Greetings to everyone who was brought here by the desire to learn about one of the protocols of quantum cryptography, since the possible appearance of a quantum computer in the near future will jeopardize many existing methods of cryptography.
At the moment, protocols have been proposed, a detailed analysis of which you can find on Habré, but I can recommend you an article with a pretty good overview: click here .
It is worth noting the distinctive feature of the AK-15 is the presence of authentication between legitimate users.
Introduction
The protocol in question, proposed by Khaled Elleyty and Abdulbast Abushgra in 2015, defines the interaction of our longtime friends Alice and Bob. Their communication will consist of several interconnected stages, and at some point, readers will be asked to parallelize due to the use of several different communication channels.
A small educational program:
EPR channel of entangled states
It is based on the Einstein-Podolsky-Rosen paradox. Here are some useful links:
First stage
To begin with, Alice has a plaintext that needs to be passed to Bob. It must first convert it to bit representation, and then to quantum bits ( qubits ):
→ → A, A -
, (DM)( ), , . ( ). , , . -PNS

DM, ( - , - ))
, . ( ), Ikubit, , (|×> |+>) .
- , .
-
4- -
Iepr :
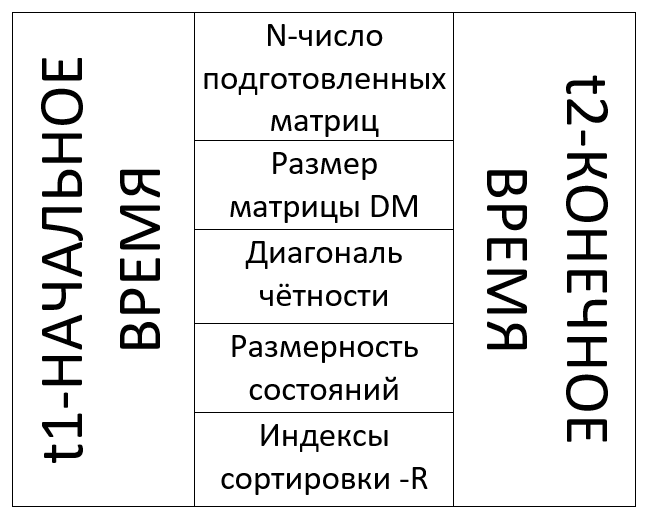
(t1,t2)- , , Iepr. N - ( ). DM, . p, , .S - , , . R - , .
:
-
, , - Iepr
,
.
, :
AC- , B- .
,
, , (00,01,10 11) ( ),
( Iepr), , . n- (SSK) n- , XOR. .
Iepr( ), Ikubit (|×> |+>) 4- ( ). ( ) . , Ikubit . QBERT( ), Iepr.
: Man-In-Middle(MIMA) The Intercept-Resend Attacks. .
:
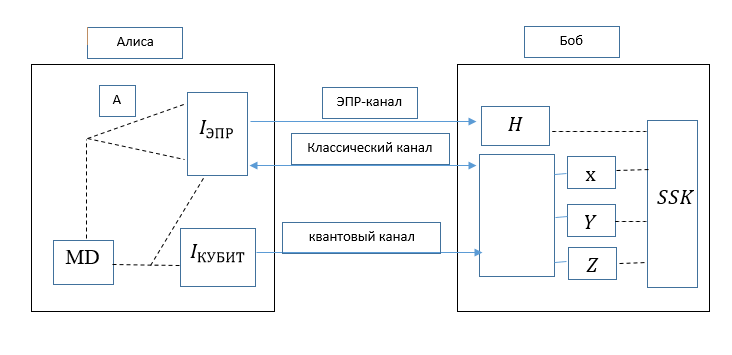
Alice and Bob first initiate EPR communication with entanglement exchange. If it succeeds, then both sides begin to exchange qubits to create a secret key. Having received the row I kubit , Bob builds the matrix, and using the row with R indices, he restores the correct DM. And it does the first investigation by inserting a parity string into a matrix, then counts each row to see if it's even parity. If there is an odd line, it must be checked for errors. If everything is successful, the n-qubit secret key (SSK) is generated.
Author's article