Recently it became known that three large chip manufacturers at once: Intel, AMD and Qualcomm, are planning to embed a new Pluton security chip in their processors. It was developed jointly with Microsoft and will replace the current TPM in the future. In any case, manufacturers spoke about such prospects.
As for Pluton, this chip is based on technologies that Microsoft has developed to protect its Xbox One game console. The goal pursued by Microsoft is to prevent pirates from hacking the game console and to prevent pirated games from being launched.
What kind of chip is this?
Mirosoft talked about it in detail on its blog a day ago .
Today, the security of the operating system on most PCs depends on a chip called the Trusted Platform Module (TPM). It is a processor independent element. It stores keys and OS integrity data. Windows has been working with TPM for over 10 years, technologies such as Windows Hello and BitLocker directly depend on this chip.
Everything would be fine, but cybercriminals are finding more and more opportunities for successfully breaking TPM-based protection. Hacking technologies are becoming more complex, their goal is a communication channel between a processor and a chip. Usually it is a tire that is vulnerable to spoofing or interceptiondata transmitted over it. Here the main problem is just the autonomy of the TPM chip and its remoteness from the central processor.
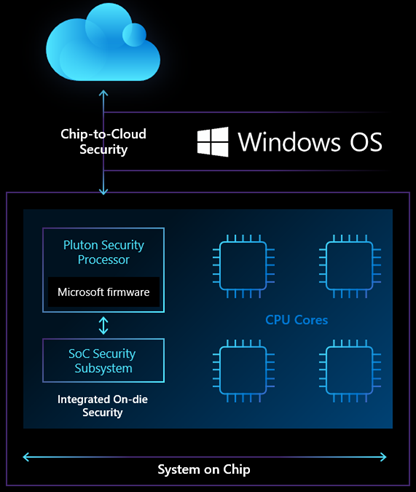
Pluton will radically change the situation towards strengthening protection. Firstly, this chip will be integrated into the processor architecture, and secondly, it will be able to simulate TPM, completely replacing the Trusted Platform Module technology. By the way, TPM emulation makes it possible to maintain compatibility of current technologies with each other, including all existing TPM specifications and APIs.
A Microsoft blog has announced that Pluton will store personal data, encryption keys, user IDs, etc. According to Microsoft representatives, it is impossible to somehow remove this data from the chip, even if the attacker has physical access to the PC. Pluton receivednew technology Secure Hardware Cryptography Key (SHACK), which makes it possible to ensure that encryption keys are never removed from the chip.
As a result, entire classes of attack vectors are blocked. It is about repelling physical attacks while preventing theft of credentials and encryption keys. It also provides the ability to control the software and hardware. Pluton will also help maintain the integrity of the system, since there will be much less room for changing some components.
Where did Pluton come from?
According to company representatives, a similar protection system was used in the Xbox One, where it was tested for several years. The console hardware developers gradually refined the technology so that it eventually "grew" out of a purely console division.
Pluton is now able to defend not only against known attacks, but also prevent attacks based on 0-day vulnerabilities. It is also compatible with Bitlocker encryption and Windows Hello authentication. Yes, so far the developers only declare about the Windows OS - what will happen to other OS installed on systems with a chip, Microsoft representatives have not yet explained.
How to update the chip firmware?
The question is quite logical, because if this chip becomes a part of the processor architecture, then how to update its firmware? As it turned out, everything is simple, the update will be carried out through the cloud - as far as you can understand, together with Windows updates.
This update principle makes it possible to always keep the firmware up to date, however, only if it is connected to the network, this is one, and two - provided that the updates themselves are not blocked. Many PC users block Windows and application updates, wanting to control their PC and OS themselves.
When will Pluton technology roll out?
It's not clear yet. But the fact that it will begin soon is absolutely certain. AMD, Qualcomm and other processor manufacturers have confirmed they will integrate Pluton into their chip architecture. In the future, Linux support will also appear, which the developers have announced separately. However, when exactly and how it will work is also unclear. But Microsoft already uses some Linux-based products on their systems, where Pluton also runs.
It turns out that everything is fine, computers will become overprotected?
In general, the level of protection of the user's personal data should really improve. In addition, the range of attack methods available to cybercriminals will be narrowed. This is the positive side.
There is also a fly in the ointment. Thus, Pluton is ideally suited to protect DRM as well, taking this technology to a height unattainable before. Since the processors will directly request updates from the servers, then the data on hardware and software can be checked against a central database.
And if something is changed, then certain functions of the PC can be blocked. Protection of licensed software and content is also moving to a new level. The same activation of Windows using specialized software will become impossible. Likewise, the computer will be able to check the license for the content being played.
True, David Weston, director of corporate OS security at Microsoft, said Pluton was created solely to improve the security of user data, and not to protect digital content.
Few analogies
A similar story happened with Apple two years ago. Then the company added the T2 chip, integrating it into the latest models of branded laptops. True, it was not integrated with the central processor, but there were many problems associated with it.
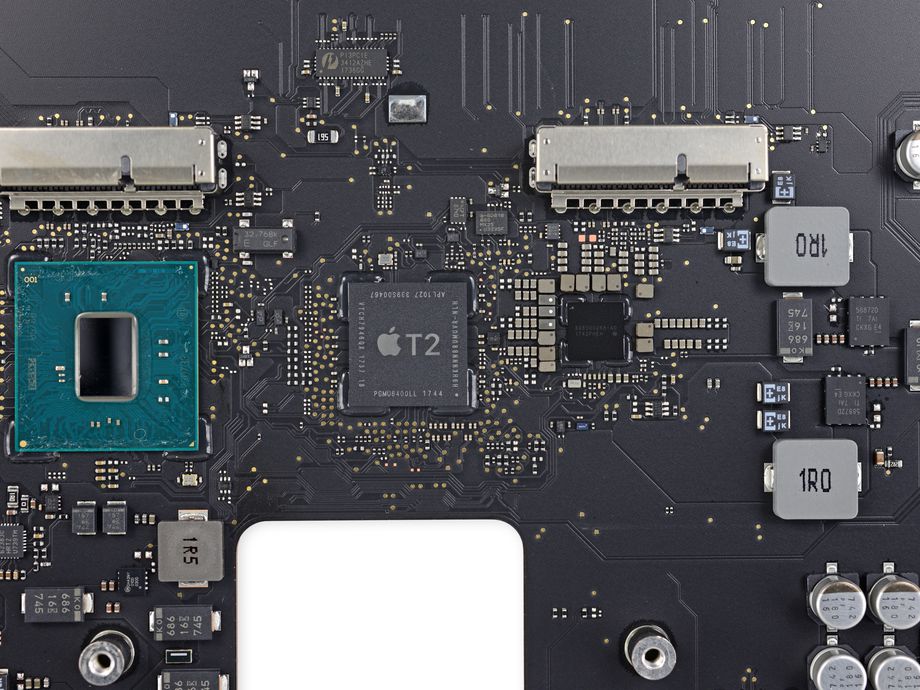
The good news is that the chip does a really good job at protecting users' personal data. It also disabled the laptop's microphone in hardware if the laptop's lid was closed.
But the same chip blocked the possibility of repairing devices with it by unauthorized service centers and ordinary users. So supporters of the "right to repair" once again found themselves in a difficult position.
As for the chip from Microsoft, it is now unclear whether the company will use such opportunities itself, provide this opportunity to partners, or will not do anything. In general, you can imagine the moment when a laptop with an inauthentic RAM bar declares the need to purchase RAM from the manufacturer. But now we can only guess about this, in order to find out more about all this, we will have to wait.
