetworkManager plugin may be useful even to those who do not use this program.
Client side settings
If you are using NetworkManager, then you need the appropriate plugin. For Neon and other Debian-based distributions, the package is fine
network-manager-ssh
. This is all you need. If you do not want to use NetworkManager, then you can use the following commands from the material of the plugin author:
ssh -f -v -o Tunnel=point-to-point -o ServerAliveInterval=10 -o TCPKeepAlive=yes -w 100:100 root@YOUR_SSH_SERVER \ '/sbin/ifconfig tun100 172.16.40.1 netmask 255.255.255.252 pointopoint 172.16.40.2' && \ /sbin/ifconfig tun100 172.16.40.2 netmask 255.255.255.252 pointopoint 172.16.40.1
This requires root access to both systems, since we are creating a tunnel. This, even when using the plugin, leads to several problems. Obviously, we would not like to be constantly prompted for a password for SSH connection and to verify the key. But if you manually configure the VPN, you can fix these problems.
Problems
Most modern systems do not allow you to log in as root using a password, and sometimes do not allow you to connect to the system in this mode at all. Therefore, we, first of all, need to solve this problem. In addition, when NetworkManager starts SSH, it looks for keys for the root user, not for the regular user. If he can't find something, he just stops. Therefore, we need to provide a seamless root login.
In order to provide the ability to root-login to the server, you need to edit the file
/etc/ssh/sshd_config
and set the parameter
PermitRootLogin
to
yes
... I recommend that you work in this mode for as long as it takes to complete the next steps of server configuration. Next, you will need to restart the sshd server, for example, with the following command:
systemctl restart sshd
You can also use this command:
/etc/init.d/ssh restart
Then, logging into the local machine using a regular account, you need to use
ssh-copy-id
to install the certificate on the host machine. After this is done, you need to return to the server and change the
/etc/ssh/sshd_config
value
PermitRootLogin
to
prohibit-password
. This will allow you to log into the server as root using a certificate, but not using a password.
If you've already logged in as root, you may have already been asked if you want to accept the server key. If this is not so, then we have a problem. If you can, please log in and answer yes to the corresponding question, after which the system will stop asking it. But, if this cannot be done, we can fix the problem by disabling
StrictHostKeyChecking
.
In theory, you can pass additional ssh options to the NetworkManager plugin, but for some reason this approach does not work with the version of the plugin from the repositories. If you don't use the plugin, doing everything manually, then you can make the necessary settings yourself. SSH settings for root user can be set in
/root/.ssh/config
. You can also set global settings in
/etc/ssh/ssh_config
.
If you change the global settings, then if the system supports it, consider using
/etc/ssh/ssh_config.d
. Thanks to this, you will be able to set parameters for a specific host, which will not be overwritten when the system is updated. For example, you can create a file in the appropriate directory with the name
hackaday.conf
:
Host *.hackaday.com hackaday.com StrictHostKeyChecking no Tunnel yes
Again, if you don't like the idea of verifying the host key, just log in once as root and manually accept the remote key. Or, if you're brave, manually edit
/root/.ssh/known_hosts
.
Connection
Everything should be ready to go now. If you are using the plugin for NetworkManager, you just need to establish a new connection. Namely, you need to go to the VPN connections section and select SSH.

Selecting the type of connection
Now you need to configure several parameters of the new connection. Including - you need to specify the certificate that you plan to use to log into the remote system.
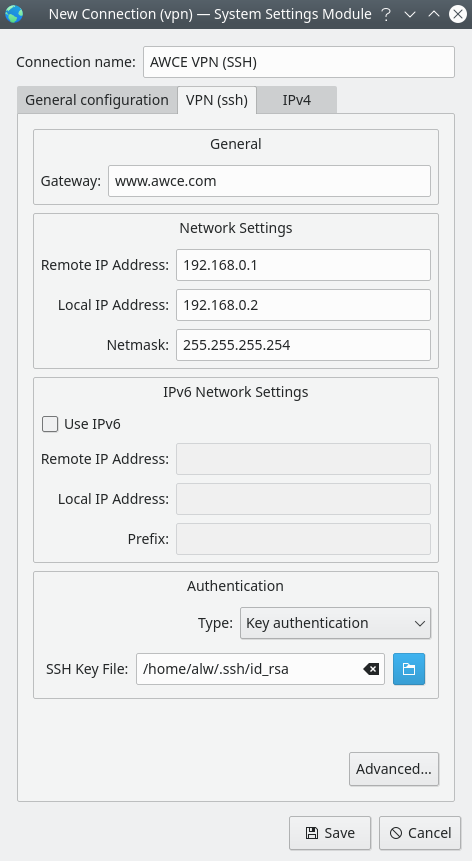
Setting up the connection
After saving the connection settings, this connection can be activated - just like any other network interface. If you want to test your new VPN - first, normally, ask for your IP address on the dedicated website . And then turn on the VPN and find out your address again. If you cannot establish a VPN connection, look in the system log for information about SSH errors.
Outcome
Of course, there are other VPN solutions as well. But it's almost guaranteed that the remote computer you are working with has an SSH server. Therefore, the proposed method for establishing a VPN connection via SSH is a simple and convenient solution that can be used without any preliminary preparation.
By the way, you can do a lot of interesting things with SSH . For example - to organize convenient work with files .
Do you use a VPN?

