Further in the program

- Formulation of the knapsack problem (+ why a knapsack?)
- Easy and hard challenges
- Examples of
- History
What is public key encryption?
.
 : , .
: , .
, - !
- , , «», .
- . , , , .
 : , .
: , .
, - !
The first general public key algorithm used the knapsack algorithm.
Based on the definition of public key systems, it takes two keys to successfully encrypt (and decrypt) a message. The "legal" recipient of the message knows the secret keywhile the sender owns another public key ...
What to do if a public key becomes known to an attacker?
There is an answer: the public key must be obtained from the secret key using a transformation ( one-way function )with the following two properties:
- knowing A, it is easy to calculate the function itself
- , and it is difficult to calculate the inverse function

What is "easy" and "difficult"?
.
«» , . .. , — , — . , .
«» . , , .
.. , , , .
«» , . .. , — , — . , .
«» . , , .
.. , , , .
The knapsack problem is formulated as follows
The set (backpack vector) Is an ordered set of ( distinct natural numbers ... Let there be a number- whole and positive. The task is to find such a setso that in total they give exactly ...
In the most famous version of the knapsack problem, it is required to find out whether a given pair hasdecision. In the variant used in cryptography, you need for this inputbuild a solution knowing that such a solution exists. Both of these options are NP-complete.
Backpack analogy
In the simplest case denotes the size (capacity) of the backpack, and each of the numbers indicates the size (weight) of an item that can be packed into a backpack. The task is to find such a set of items so that the
backpack is completely filled.
Ie, imagine that you have a set of weights 1, 6, 8, 15 and 24, you need to pack a backpack with a weight of 30.
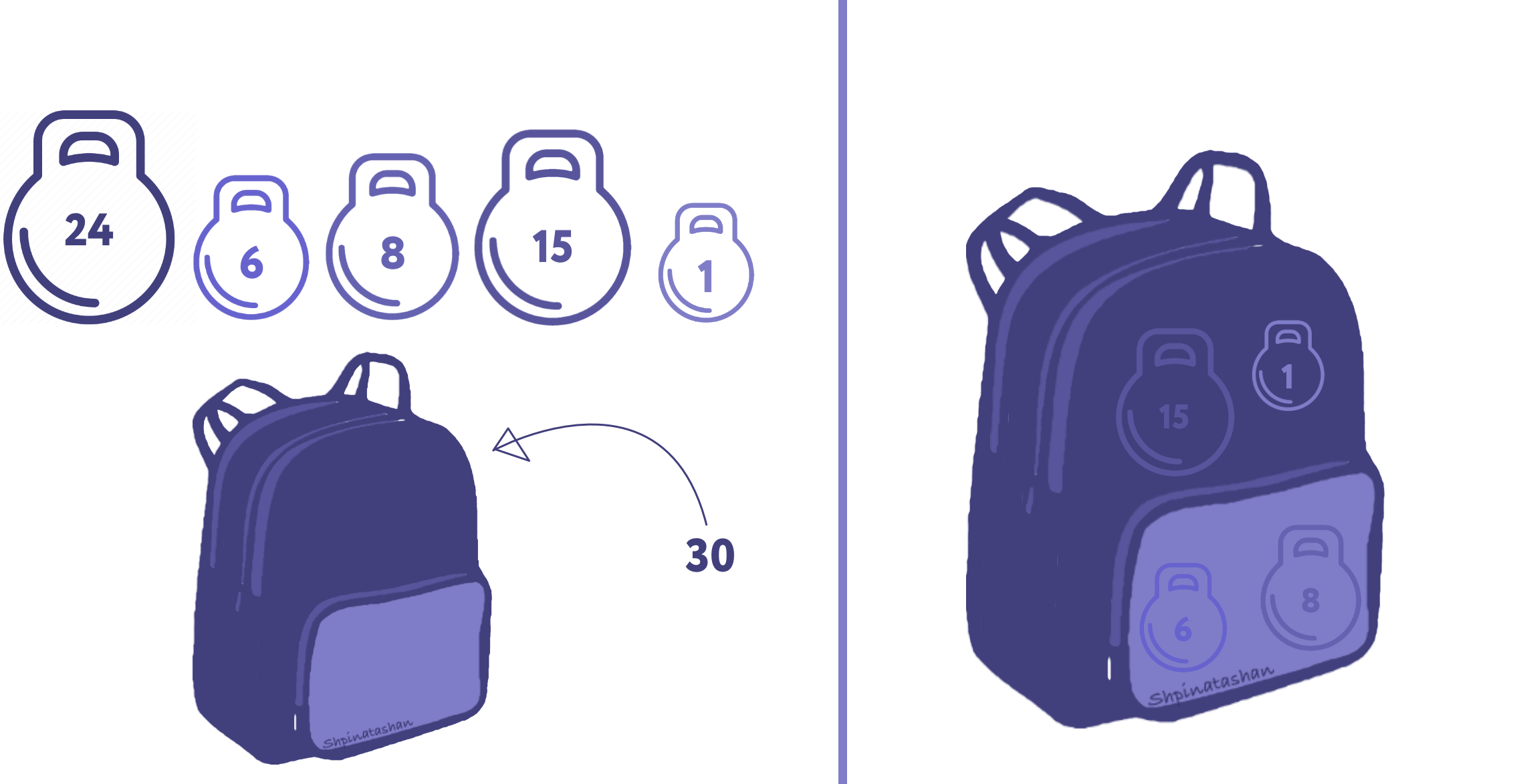
In principle, a solution can always be found by exhaustive search of subsets and checking which of their sums is ... In our case, this means brute forcesubsets (including the empty set). This is quite feasible.
But what if there are several hundred numbers?
In our example, n = 5 in order not to complicate the presentation. In real conditions, an example will have, say, 300... The point here is that no algorithms are known that have a significantly lower complexity compared to exhaustive search. Search amongsubsets cannot be processed. Indeed, the knapsack problem is known as NP-complete ... NP-complete problems are considered difficult to compute.
Does the function meet the specified requirements?
We define the functionin the following way. Any number can be given by a binary representation from bits, where leading zeros are added if necessary. Now let's define as a number obtained from summing up all such that the corresponding bit in binary notation equals 1.
That is,
Function was determined set ... Obviously, if we are able to compute of , then in practically the same time the knapsack problem will be solved: its binary representation is immediately computed, which in turn gives the components of the set included in the sum for ... On the other hand, the calculation of is lightweight. Since the knapsack problem is NP-complete,is a good candidate for a one-way function. Of course, one must demand that was big enough, say no less ...
Encryption
Plain text
(. plain text) — , , . ( ).
You can encrypt in two ways:
- The message cipher is obtained by raising the elements of this knapsack vector to the power of the corresponding bits of the encrypted message and then multiplying all the results, that is, if and the message , then the cipher will be the number ... This is a multiplicative way.
- The message cipher is obtained by multiplying the elements of this knapsack vector by the corresponding bits of the encrypted message and then summing up all the results, that is, if and the message , then the cipher will be the number ... This method is called additive .
Example
To encrypt plaintext in binary representation, it is split into blocks of length(for example, you can represent weight 30 with binary 11110). It is believed that one indicates the presence of an item in the backpack, and zero indicates its absence.
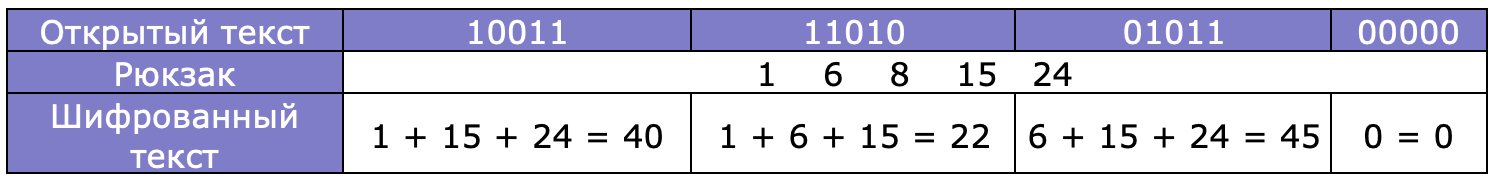
Backpack encryption provides a good approach to generating public and private keys, where the private key is easy to use and the public key is hard to figure out.
So, we can create a system where: the "hard" problem will serve as the
public key ; with it, you can easily encrypt and it is impossible to decrypt the message.
a private key - the "easy" problem will serve as using it, you can easily decrypt the message. Without the private key, you have to solve the "difficult" backpack problem.
"Easy" problem
Super growing backpack vector
, , . .
For super-growing vectors Α, the knapsack problem is easily solvable. Those. the backpack is easy to assemble.
Let's take an example:
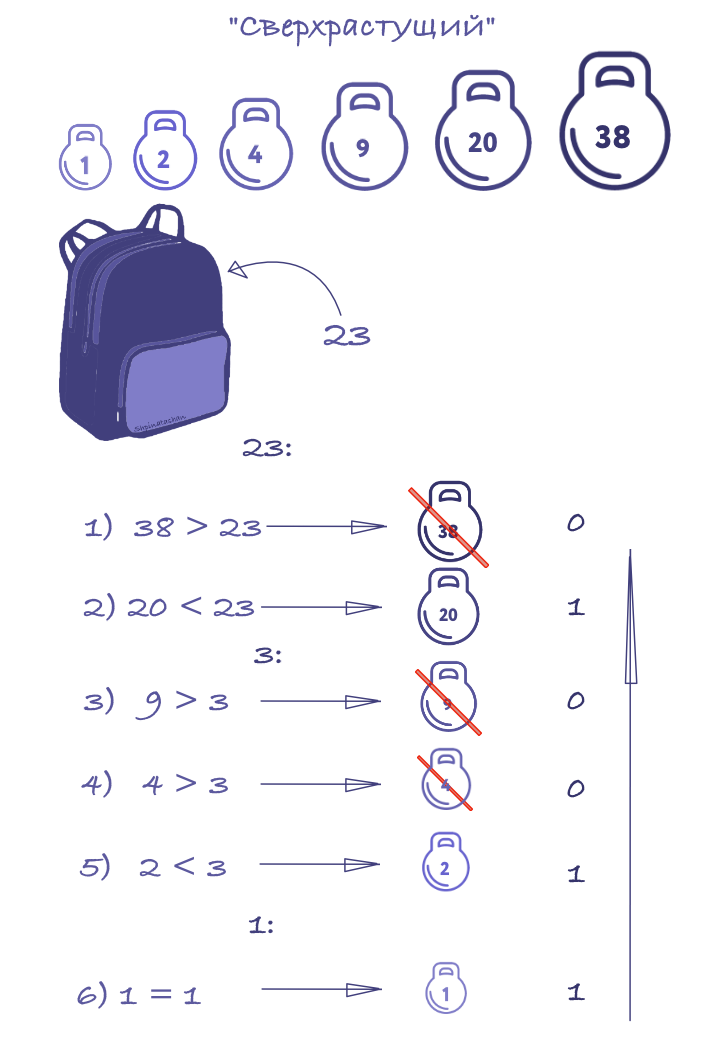
Algorithm
- .
, , . , . - .
- (1)-(2) .
, .
"Difficult" problem
It is much more difficult to decipher the problem of a non-oversized backpack.
One algorithm, which uses an oversized private key backpack and a non-oversized public key backpack, was created by Merkle and Hellman.
They did this by taking the oversized backpack task and transforming it into a non-oversizing task.
(Merkle and Hellman, using modular arithmetic, devised a way to transform a "light" backpack into a "hard" one)
Create a public key
Several important concepts
- ,
— , , [x/m] — ,
-
, , .
, , , , B A m t , , .
, ,
. ,
.
-
, , .
- — , , , .
The creator of the cryptosystem chooses such a system that vector is super-growing, and comes from strong modular multiplication with respect to ... Vector expanded as encryption key and binary blocks of length sent to the designer as numbers obtained using the vector ...
The message interceptor must solve the knapsack problem to enter... The creator of the cryptosystem calculates
and solves the backpack entry problem ... Why all this works is
shown in the following lemma.
Lemma . Let's pretend thatsuper growing vector and vector derived from strong modular multiplication with respect to ... Suppose further that, - an arbitrary natural number and ... Then the following statements are true.
(i) The knapsack problemsolvable in linear time. If a solution exists, then it is unique.
(ii) The knapsack problemhas at most one solution.
(iii) If there is a solution to enterthen it matches the only entry solution ...
proof (p. 104)
Example
Consider a super-growing sequence; for example, {1, 2, 4, 10, 20, 40}. The modulus must be greater than the sum of all numbers in the sequence, for example 110. The multiplier must not have common divisors with the modulus. So let's pick 31.
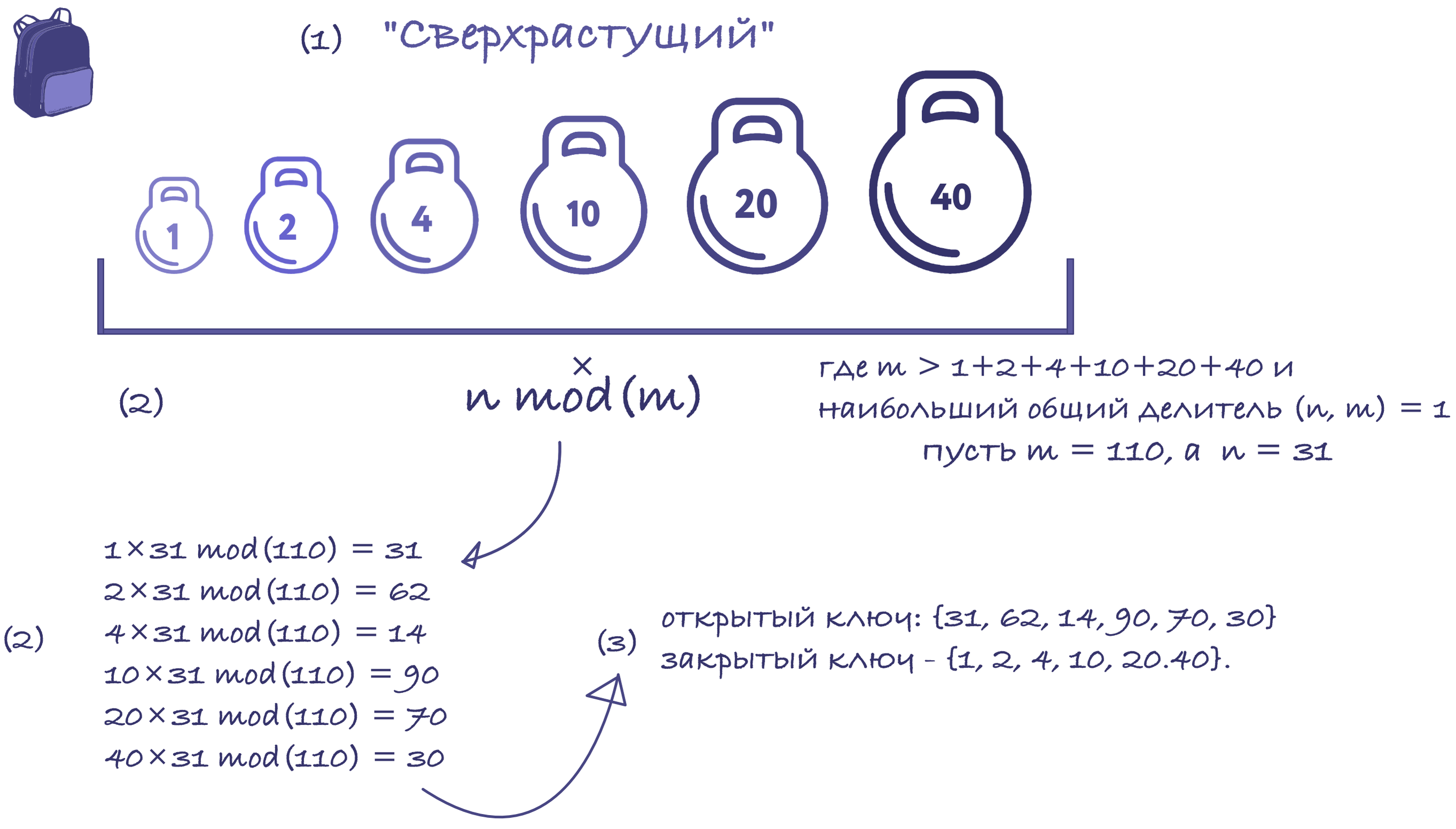
So, we calculated the public key: {31, 62, 14, 90, 70, 30} and the private key - {1, 2, 4, 10, 20.40}.
Now let's try to send a binary sequence: 100100111100101110
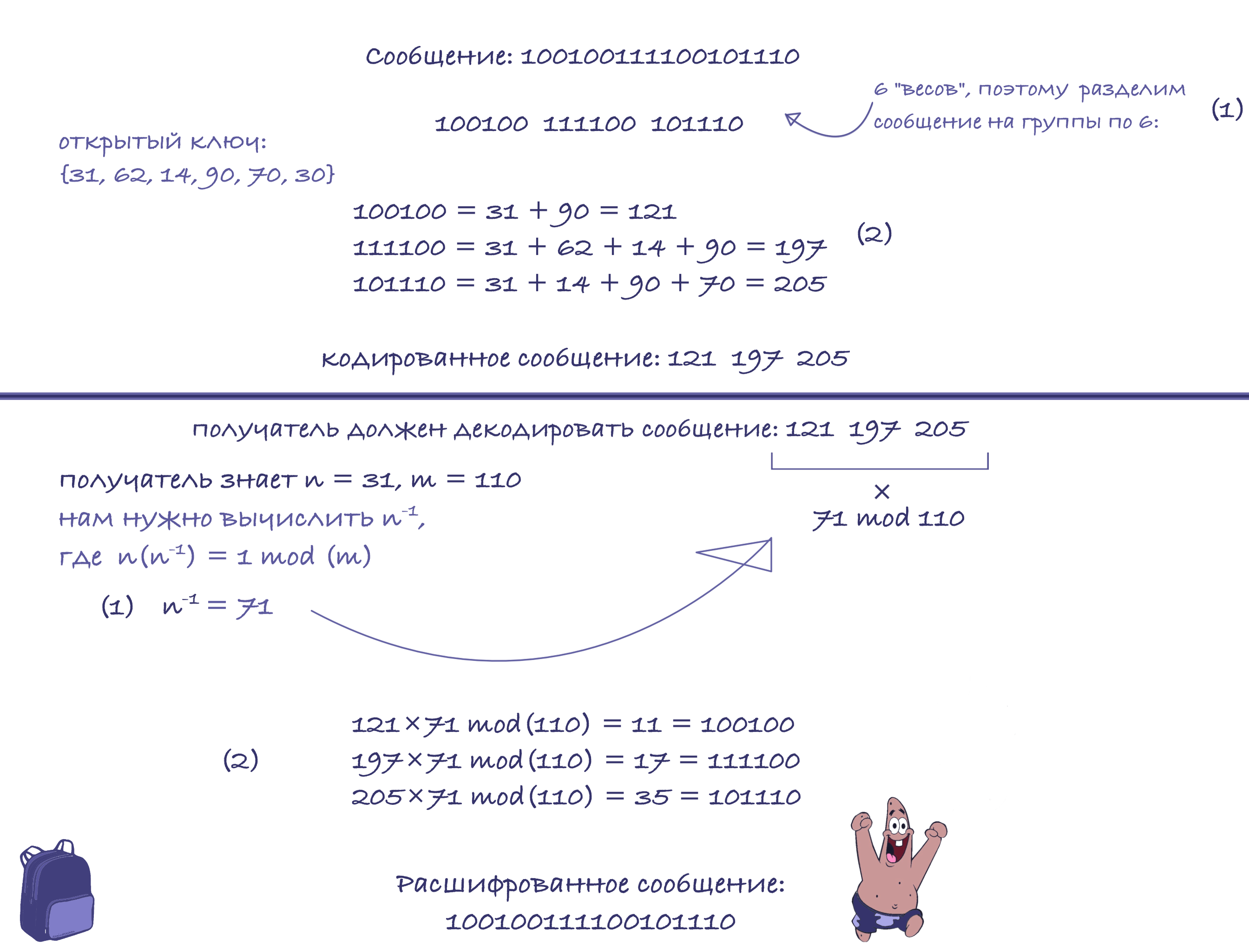
Some of the benefits of public keys
- When using a public key cryptosystem, both parties do not meet, they may not even know each other and use any kind of communication.
- Key length. In symmetric cryptography, if the key is longer than the original message, no real gain is achieved. As for public key cryptosystems, the length of the encryption key does not matter, since it is public and public. Therefore, the length of the decryption key is not so important (the recipient only stores it in a secret place)
History
 For a long time, backpack cryptosystems were considered as the most attractive and promising cryptosystems due to their NP-completeness and high encryption and decryption speed. Many schemes use the knapsack problem (in various variations), here are just a few of them: the compact knapsack problem, the multiplicative knapsack problem, the modular knapsack problem, the matrixcover problem, the group factorization problem ...
For a long time, backpack cryptosystems were considered as the most attractive and promising cryptosystems due to their NP-completeness and high encryption and decryption speed. Many schemes use the knapsack problem (in various variations), here are just a few of them: the compact knapsack problem, the multiplicative knapsack problem, the modular knapsack problem, the matrixcover problem, the group factorization problem ...
 Unfortunately, most of them are vulnerable to attacks. It turned out that it is not trivial to design a secure cryptosystem based on the knapsack problem, although the problem is known as NP-complete. Most knapsack cryptosystems have been hacked. Despite this, in contrast to integer factorization and discrete logarithm, the general knapsack (solution) problem is a proven NP-complete problem.
Unfortunately, most of them are vulnerable to attacks. It turned out that it is not trivial to design a secure cryptosystem based on the knapsack problem, although the problem is known as NP-complete. Most knapsack cryptosystems have been hacked. Despite this, in contrast to integer factorization and discrete logarithm, the general knapsack (solution) problem is a proven NP-complete problem.
Some people think that one day a polynomial-time algorithm could be invented to solve integer factorization and discrete logarithm problems, while the knapsack problem is still NP-complete.
There are several "BUTs" here.
First, NP-completeness is based on worst-case analysis; second, NP-completeness is a characteristic of a general problem, not a specific case. This means that if we consider the average complexity, the knapsack problem can be easy.
The material was prepared on the basis of this literature:
(1) A. Salomaa. Public-Key Cryptography. - Springer-Verlag, 1990. - p. 75-82, pp. 101-111
(2)Min Kin Lai. Knapsack Cryptosystems : Past and Future - University of California, 2001
(3) Baocang Wang, Qianhong Wu, Yupu Hu. A knapsack-based probabilistic encryption scheme. 2007
(4) - (5)